Senators Grill Cybersecurity Execs on SolarWinds Attack
3rd Party Risk Management
,
Breach Notification
,
Critical Infrastructure Security
FireEye, Microsoft, CrowdStrike Offer New Details and Recommendations
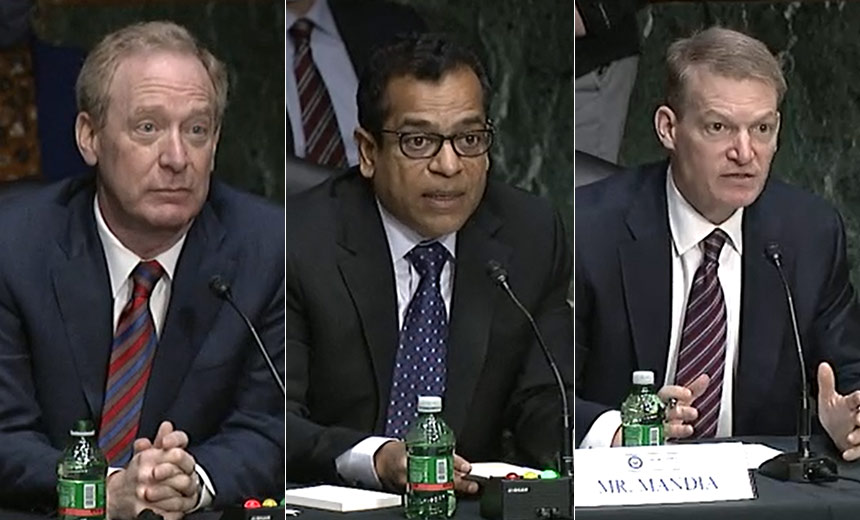
The CEOs of SolarWinds, Microsoft, FireEye and CrowdStrike rolled out a series of cybersecurity recommendations to a U.S. Senate panel Tuesday while detailing how foreign actors gained access to their firms’ systems as a result of the SolarWinds supply chain attack.
See Also: The Guide to Just-In-Time Privileged Access Management
The details that emerged from the testimony given before the U.S. Senate Select Committee on Intelligence revealed the attack was part of a multidecade effort on the part of a nation-state attacker, most likely Russia. It was estimated a team of 1,000 people was involved in pulling off the operation, which included a dry run in October 2019 against some of those attacked to ensure the plan would work when executed, the witnesses said.
The executives stressed the need to create a centralized agency within the federal government to handle attack reports and share intelligence, require private and public sector organizations to promptly issue a notification of a cyber incident, develop a deterrent to make a potential attacker think twice before acting, and create international standards that would outlaw cyber strikes on certain assets such as healthcare and elections.
Committee Chairman Mark Warner, D-Va., and Marco Rubio, R-Fla., vice-chair, called FireEye CEO Kevin Mandia, SolarWinds CEO Sudhakar Ramakrishna, Microsoft President Brad Smith and CrowdStrike CEO George Kurtz to testify. This was the second congressional hearing on the SolarWinds cyber incident. The first hearing was held behind closed doors on Jan. 6, but it was interrupted by the Capitol Hill riot.

All four executives helm companies that were struck by the nation-state actor behind the attack, and each shared their latest insights. These included the attack’s known scope, attribution, what the attackers did once inside their system and the effort that was put into gaining access by the attacker.
The last point was raised by several committee members who were curious about what it took to pull off the intrusion that resulted in 100 companies and nine federal agencies being breached.
Microsoft’s Smith said the attacking entity likely had 1,000 people working together to implement the attack and the operation is the biggest planned attack he has seen – points he recently noted on the CBS TV program “60 Minutes.”
“I can’t think of a similar operation that we have seen that would have a similar human scale,” Smith told the committee. “It’s the largest and most sophisticated operation of this sort that we’ve seen.”
