Compromised Website Images Camouflage ObliqueRAT Malware
.
The ObliqueRAT malware is now cloaking its payloads as seemingly-innocent image files that are hidden on compromised websites.


The Metropolitan Police Department has confirmed that they suffered a cyberattack after the Babuk ransomware gang leaked screenshots of stolen data. The Metropolitan Police Department, also known as the DC Police or MPD, is the primary law enforcement agency for Washington, DC, the US capital. In a statement to BleepingComputer, the DC Police stated that…

JERUSALEM: Check Point Software Technologies said on Monday it acquired U.S.-Israeli cyber security company Avanan, which specialises in protecting email, where most cyber attacks begin. Check Point, which is based in Israel, did not disclose financial details. “More and more businesses are moving to cloud-email platforms and with email becoming a major channel to launch…

Cloud Security , Security Operations Private Equity Firm Also Owns Other Security Companies, Including McAfee Prajeet Nair (@prajeetspeaks) • April 27, 2021 Watch for updates on this developing story. See Also: Live Webinar | Empowering Financial Services with a Secure Data Path From Endpoint to Cloud Private equity firm Thoma Bravo on…

In a statement released Monday, the world’s largest meat supplier, JBS USA, says it was the “target of an organized cybersecurity attack” and resolving the incident will take time, which “may delay certain transactions with customers and suppliers.” The hack of the Colonial Pipeline last month temporarily disrupted the transportation of fuel in the United…
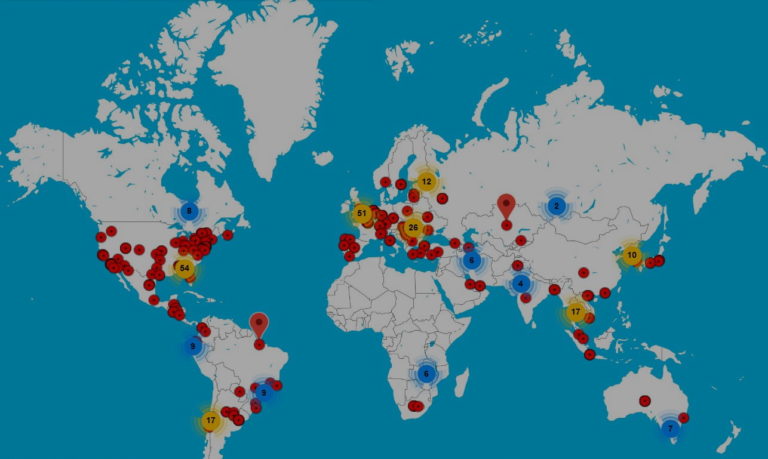
Security researchers discovered last week a new IoT botnet that deploys honeypots to capture attacks from rival botnets and then uses that information to hijack its rivals’ infrastructure. Named ZHtrap, this new botnet was built on an improved version of the infamous Mirai IoT malware. Discovered by the Netlab network security division at Qihoo 360, the…

Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks , Endpoint Security Social Media Giant says 2 Groups Were Conducting Cyberespionage Akshaya Asokan (asokan_akshaya) • April 25, 2021 Facebook says it has disrupted the activities of two Palestinian advanced persistent threat groups that targeted victims across the Middle East as part of cyber espionage campaigns….