Startup Probes Hack of Internet-Connected Security Cameras
Endpoint Security
,
Internet of Things Security
‘Arson Cats’ Researchers Say Device Flaws Gave Them Full Access to Verkada Cameras
Security researchers say vulnerabilities in a Silicon Valley startup’s internet-accessible surveillance cameras could have allowed them to gain full, remote access to all customers’ networks.
See Also: Illumination Summit: Poker & Cybersecurity: A Game of Skill, Not Luck
San Mateo, California-based Verkada, which manages and maintains 150,000 remotely accessible surveillance cameras for numerous organizations, says it’s investigating the remote access to its devices.
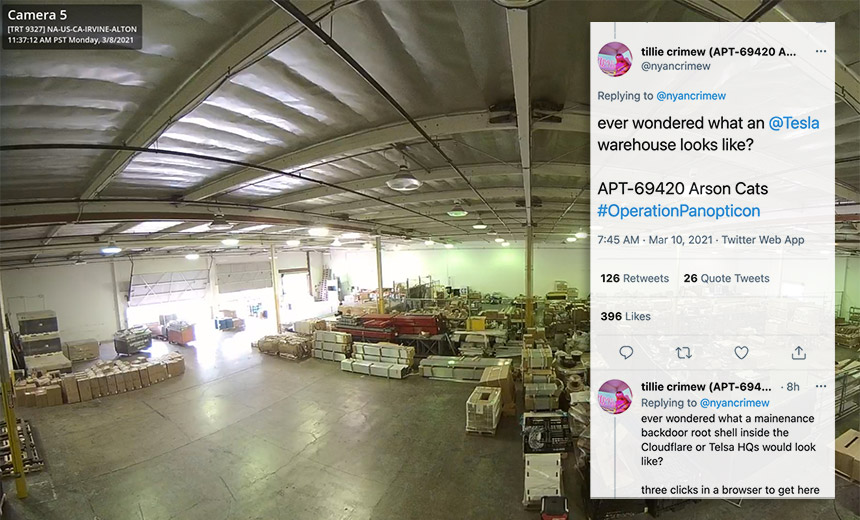
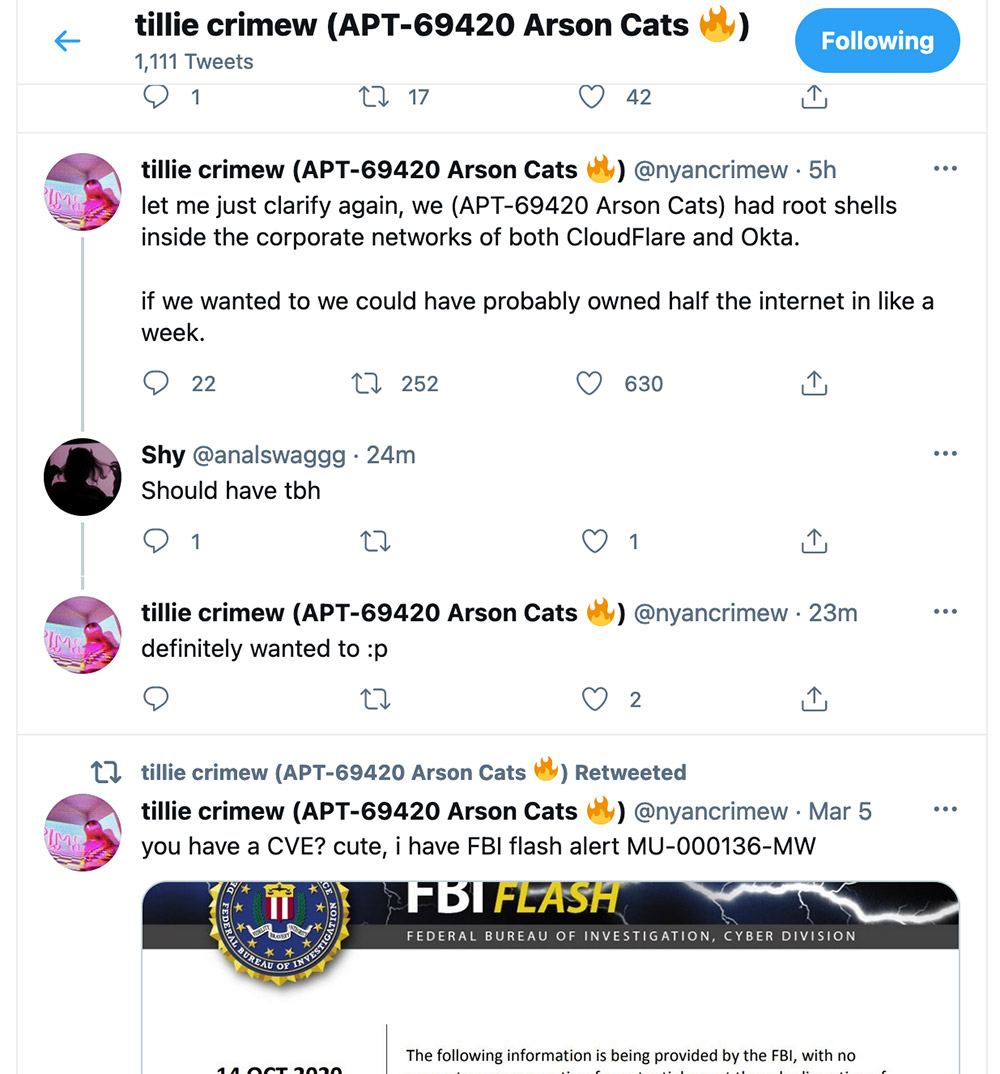
Tillie Kottmann, a Switzerland-based researcher and self-described member of the APT 69420 “Arson Cats” group – a tongue-in-cheek riff on the names cybersecurity firms assign to nation-state and cybercrime hackers they track – says the group on Monday was able to gain administrator-level access to Verkada cameras used inside facilities run by carmaker Tesla, web infrastructure firm Cloudflare and identity and access management vendor Okta as well as at Arizona’s Tempe St. Luke’s Hospital.
Verkada’s cameras are also used by other hospitals as well as schools, government agencies, prisons and more.
Verkada says it’s investigating. “We have disabled all internal administrator accounts to prevent any unauthorized access,” a spokesperson says in a statement. “Our internal security team and external security firm are investigating the scale and scope of this issue, and we have notified law enforcement.”
Kottmann says that as part of Arson Cats’ “Operation Panopticon,” they found in Verkada’s cameras “hardcoded credentials to a superadmin account in Jenkins, which gave us access to their web app with the superadmin tools which includes a button that opens a root shell in your web browser on whichever camera you pick.”
