9 Ransomware Enablers – And Tactics for Combating Them
Fraud Management & Cybercrime
,
Governance & Risk Management
,
IT Risk Management
Patch Management and Locking Down Remote Desktop Protocol Remain Essential Defenses
Ransomware operations continue to thrive thanks to a vibrant cybercrime-as-a-service ecosystem designed to support all manner of online attacks.
See Also: Live Webinar | Improve Cloud Threat Detection and Response using the MITRE ATT&CK Framework
Some of these services are based on criminals exploiting known vulnerabilities that organizations have yet to patch or brute-forcing access to remote desktop protocol connections and then selling this access to others. Improving patch management and RDP security practices are obvious defenses.
Other ransomware enablers, however, seem likely to keep thriving unless stronger measures are taken. Disrupting the cybercrime forums on which ransomware operators recruit specialists and purchase services, in particular, typically requires law enforcement intervention.
With that in mind, here are nine ransomware enablers and what – at least in some cases – might be done to better combat them.
1. Fresh Forums Facilitate Ransomware
Sometimes, the cybercrime community appears to self-police – at least in theory.
Following the political fallout caused by the May attacks by DarkSide against Colonial Pipeline in the U.S. and by Conti against Ireland’s health service, for example, some of the largest Russian-language cybercrime forums – including XSS and Exploit – officially banned any communications that involved ransomware.
Some security experts say, however, that many forums do appear to tolerate workarounds, such as advertisements for “pentesters” and “access brokers,” provided those listings don’t specifically mention schemes involving crypto-locking malware.
Although some bigger forums have banned ransomware discussions, some smaller players appear to be embracing them, including at least one newcomer.
On July 12, the Babuk ransomware operator’s data leak site, which had been renamed from Babuk to Payload.bin in June, changed again to become a cybercrime forum called RAMP, according to Israeli threat intelligence firm Kela. Officially, RAMP stands for “Ransom Anon Mark Place,” but Kela notes that “the name of the new forum is a reference to the now-defunct Russian Anonymous Marketplace – a drug market that closed in 2017.”
The new forum says it’s designed to support ransomware-as-a-service operations, which is the dominant business model today involving ransomware. Via RaaS, an operator or administrator develops crypto-locking malware, which an affiliate procures via a portal, uses to infect victims, and receives a cut of every ransom paid.
“A new admin initially named ‘TetyaSluha’ – now ‘Orange’ – announced it is now a place where ransomware affiliates can be protected from unscrupulous RaaS programs,” Kela says, noting that the admin appears to have previously been involved in the Babuk operation, if not to have led it.
“The admin claimed that following the ransomware ban on other forums, he wanted to create a new community,” Kela adds, noting that the forum already has sections devoted to initial access brokers, ransomware vendors and affiliate programs.
After suffering a spam attack, RAMP went offline on Monday, but a message on the site states it’s set to return on Aug. 13, Kela says. When it does, it will no doubt continue to be a target for threat intelligence firms that want to eavesdrop on discussions, and potentially also for law enforcement agencies seeking to identify members of the cybercrime underground and attempt to detain them.
2. Groups Have Other Communication Strategies
Larger ransomware operations have likely also cultivated an extensive list of connections and well-established relationships, and so they’re less reliant on forums, says Bob McArdle, director of cybercrime research at security firm Trend Micro.
Likewise, ransomware operations have historically recruited across multiple channels, says threat intelligence firm Flashpoint.
“Some, such as Black Shadow, maintain Telegram accounts; others, such as LockBit 2.0, run ransomware-as-a-service recruitment on their forums,” it says.
Last week, meanwhile, the AvosLocker ransomware operation used a service for distributing spam via Jabber and Telegraph to advertise its ransomware partner program, according to security firms.
3. Specialists Provide On-Demand Services
Ransomware operators don’t just seek to recruit new affiliates. Security experts say larger and more sophisticated operations – such as REvil, DarkSide and Ryuk – have thrived by recruiting diverse specialists to help make every attack succeed.
“For a single ransomware attack to run full cycle, there may be over a dozen unique actors, each with a different specialized skill set, that contribute to different stages of the attack,” says ransomware incident response firm Coveware. “When it appears a ransomware group is focusing on a specific method of ingress, it is probable that they have just found a specialist that is upstream of them and is selling network access to future victims that fit the profile of the RaaS group. Oftentimes, these upstream specialists are selling this access more than once, creating competition to impact the network before a competitor does.”
