Swiss Firm Says It Accessed SolarWinds Attackers’ Servers
Cybercrime
,
Forensics
,
Fraud Management & Cybercrime
Prodaft: APT Group Uses ‘Unprecedented Malware Detection Sandbox’
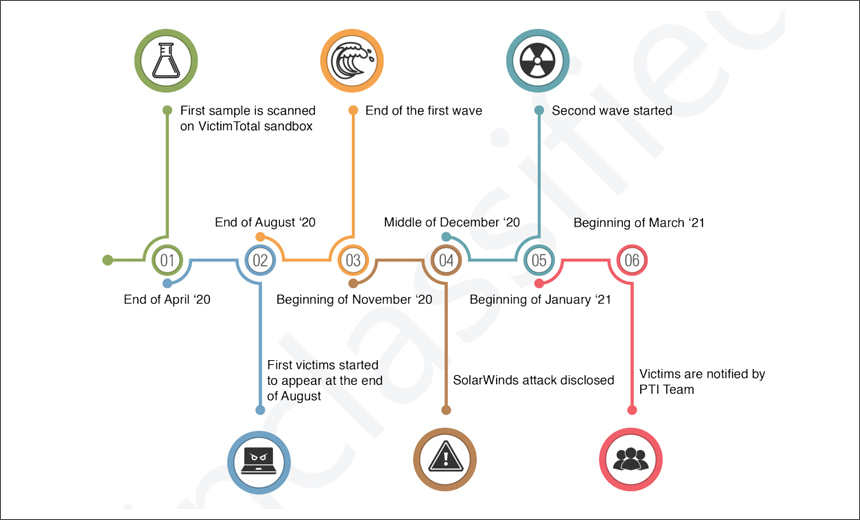
Swiss cybersecurity firm Prodaft says it has accessed several servers used by an advanced persistent threat group tied to the SolarWinds supply chain attack. These attackers continue to target large corporations and public institutions worldwide, with a focus on the U.S. and the European Union, the researchers say.
See Also: Top 50 Security Threats
Prodaft says the APT group, which it calls the SilverFish group, “has designed an unprecedented malware detection sandbox formed by actual enterprise victims, which enables the adversaries to test their malicious payloads on actual live victim servers with different enterprise AV and EDR solutions, further expanding the high success rate of the SilverFish group attacks.”
The U.S. federal agencies investigating the SolarWinds supply chain attack have said it likely was part of a cyberespionage campaign conducted by an APT group with ties to Russia. Russia has denied any involvement.
The new Prodaft report, however, does not tie SilverFish to any nation, although it makes reference to the attackers using Russian slang in reference to victims.
The supply chain attack is believed to have begun in March 2020 when attackers installed a backdoor in the SolarWinds Orion network monitoring system and then backdoored versions of Orion were shipped in SolarWinds updates.
Up to 18,000 customers installed and ran the Trojanized software. Later, attackers launched follow-on attacks on nine U.S. government agencies and about 100 private sector firms, federal investigators say (see: White House Preparing ‘Executive Action’ After SolarWinds Attack).
Reacting to this new Prodaft report, Gavin Ashton, security strategist at Stealthbits, now part of Netwrix, says: “While the scale of the attack was relatively well known, confirmation of the ongoing nature of the attack validates industry concerns. Once attackers establish persistence within an environment, it is difficult to remove them without considerable resources. This underscores the criticality of having not just detection and recovery processes in place – and rehearsed – but also basic prevention methods. Manage privileged access, patch your systems, retire outdated systems and perform backups.”
A SolarWinds spokesperson did not immediately reply to a request for comment.
‘Important Benchmark’
“Despite the fact that we refrain from making any attribution, we strongly believe that this case will become an important benchmark in terms of understanding the capabilities of advanced persistent threat actors, their rules of engagement operation and TTPs [tools, tactics and procedures],” the Prodaft researchers say. “We were able to analyze various servers and samples allowing us to link the SilverFish group with the infamous SolarWinds attacks, which became public around December 2020.”
Prodaft explains that it links the servers to the SolarWinds supply chain attack based on indicators of compromise and overlap with known victims of that attack.
The researchers say the same servers were also used by Evil Corp, which modified the TrickBot infrastructure to wage a large-scale cyberespionage campaign. Evil Corp was responsible for the development and distribution of the Dridex and WastedLocker malware, security experts say
“Upon analyzing the custom scripts and tools created by the SilverFish group, Prodaft’s threat intelligence team came to the conclusion that the main goal of this APT group is most likely to perform reconnaissance and exfiltrate data from target machines in a covert manner,” the report states.
Researchers also say they identified encoded/obfuscated PowerShell commands for loading Cobalt Strike and Empire beacon payloads. They say they extracted all of the Cobalt Strike beacons used by SilverFish attackers.
Organized Attack
The SilverFish group has apparently carried out “extremely sophisticated” cyberattacks on at least 4,720 targets, Prodaft says.
Prodaft says it has verified that victims of the SilverFish attacks include a U.S. military contractor, automotive manufacturing groups from Europe, aviation and aerospace companies, dozens of U.S. and EU banking institutions, one of the world’s leading COVID-19 testing kit manufacturers and others.
“While the United States is by far the most frequently targeted region, with 2,465 attacks recorded, it is followed by European states with 1,645 victims originating from no less than six different member states,” researchers note.
During the command-and-control server analysis, Prodaft researchers determined that one of the filter options was called “active team,” which indicates that the SilverFish likely is working systematically with multiple teams.
The APT group also appears to have the capability to auto-assign victims to a team based on the current workload, the researchers say.
“During our investigation, we found four different teams … who were actively exploiting the victims’ devices,” the researchers say. “These teams cycle frequently almost every day or every two days.” In addition, Prodaft reports that comments made about the victims include many English and Russian slang words.
Researchers found that most of the attacks were carried out between the hours of 12:00 and 16:00 UTC with almost no activity between 20:00 and 08:00 UTC. “From our point of view, this illustrates the existence of an organization that operates in an organized and disciplined manner in a hierarchical environment, one that is even highly compartmentalized,” the researchers note.
The researchers discovered a web panel the attackers used to periodically test their malicious payloads on more than 6,000 victim devices, scripts and implants.
“We distributed the victims list to relevant CERTs [Computer Emergency Readiness Teams] in their respective countries. We continue to share more IOCs with certain global threat intel/network security vendors who have already started conducting their own analyses and procedures,” the researchers say.




