Hackers From China Target Vietnamese Military and Government
A hacking group related to a Chinese-speaking threat actor has been linked to an advanced cyberespionage campaign targeting government and military organizations in Vietnam.
The attacks have been attributed with low confidence to the advanced persistent threat (APT) called Cycldek (or Goblin Panda, Hellsing, APT 27, and Conimes), which is known for using spear-phishing techniques to compromise diplomatic targets in Southeast Asia, India, and the U.S. at least since 2013.
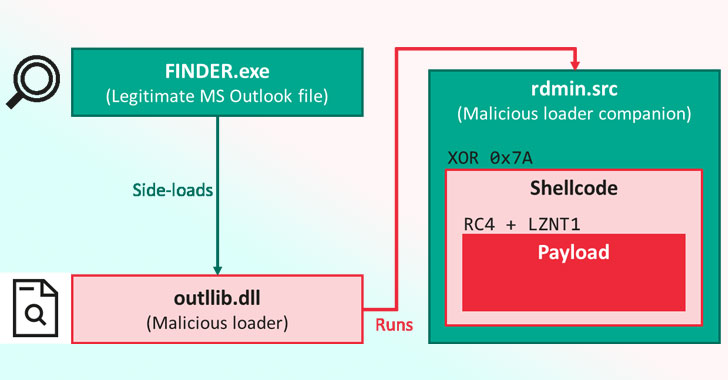
According to researchers from Kaspersky, the offensive, which was observed between June 2020 and January 2021, leverages a method called DLL side-loading to execute shellcode that decrypts a final payload dubbed “FoundCore.”
DLL side-loading has been a tried-and-tested technique used by various threat actors as an obfuscation tactic to bypass antivirus defenses. By loading malicious DLLs into legitimate executables, the idea is to mask their malicious activity under a trusted system or software process.
In this infection chain revealed by Kaspersky, a legitimate component from Microsoft Outlook loads a malicious library called “outlib.dll,” which “hijacks the intended execution flow of the program to decode and run a shellcode placed in a binary file, rdmin.src.”
What’s more, the malware comes with an extra layer designed explicitly to safeguard the code from security analysis and make it difficult to reverse-engineer. To achieve this, the threat actor behind the malware is said to have scrubbed most of the payload’s header, while leaving the rest with incoherent values.
Kaspersky said the method “signals a major advancement in sophistication for attackers in this region.”
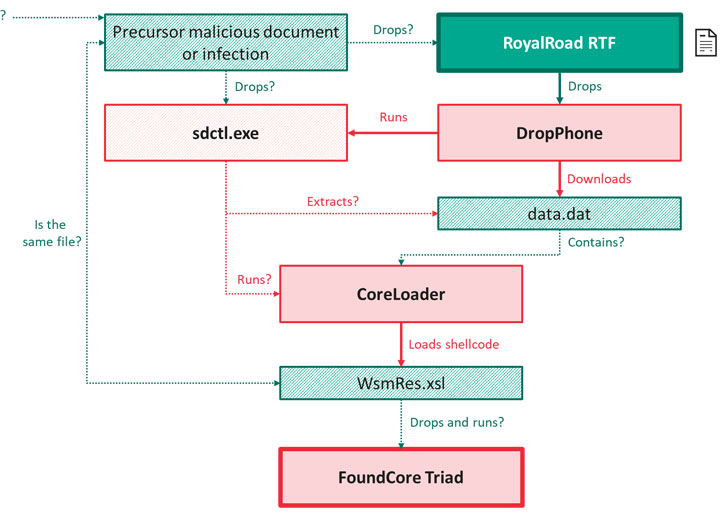
Besides giving the attackers full control over the compromised device, FoundCore comes with capabilities to run commands for file system manipulation, process manipulation, capturing screenshots, and arbitrary command execution. Infections involving FoundCore were also found to download two additional malware. The first, DropPhone, gathers environment-related information from the victim machine and exfiltrates it to DropBox, while the second, CoreLoader, runs code that enables the malware to thwart detection by security products.
The cybersecurity firm theorized the attacks originate with a spear-phishing campaign or other precursor infections, which trigger the download of decoy RTF documents from a rogue website, ultimately leading to the deployment of FoundCore.
Among dozens of affected organizations, 80% of them are based in Vietnam and belong to the government or military sector, or are otherwise related to the health, diplomacy, education, or political verticals, with other victims, occasionally spotted in Central Asia and Thailand.
“No matter which group orchestrated this campaign, it constitutes a significant step up in terms of sophistication,” the researchers concluded. “Here, they’ve added many more layers of obfuscation and significantly complicated reverse engineering.”
“And this signals that these groups may be looking to expand their activities. Right now, it may seem as if this campaign is more of a local threat, but it’s highly likely the FoundCore backdoor will be found in more countries in different regions in the future,” said Kaspersky senior security researcher Mark Lechtik.