The Games Ransomware Attackers Play
Business Continuity Management / Disaster Recovery
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Criminals Regularly Fib About Stealing Data, Sparing Hospitals and Much More
If you’re a criminal, practicing good operational security would seem to preclude granting tell-all news media interviews. And yet we’ve seen a spate of attackers who wield ransomware – including MountLocker, LockBit, REvil and DarkMatter – sharing insights into their inclinations, motivations and tactics.
See Also: Live Panel | How Organizations Should Think About Zero Trust
One perhaps inadvertent takeaway from their interviews is the extent to which ransomware-wielding criminals lie (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
“We are familiar with the DarkSide team from working together in the past, but we are not them, although we are intimate with their ideas.”
Researchers at Cisco Talos, for example, interviewed an individual they’ve called “Aleks” who was working as an affiliate with ransomware-as-a-service operations, including LockBit. Such operations develop and offer their crypto-locking malware to affiliates via a portal. The affiliate takes the malware and infects victims. Whenever a victim pays, the operator and affiliate share in the profits.
Craig Williams, director of outreach at Cisco Talos, said the biggest surprises from the interactions with Aleks involved how much he appeared to inadvertently reveal.
“The ones that really surprised us the most were the guy’s insights into himself that he accidentally shared – namely, the belief that he wanted to convey that he didn’t target healthcare and other targets that are ethically charged,” Williams told me. “Now, the reality was, we knew the entire time that he was targeting healthcare. But it was really interesting to see that he wanted to convey this almost Robin Hood-type view of himself – that he was really a good guy that was misunderstood and that had to struggle in life and feed his family.”
If there’s a common set of “interview with a ransomware attacker” cliches, it’s that all attackers claim to love the motherland and their families and that they use cybercrime simply as a way to put food on the table. Faced with such considerations, who among us wouldn’t wield ransomware?
Attackers Regularly Try Rebranding
The White House sees things differently. Although ransomware has been pummeling organizations for years, attacks in May that disrupted critical infrastructure in the U.S. and Ireland led the Biden administration to escalate efforts to eradicate this criminal business model.
One such catalyst was the DarkSide RaaS operation hitting Colonial Pipeline Co., leading to a warning from Biden to Russian President Vladimir Putin that if he didn’t crack down on criminals operating inside his border, the U.S. reserved the right to do so.
In response, DarkSide appeared to go quiet. REvil, aka Sodinokibi, also went quiet after it hit meat-processing giant JBS – which paid it an $11 million ransom – and later remote management software firm Kaseya, leading to about 1,500 organizations getting hit with ransomware.
One persistent question has been: Have the Avaddon, DarkSide and REvil operations truly gone away, or are they just going to get rebooted with new names? (See: Ransomware Changes: DoppelPaymer Rebrands; Babuk Evolves)
Did DarkSide Simply Reboot?
Enter a new operation called BlackMatter, which claims to have “incorporated … the best features of DarkSide, REvil and LockBit.”
On Monday, Dmitry Smilyanets of cybersecurity firm Recorded Future’s news site The Record published an interview with the apparent leader of BlackMatter.
Is the operation, however, simply a reboot of DarkSide or another group?
“We are familiar with the DarkSide team from working together in the past, but we are not them, although we are intimate with their ideas,” the BlackMatter representative told Smilyanets.
But security experts, including Fabian Wosar, CTO of security firm Emsisoft, report that there are numerous similarities between the BlackMatter and DarkSide code, to the extent that they appear to be the same crypto-locking malware and decryption toolsets.
After looking into a leaked BlackMatter decryptor binary I am convinced that we are dealing with a Darkside rebrand here. Crypto routines are an exact copy pretty much for both their RSA and Salsa20 implementation including their usage of a custom matrix.— Fabian Wosar (@fwosar) July 31, 2021
On Tuesday, blockchain analysis firm Chainalysis added further evidence of such a relationship, reporting that, based on its analysis of the cryptocurrency wallets being used by BlackMatter, it was simply a rebrand of DarkSide.
THREAD: Based on our blockchain analysis, we can confirm reports speculating that DarkSide #ransomware group has rebranded to BlackMatter. This is part of a trend in which ransomware groups shut down & reemerge with new names, often after law enforcement actions or media scrutiny— Chainalysis (@chainalysis) August 3, 2021
False Data Theft Claims
It’s useful to highlight exactly how and why attackers might lie, beyond trying to dodge White House reprisals.
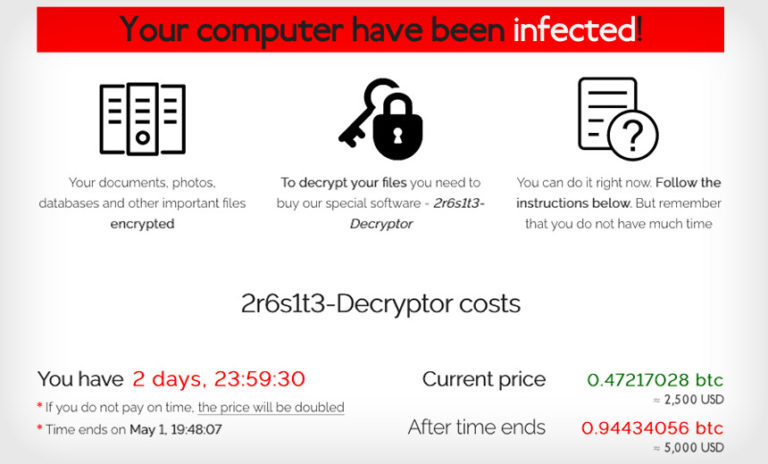
For example, many operations now claim to have stolen data when they begin extorting victims, to increase the pressure to pay. But not all such claims are true, and when they are, sometimes the stolen data is relatively worthless.