Not all specialists are involved in directly hacking into an organization. Some provide ancillary services, such as negotiating with victims. Others can bring other types of pressure on victims to pay, for example, via distribute denial-of-service attacks that don’t appear to require top technical skills to deliver.
Threat intelligence firm Intel 471 says it tracked an individual who first appeared on a well-known cybercrime forum in January and went on to become a claimed associate of the notorious DarkSide operation, prior to its shutdown following the Colonial Pipeline attack fallout. “The actor claimed to have launched DDoS attacks against DarkSide’s victims for six weeks before the gang’s shutdown. Ten to 20 targets were under DDoS at any given time, with attacks lasting from one to 21 days, and they earned $500 to $7,000 each time a victim paid a ransom,” Intel 471 says.
Opportunities for newcomers appear plentiful. “Over a six-month period, the person built enough reputation to latch onto one of the most notorious ransomware gangs in operation, profiting off the million-dollar ransoms DarkSide pulled in before disappearing,” Intel 471 says. “While this actor is new, they followed a model that is being replicated by a variety of actors that work in the cybercrime underground.”
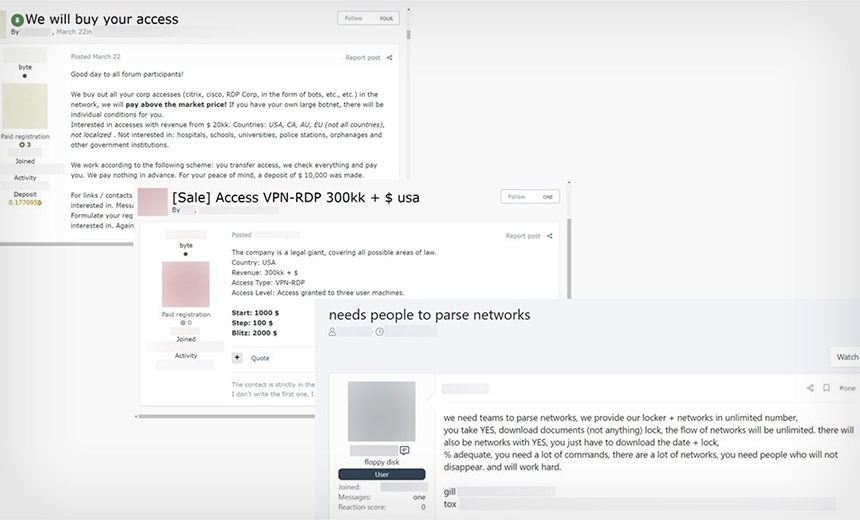
4. Initial Access Brokers Smooth the Way
Among the various specialists tapped by ransomware attackers are initial access brokers, which is a fancy way of describing hackers who gain access to an organization’s network and then sell that access to others. For ransomware-wielding attackers, buying access means they can spend more time infecting victims without having to hack into them first.
Such brokers’ offerings appear to be surging. Reviewing the 10 most popular Russian-language and English-language criminal forums in the first three months of this year, security firm Positive Technologies counted nearly 600 access offers, compared to 255 the previous quarter.
