Measuring Success of No More Ransom Project
Business Continuity Management / Disaster Recovery
,
Fraud Management & Cybercrime
,
Governance & Risk Management
Europol Says Initiative Has Saved Ransomware Victims Over $1 Billion

EU law enforcement agency Europol says the No More Ransom Project, a portal launched five years ago, so far has helped more than 6 million ransomware victims worldwide recover their files for free so they could avoid paying almost 1 billion euros ($1.2 billion) in ransoms.
See Also: Expert Analysis: The Battle Against Ransomware
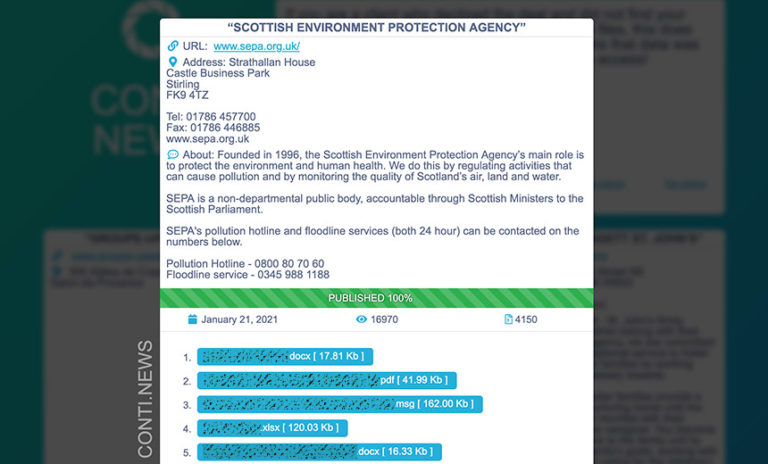
Europol’s European Cybercrime Center, the National High Tech Crime Unit of the Netherlands police and the cybersecurity companies Kaspersky and McAfee created the portal to help ransomware victims retrieve their encrypted data by providing them with decryptors.
The initiative now has nearly 170 law enforcement and corporate sponsors who offer 121 free tools that can decrypt 151 ransomware families, Europol says. The portal is available in 37 languages.
A ransomware victim can use the portal’s Crypto Sheriff tool to help determine which variant was involved and whether a free decryptor tool is available, says Jornt van der Wiel, a security researcher on Kaspersky’s global research and analysis team.
“A decryptor tool can be downloaded, installed and executed so the user get its files back,” he says. “If the user wants to report a crime, that information is available as well. Finally, in order for such an unfortunate event not to happen again, there is information on prevention on the website.”
Investigation Now More Complex
A number of major ransomware incidents have grabbed headlines this year, including those targeting software firm Kaseya, Colonial Pipeline and meat processor JBS.
But the average ransom paid by a victim has dropped 38% in the second quarter of 2021, compared to the first quarter, reaching $136,576, according to ransomware incident response firm Coveware.
Marijn Schuurbiers of the High Tech Crime Team at the Dutch Police says that ransomware actors have begun to specialize in specific areas. “For example, some specialize in data theft. Then there are groups that offer a ransomware-as-a-service model,” he says.
“Now, when you investigate one ransomware incident, you’re not looking at just one criminal or one small criminal group – you’re looking at five or six separate groups working together in an attack. That makes investigation more complex.”
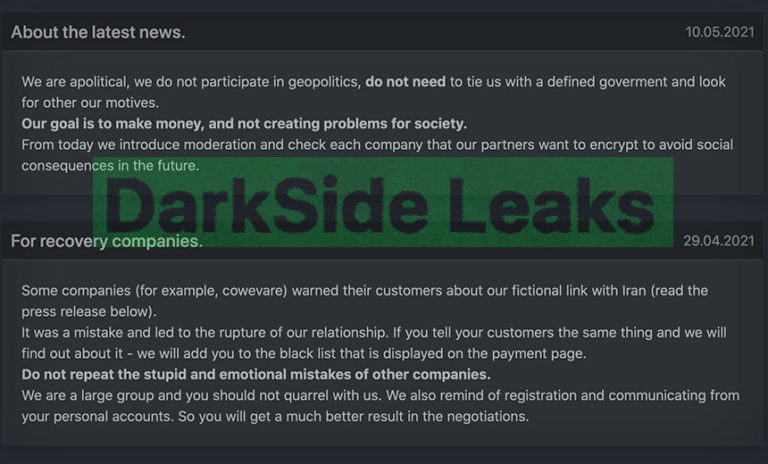
And as some ransomware groups apparently shut down operations, others pop up to take their place. For example, REvil’s infrastructure recently disappeared, but BlackMatter may be the group’s successor.
Risk Mitigation
One of the many risk mitigation steps that organizations can take is locking down remote desktop protocol, says Raj Samani, chief scientist and fellow at cybersecurity firm McAfee and one of the founders of the No More Ransom Project.
“All companies should consider what their approach will be in the event of a ransomware attack. Once this approach is set, testing out procedures to verify whether the measures they have in place actually work or not is key as well,” he adds.
The biggest mistake companies make is failing to create an adequate data backup plan, van der Wiel says. “It is part of the basic cybersecurity hygiene, but the fact that many companies still pay ransoms shows that there is something wrong with their backup strategy. Either it is lacking or is not working properly.”
In a recent interview, Fabian Wosar, CTO of Emsisoft, described a series of steps ransomware victims must take to smooth their recovery.