Repurposed REvil Ransomware Used in Attacks
Cybercrime as-a-service
,
Fraud Management & Cybercrime
,
Next-Generation Technologies & Secure Development
Secureworks: New Group Apparently Waging Attacks Using Same Code
A newly identified threat group is using a repurposed version of REvil ransomware to wage attacks, according to security company Secureworks’ Counter Threat Unit.
See Also: Top 50 Security Threats
Researchers at Secureworks tracked what looked like a new ransomware strain, dubbed LV, which has been in the wild since late 2020, and found that it had identical code structure to REvil. While a threat group the researchers call “Gold Southfield” operates REvil, Secureworks has dubbed the separate group that’s using the repurposed version “Gold Northfield.”
The researchers say the use of the repurposed REvil malware indicates one of three scenarios: that Gold Southfield sold the source code or shared it as part of a partnership – or that the code was stolen.
Concealing the Connection
The researchers say the threat actors using the LV version of the malware likely used a hex editor to remove potentially identifying characteristics from the binary to conceal that LV is a repurposed version of REvil.
Variations in partner and campaign IDs across LV configurations and the practice of naming and shaming victims could indicate that Gold Northfield is launching a ransomware-as-a-service offering, the researchers say. But the researchers have not discovered LV ransomware advertisements on underground forums.
REvil, also known as Sodinokibi and Sodin, first appeared in April 2019. The gang behind the ransomware has been tied to several high-profile attacks, including those targeting meat processor JBS, Apple device blueprints, and a suspected attack at Fujifilm.
Leak Sites
Researchers identified two LV ransomware leak sites, which had an identical structure but appeared to be operated independently. “The sites listed victims during the same time frame, but only one victim was listed on both sites. It is unclear why Gold Northfield would operate two leak sites,” the researchers note. “The leak sites name and shame victims. The threat actors coerce the victims into paying the ransom by threatening to publish their sensitive information,” unless victims initiate contact within 72 hours.
To support their claims, the threat actors also post screenshots of the victim’s sensitive files on the leak sites.
“However, it appears that none of the victims’ data has been released as of this publication,” the researchers report. “It is unclear if victims paid the ransom and the threat actors just keep the full list of victims on the leak site as evidence of their conquests.”
A Cost-Effective Approach
The Secureworks report also notes: “By modifying the binary of a prolific ransomware family, the Gold Northfield threat actors significantly expedited their maturity within the ransomware ecosystem. Without expending resources on ransomware development, the group can operate more efficiently than its competitors while still offering a best-in-class ransomware offering, ultimately resulting in a more profitable business model.”
The ability to repurpose the REvil binary suggests that the Gold Northfield threat actors have technical capabilities, the researchers say. “Additionally, the complexity required for this repurposing and the configuration variations across LV samples suggest that Gold Northfield may have automated the process. Although a RaaS for the LV ransomware could provide direct competition for Gold Southfield’s RaaS offering, the lack of a reliable and organized infrastructure needed to operate a successful RaaS offering suggests that Gold Northfield has to expand its capabilities and resources to compete with other ransomware operations.”
Ransom Notification
Researchers say that the only ransom note change the LV operators made from the standard REvil format was replacing REvil’s ransom payment Tor domain with LV’s domain.
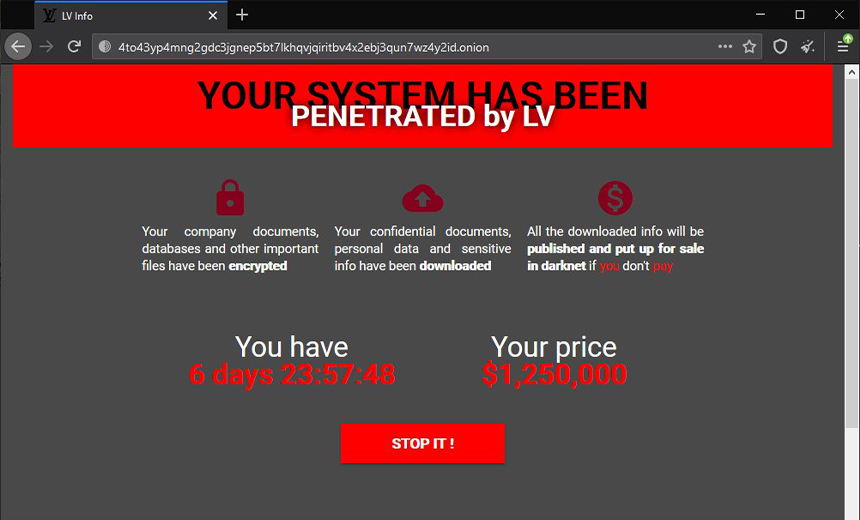
Upon accessing the ransom site, a victim is presented with a form that requests a key from the original ransom note. The original ransom note generally represents information about the ransomware infection that has been encrypted.
The Secureworks researchers tried to submit the key from the ransom note, but it returned HTTP errors. Researchers say that the errors may have been caused by anti-analysis controls implemented by LV operators to inspect characteristics of the submitted key for suspicious or undesirable activity.
A successful key submission displays a page showing the ransom amount in U.S. dollars and how much time the victim has to pay the ransom before sensitive data is disclosed. The page also includes a live chat function for the victim to interact with the threat actors, the researchers report.
Another REvil Attack
Meanwhile, it appears the original REvil operation is continuing its attacks.
A Brazilian medical diagnostic company, Grupo Fleury, said this week that it had suffered an external attack that disrupted business operations. Bleeping Computer, citing cybersecurity experts, reports REvil ransomware was involved.
A ransom note accessed by Bleeping Computer says that the “REvil ransomware operation is demanding $5 million to receive a decryptor and not leak allegedly stolen files.”