T-Mobile Probes Attack, Confirms Systems Were Breached
Cybercrime
,
Fraud Management & Cybercrime
Attackers Claim They Stole 36 Million Unique Customer Records

T-Mobile USA on Monday confirmed that its computer systems were illegally accessed, following reports of an apparent intrusion. But the Bellevue, Washington-based mobile communications subsidiary of Germany’s Deutsche Telekom says it’s still investigating whether customers’ personal customer data was exposed.
See Also: Live Webinar | Password Management: Securing Hybrid Work for the Long Haul
A seller in an online forum claims that 100 million personal records were taken from T-Mobile’s Systems, of which 36 million are unique. Part of the data, which consists of 30 million Social Security and driver’s license numbers, was put up for sale on the online forum for six bitcoins, worth about $286,000 (see T-Mobile USA Investigates Possible Data Breach).
The rest of the personal data purportedly includes names, addresses, birth dates and technical phone data such as International Mobile Subscriber Identity, or IMSI, and International Mobile Equipment Identity, or IMEI, numbers.
There are also allegedly security PINs, which are the secret numbers that customer service representatives ask for when a customer wants to, for example, get a replacement SIM card or move a number to a new carrier. Exposure of those numbers could put people at risk of so-called SIM swapping or hijacking attacks (see Gone in 15 Minutes: Australia’s Phone Number Theft Problem).
T-Mobile says it believes it has closed the entry point where the intruders gained access. Law enforcement has been contacted, and the company says it is undertaking an extensive analysis alongside digital forensic experts.
“This investigation will take some time but we are working with the highest degree of urgency,” according to a statement on the company’s website. “Until we have completed this assessment we cannot confirm the reported number of records affected or the validity of statements made by others.”
Noisy Attackers
Computer security and cybercrime analysts are closely examining the claims made by those close to the alleged breach. Those actors have been active on Twitter and other forums.
Analysts say the actors around the periphery of the intrusion appear to have been involved in telco-related hijinks such as SIM swapping and lookup services that match phone data with numbers. But ultimately it’s unclear in this case if they’re bluffing.
One person involved in the T-Mobile incident, who goes by the pseudonym Anton Lyashevesky and is apparently closely linked with a Twitter handle @und0xxed, told Information Security Media Group on Monday that the data is for sale and claimed that “multiple” parties are interested.
Negotiations seen by ISMG, however, suggest there is interest in selling the data for a far lower price than $286,000.
Lyashevesky claimed to ISMG that T-Mobile was compromised after the company left a Gateway GPRS Support Node, or GGSN, misconfigured and exposed to the internet. GGSNs are part of the core infrastructure that connect mobile devices to the internet. Lyashevesky says they had access to T-Mobile systems for two or three weeks until it was shut off on Saturday.
Lyashevesky claimed the attackers then pivoted to T-Mobile’s LAN and then eventually to more than 100 or so mostly Oracle databases containing user data. According to one tweet by @und0xxed, the data came from two T-Mobile data centers dubbed Polaris and Titan.
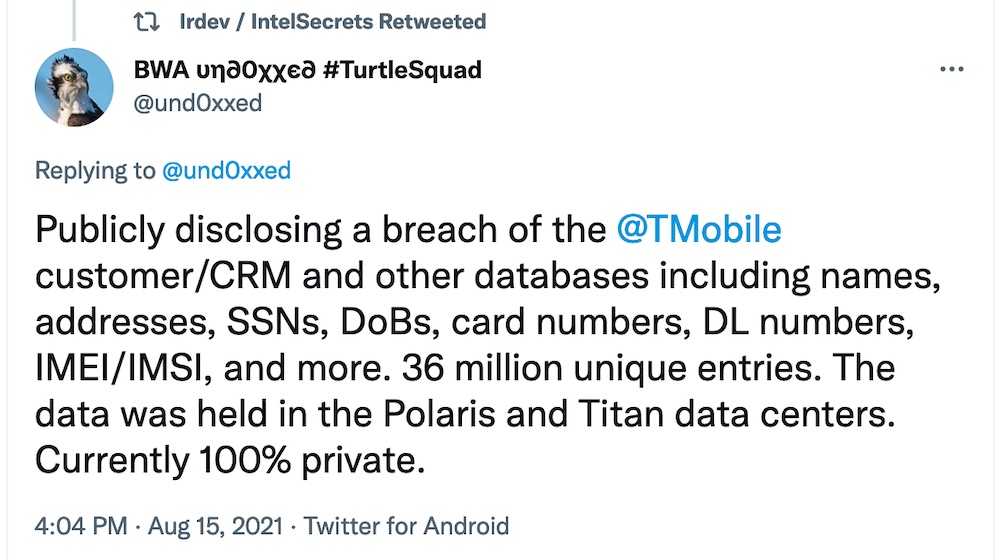
There certainly are potential security risks around GGSNs, which are the routers that stand between the telco’s network and the internet. Research presented at the Hack in the Box security conference in Malaysia in 2011 outlined some of the risks.
Whether that is the route that compromised T-Mobile remains to be seen. It may be possible to hack into a GGSN router, but it’s extremely unlikely that access could be parlayed into reaching all of the T-Mobile’s databases with customer data, says Gene Yoo, CEO of Resecurity. Also, there are no email addresses in the data.
Another handle wrapped up in the T-Mobile situation is @Intelsecrets. Lyashevesky claims to ISMG that @Intelsecrets is the person who actually hacked T-Mobile. The @und0xxed Twitter profile humorously lists @Intelsecrets as a co-defendant.
@Intelsecrets runs Intelsecrets[dot]su, a website that has been online for at least two years. That website also appears in the GitHub profile of someone calling themselves John Erin Binns, a name that also appears in the Twitter handle.
Yoo says that @Intelsecrets also been linked to another handle, v0rtex, which three years ago sold a lookup service that matched IMSI numbers with phone numbers from multiple carriers.
The data that is being offered now may be a mix of some T-Mobile data but also other data collected from third parties or commercial providers from that era, Yoo says. Samples of the data carry different prefixes, such as “tmo-cxline”, “tmo-crm” and “tmo-prepay2016.”
Efforts to reach @Intelsecrets weren’t immediately successful.
T-Mobile: Repeat Target
Given the circumstances of how the data was advertised and the threat actors involved, there’s a reasonable chance the data will end up being dumped publicly at some point, according to a cybercrime researcher who requested anonymity.
That’s in part because the alleged breach has been promoted by threat actors who have historically engaged in attention-seeking behavior. Fraudsters who buy databases value exclusivity, but when the media spotlight moves on, these sellers may not uphold their end of the bargain.
“The likelihood this data will go fully public is pretty high,” the researcher says. “If a potential buyer wants this, all they need to do is wait.”
T-Mobile has been repeatedly targeted by SIM swappers, the researcher says, and the attackers are persistent.
Sometimes, attackers will gain access to networks after repeatedly calling company employees, claiming to be from the company’s own technical support to try to get the employee to download a remote access trojan. Most of those attempts fail, but occasionally, it works, the researcher says.