What is a DDoS Extortion Attack and How do you Respond to it?
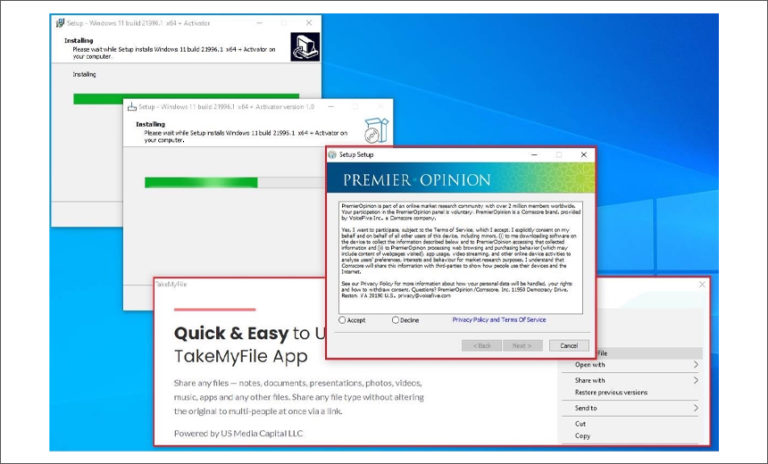
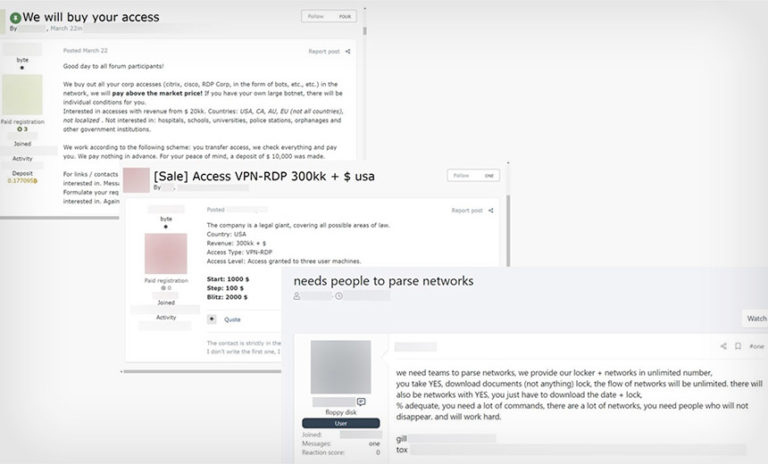
DDoS extortion attacks have skyrocketed over the past year and are expected to trend upwards in the future too. DDoS attacks aren’t new threats. However, cybercriminals are leveraging these attacks to extort money from organizations by causing downtimes and preventing legitimate users from accessing the web application. With the global pandemic forcing organizations to adopt…