Jenkins is a Kubernetes-native platform for continuous integration and continuous deployments used to develop cloud-based applications. Verkada uses it as part of the technology stack built into its cameras. Gaining superadmin access to a root shell on a Verkada camera means the researchers could potentially have used it as a beachhead for obtaining full, remote access to every network in which Verkada cameras were being used.
The relatively wide deployment of Verkada’s cameras and the level of access the researchers were able to obtain led Kottmann to boast via Twitter: “I don’t think the claim ‘we hacked the internet’ has ever been as accurate as now. … I’m sorry for being so powerful.”
Kottmann’s Twitter account, @nyancrimew, which states “I would never do cybercrime” in the bio, has since been suspended by Twitter.
Hospitals and Prisons Affected
News of the researchers’ ability to hack Verkada cameras was first reported by Bloomberg, which said the group was able to view video – and in some cases audio – from numerous installations, including Madison County Jail in Huntsville, Alabama; a police station in Stoughton, Massachusetts; intensive care unit beds at a hospital in Texarkana, Texas; and many other sites.
Founded in 2016, Verkada calls itself a “cloud-based enterprise video security” firm. It offers surveillance as a service in the form of internet-connected security cameras that customers can remotely access, with some providing the high-definition resolution known as 4K. In January 2020, Verkada announced that it had secured $80 million in Series C financing and had a $1.6 billion valuation. Investors include venture capital giant Sequoia Capital, as well as Next47, Meritech Capital and Felicis Ventures.
Elisa Costante, vice president of research at network security firm Forescout, notes that “Verkada cameras are in widespread use within government and healthcare.”
