Researchers Uncover Another DarkSide Ransomware Variant
Fraud Management & Cybercrime
,
Ransomware
FortiGuard Labs Describes Variant, Which Is No Longer Active
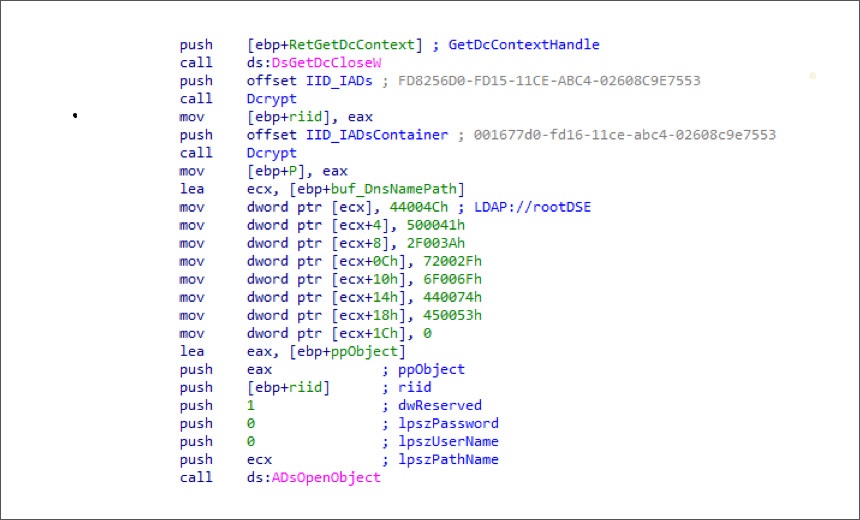
Security researchers at FortiGuard Labs have uncovered another DarkSide ransomware variant with destructive capabilities that enabled attackers to seek disk partition information and encrypt the files in multiple disks. But the researchers say the variant is “unrelated to the Colonial Pipeline campaign” and no longer active.
The DarkSide gang announced on May 13 that it was shutting down its ransomware-as-a-service operation. Another DarkSide malware variant was used against Colonial Pipeline Co., which led to the temporary shutdown of the company’s pipeline serving much of the East Coast (see: DarkSide Ransomware Gang Says It Has Shut Down).
FortiGuard Labs says the recently identified DarkSide malware variant was found in a sample provided by “trusted partners.” It had been used in an attack campaign designed to enable attackers to cause wider disruption.
“This DarkSide variant seeks out partitions on a multi-boot system to find additional files to encrypt, thereby causing greater damage and an increased incentive to pay a ransom to recover files,” FortiGuard researchers note.
Malware Analysis
The newly discovered DarkSide malware variant was efficiently compiled with minimum file size and ability to deliver large payload, FortiGuard researchers say. The malware began its operation by locating a domain controller used for security authentication requests. The malware then looked for Active Directory, the centralized domain manager in Microsoft Windows systems.
Because authentication is required to access the Active Directory, the malware used Lightweight Directory Access Protocol, an open-source tool, to authenticate anonymously, the report notes.
“After issuing Active Directory queries, the ransomware then attempts to encrypt files in network shares found in this section of the code,” according to the researchers’ report. “It seems that DarkSide avoids certain queries as it might not be running in the context of an administrator and attempts to access them could potentially trigger an alert.”
The DarkSide variant then scanned the hard drive to check if it is a multi-boot system in order to find additional partitions and try to encrypt files in network shares, FortiGuard researchers note.
“After the malware finds a targeted drive type, it checks the version of Windows it is running on. For systems running Windows 7 and above, the malware looks for volumes with a bootmgr file in it,” the report notes. “For systems older than Windows 7, DarkSide chooses a different approach.
This included calling an API to retrieve additional information about the type, size and nature of a disk partition. If the partition style was identified, the malware then encrypted the files within the drives, the report says.
Researchers note that the technique used to identify the partition locator and customization based on the victims’ operating systems was also deployed in the NotPetya malware outbreak that affected organizations worldwide. Unlike NotPetya, which left the infected systems unusable, the newly discovered DarkSide variant left the systems in a semi-recoverable state, according to the report.
DarkSide C&C Servers
When analyzing the IP address of the command-and-control server associated with the new variant, the researchers determined that it was co-located in the U.S. and the Netherlands on the servers of KingServers.
“B.V. KingServers has been classified as a bulletproof host by the infosec community, and although based in the Netherlands, it has ties to Russia, where DarkSide is located,” FortiGuard researchers note. “Specifically, its hosting service was used in several notable attacks, such as attacks on an India-based IT outsourcing firm to perpetrate gift card fraud, as well as for the 2016 Democratic National Committee attacks in the U.S.
DarkSide Advisory Update
On Wednesday, the Cybersecurity and Infrastructure Security Agency and the FBI updated their joint cybersecurity avisory on indicators of compromise to help network defenders find and mitigate activity associated with DarkSide ransomware.