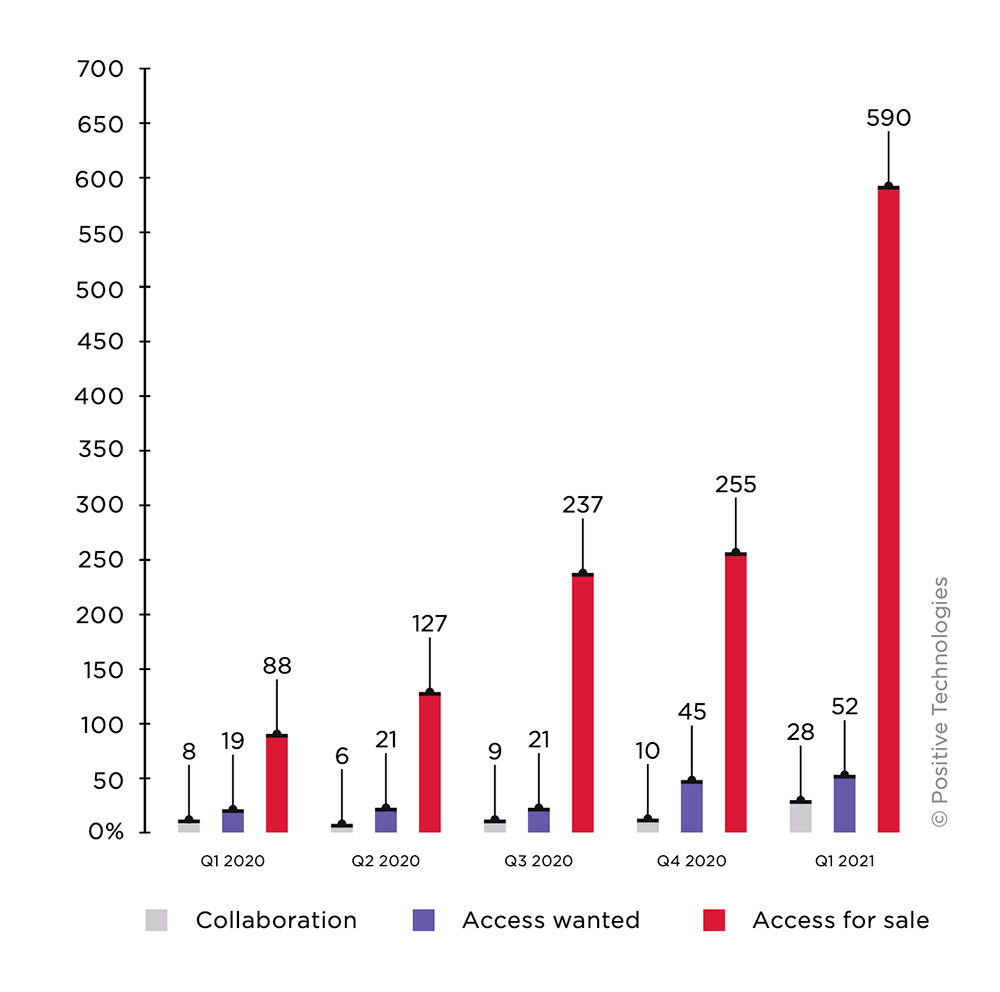
This doesn’t include all such access being offered for sale, because some ransomware operations form partnerships with initial access brokers or pay them a premium for right of first refusal. Other brokers will list some “accesses” they’re offering for sale, but tell potential buyers to contact them directly for information on other targets.
The increase in publicly available offers, however, suggests more organizations risk falling victim to criminals who gain remote access to their network and offer to sell this access to the highest bidder.
5. Phishing and RDP Provide Access
For ransomware-wielding attackers, phishing and brute-forcing RDP access credentials remain the top two tactics for gaining initial access to a system, Coveware says.
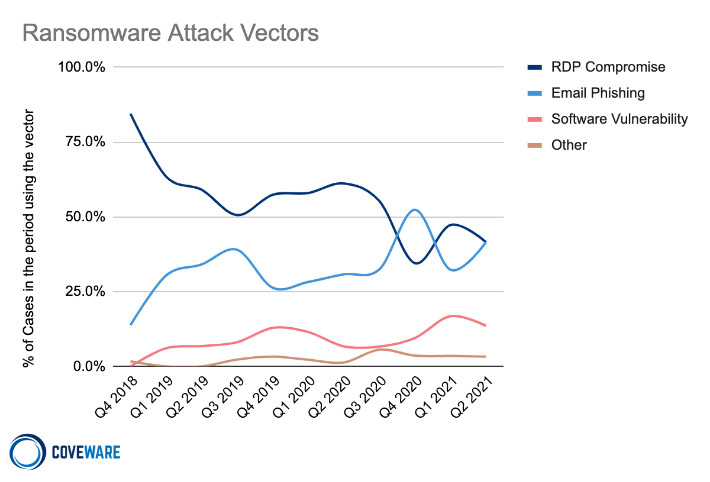
As a result, having robust phishing defenses in place and locking down RDP remain defensive no-brainers.
