Watering Hole Attack Targeted Florida Water Utilities
Cybercrime
,
Fraud Management & Cybercrime
,
Next-Generation Technologies & Secure Development
Dragos: Oldsmar City Employee Visited Rigged Site, But There’s No Connection to Incident

Investigators at industrial cybersecurity specialist Dragos say an employee of the water treatment plant in Oldsmar, Florida, where a cyberattack was thwarted, had visited an infected website the same day, but that apparently played no role in the security incident.
See Also: Top 50 Security Threats
The city worker visited the infected website, which belongs to a general contractor in Florida that services the water and waste industries, writes Kent Backman, an adversary hunter at Dragos. The visit occurred on Feb. 5, the same day that an attacker attempted to increase the levels of lye that would be added to the city’s water, an action that was spotted and stopped (see: Hacker Breached Florida City’s Water Treatment System).
“This malicious code used [in the watering hole-style attack] seemingly targeted water utilities, particularly in Florida, and more importantly, was visited by a browser from the city of Oldsmar on the same day of the poisoning event,” Backman writes.
The intrusion at the Oldsmar plant set off fresh concerns about the potential for tampering with industrial control systems in critical infrastructure. In another recent critical infrastructure incident, a ransomware attack against Colonial Pipeline Co. led the the company to temporarily shut down its critical fuel-delivery pipeline, triggering fuel shortages (see: Colonial Pipeline Attack Leads to Calls for Cyber Regs).
At Oldsmar, the attacker gained access to a human-machine interface via an account for TeamViewer, remote access software used by plant employees. The intruder increased the level of lye, or sodium hydroxide, that was to be added to the water from 100 parts per million to 11,100 parts per million. But an operator noticed someone was in the system, and officials took immediate steps to restrict remote access, thwarting the attack.
An advisory issued by Massachusetts for its own water treatment plants included other details about the Oldsmar facility’s systems. All of its computers, which ran 32-bit versions of Windows 7, were connected to the supervisory control and data acquisition, or SCADA, controls, the advisory states. Also, all computers shared the same password for remote access.
Link to Tofsee Botnet?
Even though the watering hole site didn’t appear to be related to the attempted tampering with lye levels in Oldsmar, Dragos decided to write up the finding to demonstrate that coincidental activity doesn’t mean causal activity. Backman writes that Dragos issued an advisory alert about its finding on Feb. 17 and reported it to the Department of Homeland Security.
“The purpose behind this investigative anecdote on the ‘water watering hole’ is educational and highlights how sometimes two intrusions just don’t line up together no matter how much coincidence there is,” Backman writes.
The infected general contractor’s site, which Dragos didn’t identify, didn’t deliver exploit code to visitors’ computers as is often done in a watering hole attack. Instead, the malicious code was a fingerprinting script that collected 100 bits of information, such as OS, CPU, browser, language and more. It also collected browser cipher fingerprint hashes.
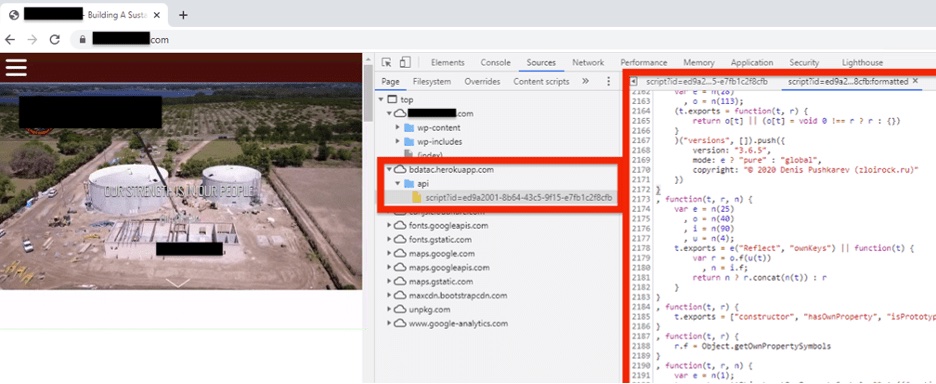
The contractor’s website ran WordPress and was using several vulnerable plug-ins, which may have led to the compromise, Backman writes.
Dragos found that another website had been infected with the same fingerprinting code on the same day – Dec. 20, 2020 – that the contractor’s website was infected. That website, called the DarkTeam Store, is now offline, but Backman writes that it “claims to be a dark market that supplies thousands of customers with gift cards and accounts.”