Ransomware incident response firm Coveware, for example, reported that near the end of 2020, it was seeing a rise in attackers falsely claiming to have stolen data before they crypto-locked systems. Attackers may make such claims when first attempting to extort a victim, but before they have posted the victim’s name to a data leak site or published samples of stolen data.
The takeaway for victims who are considering paying a ransom in part because of stolen data is that data theft claims should never be trusted without proof.
But many attackers have ways of sidestepping any requests for proof.
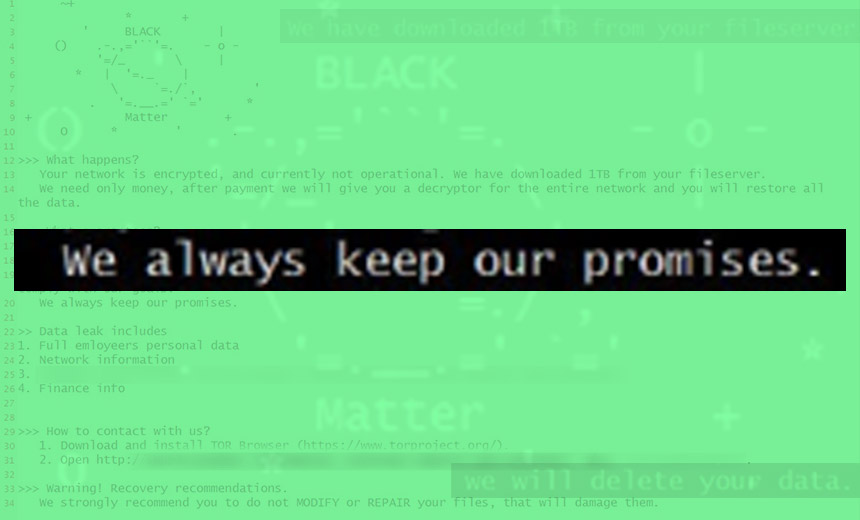
For example, “Dissent,” who runs the DataBreaches.net blog, reported earlier this year that the REvil operation told her that it never provided copies of stolen data to victims as it “violates our privacy policy,” whatever that means. But REvil did say it would share screenshots of directories showing stolen data. Of course, attackers could easily have taken such a screenshot without actually stealing any underlying data.
Dissent said the operation also didn’t hesitate to lie in the quest to receive a ransom payment. In one excerpt of a chat between a REvil victim and a REvil “customer support” worker, for example, the victim asked if data had been stolen. “We took your data,” REvil responded.
The victim then chose to pay REvil a bitcoin ransom worth $25,000 – negotiated down from $50,000 – with the understanding that the attackers would share a directory listing showing which files had been stolen, Dissent said. After asking for this information again post-payment, REvil’s support representative changed their tune, telling the victim: “We did not take any data from you.”
Repeat Extortion an Ongoing Threat
Clearly, ransomware attackers routinely pedal false promises or use fuzzy math.
Many groups now practice so-called double extortion, which involves demanding one ransom for a decryptor and another for the promise that stolen data will be deleted – if indeed any data was even stolen in the first place.
Last year, Coveware warned that “unlike negotiating for a decryption key, negotiating for the suppression of stolen data has no finite end,” and it was likely attackers would never delete such data. In the case of REvil, it noted some victims who paid were extorted a second time – with a repeat threat to leak stolen data unless they paid more.
Attackers, however, keep looking to gain any potential edge for reaching a payday. Some have taken to using so-called triple extortion – adding distributed denial-of-service attacks to further disrupt a victim – or even quadruple extortion, in which they contact a breached organization’s customers or business partners to tell them about the attack.
Own Our Failures – Who, Us?
Perhaps it should go without saying that ransomware attackers spin their version of reality to make themselves look as good as possible. In the fallout from the Colonial Pipeline hit, for example, DarkSide’s administrators blamed an affiliate for poor target selection. But this is disingenuous in the extreme.
“If you think about it, in the affiliate model of ransomware, the affiliates are like contractors that you’re responsible for,” Bob McArdle, director of cybercrime research at Trend Micro, tells me. “They’re not quite like your core group. But they’re still people that you’re responsible for, and if they go off and do things that are outside your rules, just like in the real world, there’s a certain amount of repercussions on you as the company that hired them, for want of a better word.”
BlackMatter, meanwhile, claims that it will vet all targets before affiliates are allowed to unleash crypto-locking malware. BlackMatter’s supposed list of rules on its site states that “we do not attack” a long list of entity types, including hospitals, critical infrastructure, oil and gas firms, defense contractors, nonprofit organizations or government agencies.
Read the Small Print
But don’t forget to read the small print: “If your company is on that list you can ask us for free decryption.” So while the operation claims that it will practice exceptional care when picking targets, in fact, what it appears to be saying is that lots of organizations are going to get hit, and if yours falls into one of the aforementioned categories, it will consider sharing a “free” decryption tool.
Of course, that’s a different scenario, because recovering from a ransomware hit can take months, if not years. Ireland, for example, literally deployed the army to help roll out new systems for its health service after it was hit by Conti ransomware. Sure, Conti gave it a “free decryptor.” But the attack led to weeks, if not months, of unnecessary disruption, putting lives in danger.
The obviously better approach, of course, would be to not hit organizations with ransomware in the first place. But for so many criminals, whatever their claims or supposed rules, this remains a step too far – even if they might claim otherwise.