6. Unpatched Vulnerabilities Also Provide Access
Third place on the list of how ransomware-wielding attackers get access is exploiting security flaws. From April through June, Coveware said, it saw two flaws being especially targeted by attackers to gain remote access to an organization’s network. Those were a Fortinet FortiOS path traversal vulnerability affecting SSL VPN devices, designated CVE-2018-13379, and a vulnerability in SonicWall SRA 4600 devices, designated CVE-2019-7481.
FireEye’s Mandiant incident response group says in a report that it saw a group wielding FiveHands ransomware begin targeting a flaw in SonicWall SMA 100 Series VPN appliances in February, prior to the vendor issuing a patch.
Intel 471 says members of FiveHands have since discussed targeting VMware Sphere Client vulnerabilities that the vendor patched in May and the Windows Print Spooler Service flaw that’s been dubbed PrintNightmare, which Microsoft only fully patched earlier this month.
The perpetual patch or perish problem means that as soon as vendors release a security fix, attackers will race to reverse-engineer it to find a flaw they can potentially exploit to easily amass new victims who haven’t yet installed the update.
“Cybercriminals pay attention to CVEs as much as anyone else, knowing that organizations drag their feet in closing vulnerabilities that give criminals the access they need to carry out attacks with little struggle,” Intel 471 says.
Thankfully, at least in the case of SonicWall exploring how it might hit the VMware and PrintNightmare vulnerabilities, Intel 471 tells Information Security Media Group that so far “it seems like the group racing to take advantage of the vulnerability … hasn’t really worked.”
7. Open-Source Options Facilitate More Attacks
Malware source code regularly gets leaked or dumped in the wild, enabling criminals to reuse and adapt it. Examples abound: In 2011, for example, the source code for the notorious Zeus banking Trojan was leaked online for unknown reasons and quickly adopted by numerous criminals.
Just weeks after the IoT-targeting Mirai botnet appeared in August 2016, its creators leaked the source code online, likely to try and throw investigators off their tracks. Many other criminals have since adapted and repurposed the malware.
On the ransomware front, in 2015, security researcher Utku Sen built both EDA2 and Hidden Tear as open-source ransomware, publishing the source code on GitHub. While the researcher stated that the code was developed for educational purposes, it was quickly adopted by criminals, including for a variant with a “Pokemon Go” theme.
One obvious takeaway for any would-be security researchers: Never release proof-of-concept ransomware into the wild.
8. Leaks Feed Demand for Crypto-Locking Malware
More recently, someone leaked a Windows executable named “Babukbuilder,” which turned out to be key software used by Babuk (see: Babuk Ransomware Mystery Challenge: Who Leaked Builder?).
Builders are used to generate unique copies of malware, and in the case of Babuk, to generate both crypto-locking malware as well as a decryption tool for every different victim organization.
The executable was first spotted by Kevin Beaumont, head of the security operations center for London-based fashion retail giant Arcadia Group, who reported that it would generate malware that would work on “Windows, VMware ESXi, network-attached storage x86 and ARM,” respectively referring to Microsoft’s operating system, as well as a widely used VMware hypervisor and NAS devices.
Security experts, including Beaumont, have verified that the software works.
Apparently, some less advanced criminals have also leaked their tools. “In late June, an operator using info-stealing malware Vidar issued ‘download and execute’ tasks to bots, aiming to install the Babuk ransomware variant generated by the builder,” Intel 471 reports.
9. Reusing Malware Shortens Development Cycles
Some malware developers apparently borrow, share or steal code. For example, there are “multiple similarities in the code between Conti ransomware and BazarLoader,” which is malware designed to provide remote access to an infected endpoint, Intel 471 reports.
Ransomware-wielding attackers have previously used such malware, including BazarLoader, to gain initial access on a device and then to download and run additional tools and malware, such as Ryuk and Vatet (see: Ransomware-Wielding Gangs Love to Phish With Trojan Loaders).
But Intel 471 says it appears that whoever develops Conti has borrowed some of BazarLoader’s code. “One particular similarity is in the code that allows Conti to evade analysis in an isolated instance, such as a sandbox or virtual machine,” it says. “The code of this function is nearly identical to that used by the BazarLoader, with both functions following the exact logic and executing the same way when searching for hooks.”
Unfortunately, once such code gets into the wild, there’s no easy way to eliminate it. In some cases, however, security firms can deduce ways of spotting it operating in the wild, based on how it works, to help organizations defend against it.