Warner had several questions for the cybersecurity executives, including about the progress made to date in expelling the hackers and preventing such an incident from happening again. He was also interested in their opinion on their experience working with the federal government, specifically the Unified Coordination Group, to help mitigate this issue.
The Initial Attack
FireEye’s Mandia gave a detailed look at how the nation-state actor behaved once access was gained. In broad strokes, he said the attackers were fast, accurate, knew exactly what they wanted before they were inside and had prepared the battlefield to ensure success.
“They did a dry run in October 2019, put innocuous code into SolarWinds, just to make sure the results of their intrusion was making it into a SolarWinds platform production environment,” Mandia said.
The FireEye attack became public on Dec. 8, when the company reported some penetration testing tools had been removed from its system. Mandia said the attackers had entered the system several months earlier.
“The very first thing they did is went for your keys, your tokens. They stole your identity architecture, so they could access your network the same way your people did it. And that’s why this attack was hard to find these attackers from day one. They had a backdoor.”
This also helped ensure persistence in the systems, he said.
A Call for Notification Legislation
Microsoft’s Smith expressed anger that there is no federal requirement for private entities to share intelligence or even inform the government that they have been victimized. Only state laws spell out breach notification requirements.
When asked by the committee if any of the security companies present were under a federal legal obligation to reveal what happened, all replied no, but they said they had done so anyway out of a moral duty to the industry and the country.
“It is time not only to talk about but to find a way to take action to impose in an appropriate matter some kind of notification obligation on entities in the private sector,” Smith said, and the other CEOs agreed.
Centralized Reporting
Another recommendation made by the witnesses was the creation of a centralized reporting agency within the federal government. The executives all noted the current system of having to notify individual departments of a problem wastes time at a period when action must immediately be taken to protect the country.
“I still believe it is critical we find a way to have a centralized agency that we can report threat intelligence to confidentially, and that if you’re designated as a first responder in cyberspace whether private or public sector you report to that agency,” Kurtz told the committee.
This would enable the intelligence to be placed into the hands of those who can quickly take actionable steps, he added.
Attribution
Investigators have said that a group backed by the Russian government was behind the cyberespionage operation, but Sen. Rubio directly asked Smith, Kurtz and Mandia if Russia was the culprit.
Mandia said the forensics indicated the attack was not consistent with those used by China, North Korea or Iran, but most consistent with Russia. CrowdStrike’s Kurtz said he could neither “confirm nor deny” that it was Russia.
Risk and Response
Mandia, Smith and Kurtz all noted there is currently no regulation on the books that spells out the government can respond to an attacker – and Sen. Warner agreed.
Along similar lines, Warner asked whether international standards or norms need to be negotiated with other countries and put in place as they are for other forms of conflict.
“We don’t bomb ambulances in war. Should we, therefore, consider efforts to subvert patching, which after all is about fixing vulnerabilities, to be similarly off-limits?” Warner asked during his opening remarks.
Mandia noted: “Attribution is critical. You know, anytime I get to advise a head of state, it’s very simple. If you don’t know who did it, you can’t do anything about it. So I would argue that one of the most critical issues we have to start to solve as a nation is: We’ve got to know who did every breach.”
Executive Action to Come
Last, week, Deputy National Security Adviser Anne Neuberger said the Biden administration is preparing “executive action” to address security shortcomings that have come to light as a result of the SolarWinds supply chain attack.
“We’re working on close to about a dozen things – likely eight will pass – that will be part of an upcoming executive action to address the gaps we’ve identified in our review of this incident,” Neuberger said.
Investigators believe that nine federal agencies, as well as 100 private sector organizations, were compromised as part of the attack, Neuberger said.
The supply chain attack was launched when hackers planted a backdoor known as “Sunburst” within an update for SolarWinds’ Orion network monitoring platform. Then, 18,000 of the company’s customers downloaded the update, and some of those were further targeted for follow-on attacks.
Neuberger also noted that it will take several months to fully expel malicious code from the networks targeted by the hackers.