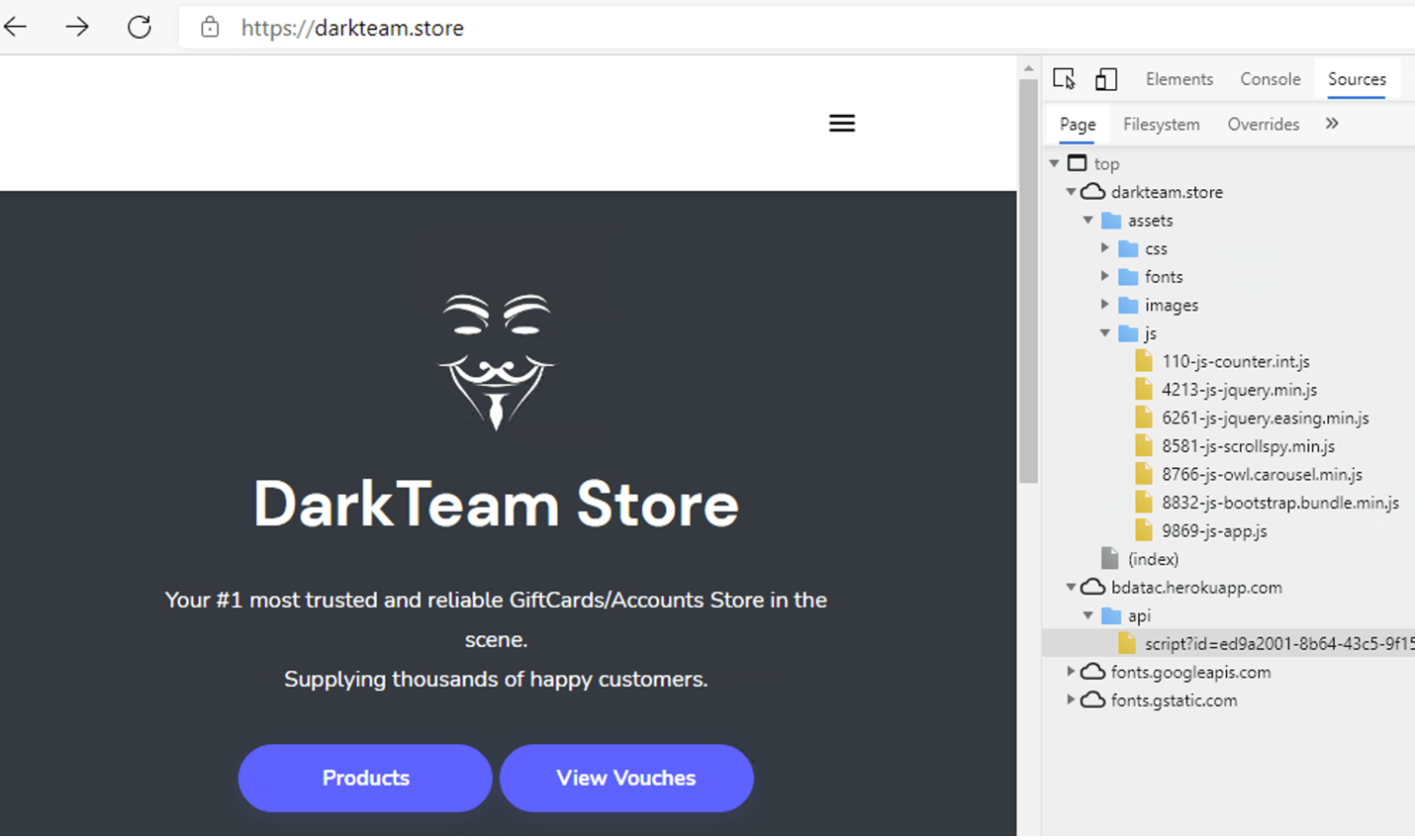
The DarkTeam Store website also seemed be connected to a type of botnet code called Tofsee. Backman writes that Dragos saw 12,735 IP addresses check in with a password-protected page within the domain.
The aim of all the activity is unclear. But Backman writes that the best guess is that the threat actor was collecting the data in an attempt to improve the ability of the botnet code to impersonate legitimate web browser activity.
“We do not understand why the adversary chose this specific Florida water construction company site to compromise and to host their code,” Backman writes.