‘We stole 3TB of French AXA Group data’
Avaddon ransomware gang is threatening to carry out DDoS attacks and data leaks if AXA did not corporate with the attackers.
French insurance giant AXA Group announced on Sunday that the company has become a victim of a ransomware attack. The incident affected its IT operations of Asia Assistance in Thailand, the Philippines, Malaysia, and Hong Kong.
In a statement, the company said that “certain data operated by Inter Partners Asia in Thailand has been accessed by cybercriminals and there is no proof for the moment what data has been stolen.”
AXA Partners is the structure dedicated to the development of the group’s international assistance partnerships. Regulators and the company’s business partners have been made aware of the incident.
The company is investigating the incident with the support of outside experts.
“If the investigation confirms that anyone’s sensitive data has been affected, the necessary steps will be taken to prevent and support all business customers and affected individuals,” the company added.
Avaddon ransomware gang claims responsibility
Hackread.com can confirm that the infamous Avaddon ransomware gang has claimed responsibility for the ransomware attack on AXA Group.
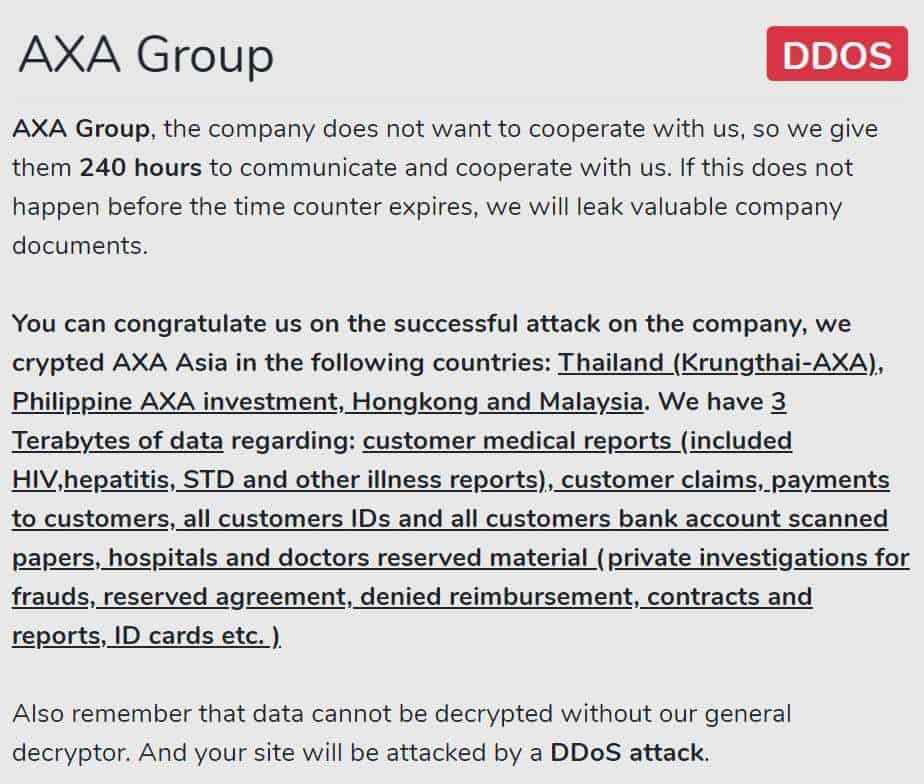
On its official website on the dark web accessible via Tor browser, the ransomware gang claims it managed to steal 3 terabytes of AXA Group’s data which allegedly includes:
- ID cards
- Passport copies
- Customer claims
- Reserved agreement
- Denied reimbursement
- Payments to customers
- Contracts and reports
- All customers IDs and all customers bank account scanned papers
- Hospitals and doctors reserved material (private investigations for frauds)
- Customer medical reports (included HIV, hepatitis, STD, and other illness reports).
Sample data leaked by the hackers
A Thai passport among leaked data (Image credit: Hackread.com)
The hackers have also warned AXA Group of data leaks and DDoS attacks if their demands are not met.
AXA Group, the company does not want to cooperate with us, so we give them 240 hours to communicate and cooperate with us. If this does not happen before the time counter expires, we will leak valuable company documents,” the hackers said in a statement as seen by Hackread.com.
The attack structure of the Avaddon ransomware gang follows the same modus operandi as other ransomware groups such as breaching the security of its target, stealing data and locking the files on the victim’s system, and demand ransom payment for decrypter key/tool.
However, in case if the ransom is not paid Avaddon carries out DDoS attacks on the website of its victim in an attempt to force them to pay the ransom.
On the other hand, the DarkSide group that was behind the ransomware attack on the largest fuel pipeline in the United States, couldn’t take heat after the attack and ended up quitting its operation. But the Avaddon ransomware gang is hunting for new targets and the list of its victims is growing with every passing day.
Last week, a Melbourne-based service provider called Communication, which is a platinum partner of telecom giant Telstra became the victim of a series of cyber-attacks and data leaks. The attack was also claimed by the Avaddon ransomware gang.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.