CVE-2021-37708
CVE-2021-37708

Overview. Pulse Connect Secure (PCS) gateway contains a vulnerability that can allow an unauthenticated remote attacker to execute arbitrary code. Description. CVE-2021-22893. An unspecified vulnerability exposed by the Windows File Share Browser and Pulse Secure Collaboration features of Pulse….
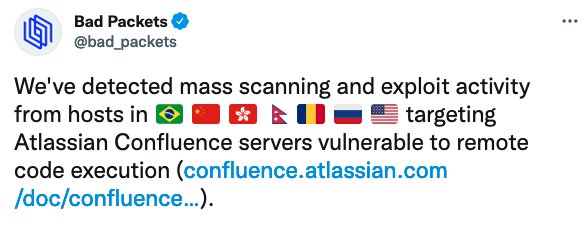
Hackers started exploiting a vulnerability in Atlassian’s Confluence enterprise collaboration product just one week after the availability of a patch was announced. Atlassian informed customers on August 25 that Confluence is affected by a critical vulnerability — described as an OGNL injection issue — that can allow remote attackers to execute arbitrary code on impacted…

CNA Financial, one of the largest insurance companies in the US, reportedly paid hackers $40 million after a ransomware attack blocked access to the company’s network and stole its data, according to a report from Bloomberg’s Kartikay Mehrotra and William Turton. CNA first announced the hack in late March, stating that it had seen a…
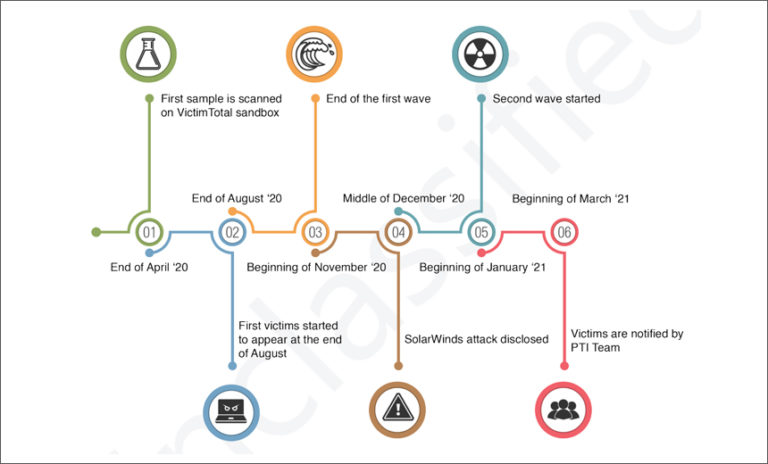
Cybercrime , Forensics , Fraud Management & Cybercrime Prodaft: APT Group Uses ‘Unprecedented Malware Detection Sandbox’ Prajeet Nair (@prajeetspeaks) • March 22, 2021 SolarWinds attack timeline (Source: Prodaft) Swiss cybersecurity firm Prodaft says it has accessed several servers used by an advanced persistent threat group tied to the SolarWinds supply chain attack. These…

Malware hosting domain Cyberium fanning out Mirai variants | IT Security News Android App Android App with push notifications Sponsors Endpoint Cybersecurity www.endpoint-cybersecurity.com – Consulting in building your security products– Employee awareness training– Security tests for applications and pentesting… and more. Daily Summary Categories CategoriesSelect Category(ISC)2 Blog (323)(ISC)2 Blog infosec (13)(ISC)² Blog (373)2020-12-08 – Files for an ISC…

SAP partners with Onapsis to mitigate active threats against unprotected SAP applications – IT Security News 8. April 2021 SAP and Onapsis jointly released a cyber threat intelligence report providing actionable information on how malicious threat actors are targeting and potentially exploiting unprotected mission-critical SAP applications. The companies have worked in close partnership with the…