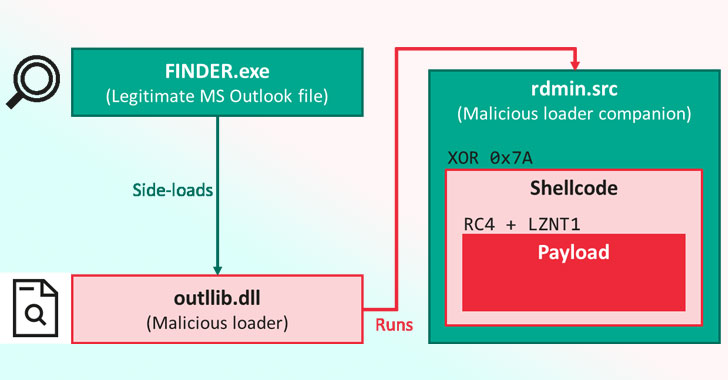
Belgium Investigating Attack on Interior Ministry Network
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Federal Public Service Interior Investigating Possible Cyberespionage Campaign

Belgium’s interior ministry, Federal Public Service Interior, is investigating an attack against its network that appears to have the hallmarks of a cyberespionage campaign.
The intrusion, which apparently occurred in April 2019, was not discovered until March when the ministry, along with Belgium’s Center for Cybersecurity, began patching for vulnerabilities in Microsoft Exchange email servers, according to the Belgium government.
See Also: Top 50 Security Threats
The patching came after Microsoft noted that zero-day vulnerabilities found in some versions of its on-premises Exchange email server were being exploited, compromising thousands of servers around the world (see: Microsoft Patches Four Zero-Day Flaws in Exchange).
In March, Microsoft and other security researchers urged organizations and government agencies to immediately apply patches.
During its Exchange patching effort, the Center for Cybersecurity’s “cyber experts identified subtle tracks of questionable acts on the Federal Public Service Interior network,” the government said in a statement. “The first tracks date from April 2019 and indicate a very sophisticated cyberattack. The complexity of this attack indicates an actor who has cyber capacities and extensive resources. The perpetrators acted in a targeted manner, which is reminiscent of espionage.”
After the intrusion was discovered in March, Belgium’s interior ministry removed the malware, but it continues to monitor for other possible attacks. The Federal Prosecutor’s Office is leading the investigation into what happened and what group might have been responsible.
The government did not say if the espionage campaign targeted Exchange servers or if this incident was related at all to the attacks that Microsoft has attributed to Hafnium, a Chinese threat group. Some security experts reported, however, that several groups exploited the zero day flaws in Exchange earlier this year.
Security firm Volexity, which helped discover the Exchange flaws, believes that the attacks that took advantage of these flaws started around Jan. 6.
The discovery of the attack against the interior ministry comes a few weeks after the websites of about 200 public and private entities in Belgium were knocked fully or partially offline by a large-scale distributed denial-of-service attack against the publicly funded internet service provider Belnet (see: DDoS Attack Knocks Belgian Websites Offline).
Difficult Attribution
Ilia Kolochenko, founder of security firm ImmuniWeb, and a member of Europol Data Protection Experts Network, notes that attributing cyberespionage campaigns can be difficult.
“Oftentimes, they deal via so-called brokerage, making attribution even harder by placing hacking orders to trusted intermediaries who later hire and pay the attackers,” he says.
Attackers “commonly try to mislead possible forensic investigations of the intrusion by copying attack patterns of known hacking groups or, among other things, by stealing data that they don’t really need, but want to exfiltrate as if it was the primary target of the attack,” he adds.
Other Cyber Campaigns
Other countries throughout Europe have also reported attacks that have targeted elected officials and government agencies and appear connected to various espionage campaigns.
For example, in December 2020, Norway accused the Russia-linked advanced persistent threat group known as APT28 of attacking the email accounts of some elected officials and government employees (see: Norway Says Russia-Linked APT28 Hacked Parliament).
And in March, several members of the German Parliament as well as political activists were targeted by a spear-phishing campaign, according to German newsmagazine Der Spiegel. German lawmakers had previously been targeted by Russia-linked attack groups in 2015 (see: German Parliament Sustains Another Attack).