Saudi Aramco Traces Data Leak to Attack on Supplier
Fraud Management & Cybercrime
,
Incident & Breach Response
,
Ransomware
Extortionists Demand $50 Million – Payable in Monero Cryptocurrency – From Oil Giant

Saudi Aramco, one of the world’s largest oil and natural gas firms, has confirmed that corporate data was leaked after attackers breached one of its suppliers.
See Also: Why You Should Take Security to the Cloud
A spokesperson tells Information Security Media Group that Saudi Aramco’s internal IT systems were not affected, and that its oil and gas operations continue to function normally. The company says its leak investigation is ongoing.
“Aramco recently became aware of the indirect release of a limited amount of company data which was held by third-party contractors,” the spokesperson says. “We confirm that the release of data was not due to a breach of our systems, has no impact on our operations and the company continues to maintain a robust cybersecurity posture.”
Saudi Aramco, also known as Saudi Arabian Oil Company, did not identify the supplier that was breached or describe the nature of the intrusion.
The oil company, which has more than 66,000 employees, had nearly $230 billion in revenue in 2020, with a net income of $49 billion, according to its latest annual report.
Reported Extortion Plot
The cyberattackers who targeted Saudi Aramco’s supplier claim to have stolen 1TB of corporate data. They are demanding a payment of $50 million in the monero cryptocurrency, according to a website they created just for the extortion attempt. That site, like most ransomware extortion sites, is hosted on the anonymizing Tor network, which makes it difficult to trace whoever created it.
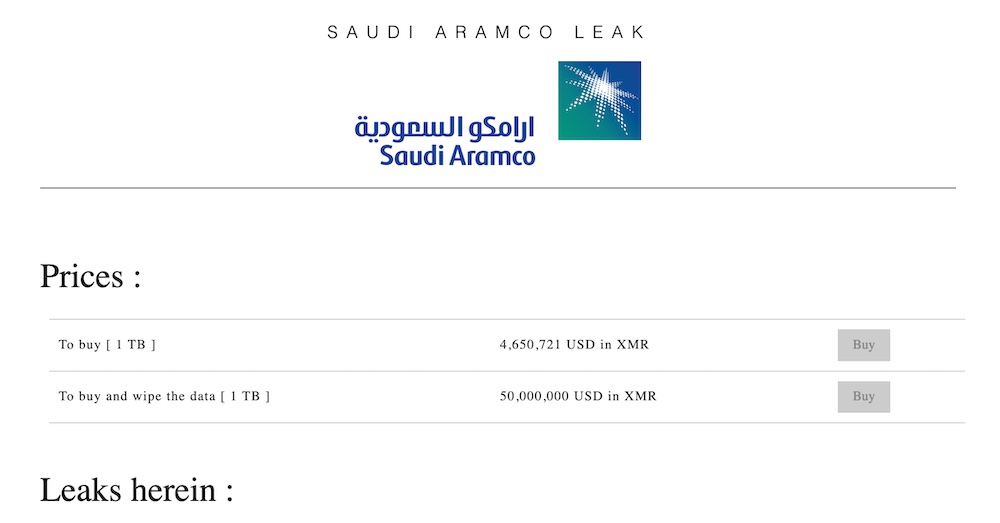
The person or group that obtained the data goes by the nickname “Zerox296” and claims the data was taken after a zero-day vulnerability in a cloud storage platform was exploited. No evidence to support this claim, however, has been produced.
About a week ago, ISMG initiated contact with Zerox296 but was unable to learn more about the leaked data or the way it was obtained.
Earlier, Zerox296 also posted an advertisement for the data on a well-known data leak forum. Zerox296 claimed the data included information about 14,000 employees, such as passport details, phone numbers and ID numbers. The data also purportedly contains invoices, contracts, client data and documentation about Saudi Aramco’s network.
The incident demonstrates that too many organizations continue to experience security weaknesses in their supply chains – especially when it comes to third parties and other subcontractors, says John Dickson, vice president at security consulting firm Coalfire.
“Many subcontractors are granted carte blanche access to client facilities and networks and not treated as the third parties that they are,” Dickson says. “Sophisticated organizations apply the same rigorous vetting to subcontractors as they do for employees and monitor their behaviors as if they were full-time staff. Saudi Aramco serves as another business case for the tight monitoring of subcontractors.”
Previous Security Problems
Saudi Aramco has sustained other attacks over the years. In 2012, the company was hit with wiper malware known as Shamoon, which disabled tens of thousands of the firm’s workstations and forced the company to shut down large portions of its IT networks. As part of its recovery, the company was forced to replace extensive amounts of hardware, and it purchased 50,000 new hard drives.
Security researchers and the U.S. government have long believed that Iran deployed Shamoon against the Saudi Arabian company (see: Suspected Iranian Group Wages Wiper Attacks on Israel).
In 2019 and 2020, the U.S. Cybersecurity and Infrastructure Security Agency warned U.S. companies about possible Iranian-linked attacks that could use the Shamoon wiper malware (see: DHS: Conflict With Iran Could Spur ‘Wiper’ Attacks).
Under Attack: Oil and Gas Sector
Other companies in the oil and gas sector have recently been targeted by ransomware gangs looking to extort them for millions.
In May, Colonial Pipeline Co. sustained a ransomware attack that led it to shut down its pipeline serving large portions of the U.S. East Coast. The company paid a $4.4 million ransom to a Russian-speaking ransomware operation called DarkSide, although the FBI eventually recovered $2.3 million of that payment by gaining access to a cryptocurrency wallet associated with the attackers (see: How Did FBI Recover Colonial Pipeline’s DarkSide Bitcoins?).
The Colonial Pipeline attack was one of several cybersecurity issues discussed during a June summit meeting between U.S. President Joe Biden and Russian President Vladimir Putin (see: Analysis: The Cyber Impact of Biden/Putin Summit Meeting).
Executive Editor Jeremy Kirk contributed to this report.