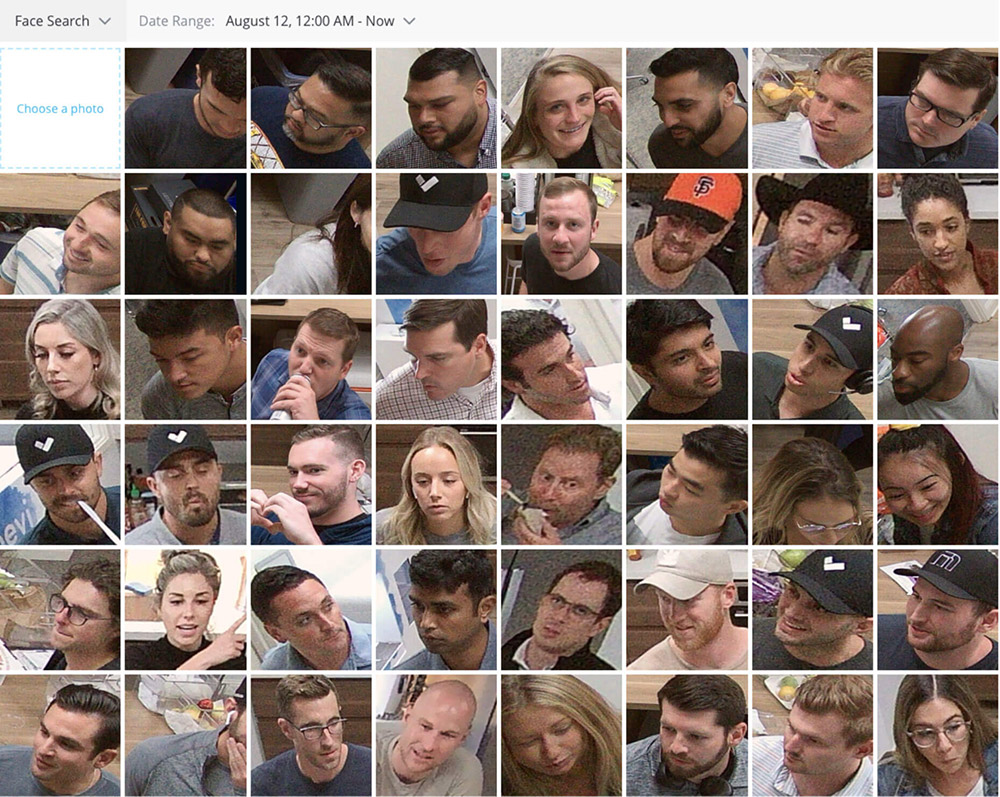
Verkada markets its ability to not only provide managed access to security cameras, but also to recognize faces and vehicles via its so-called people analytics and vehicles analytics features. For people, as described by Verkada in a blog post, the company says “users can search and filter based on many different attributes, including gender traits, clothing color, and even a person’s face.”
“Verkada positions itself as a ‘more secure, scalable’ alternative to on-premises network video recorders,” says Rick Holland, CISO at threat intelligence firm Digital Shadows. “The Verkada intrusion is an example of the risks associated with outsourcing services to cloud providers. You don’t always get more secure when you outsource your security to a third party.”
Customers Seek More Information
Reached for comment, some affected customers said they’re investigating and also seeking more information from Verkada.
A Cloudflare spokeswoman said in a statement that on Tuesday, “we were alerted that the Verkada security camera system that monitors main entry points and main thoroughfares in a handful of Cloudflare offices may have been compromised.” She added, however, that “the cameras were located in offices that have been officially closed for nearly a year” as the COVID-19 pandemic has continued.
“As soon as we became aware of the compromise, we disabled the cameras and disconnected them from office networks,” she said. “No customer data or processes have been impacted by this incident. While facial recognition is a beta feature that Verkada makes available to its customers, we have never actively used it nor do we plan to.”
Okta says it too learned on Tuesday “of a report around Verkada and Okta,” and notes that no services provided by Okta have been affected. “We are continuing to investigate the situation and will provide updates as relevant additional information becomes available,” a spokeswoman tells Information Security Media Group.
Tesla didn’t immediately respond to a request for comment.
Regulatory Impact Unclear
Security experts say Verkada – and its customers – will likely have to make numerous breach notifications to comply with HIPAA in the U.S. and the EU’s General Data Protection Regulation.
“The video leak is likely to result in regulatory investigations from the Department of Health and Human Services for HIPAA violations because surveillance footage can be considered protected health information,” Digital Shadows’ Holland says. “GDPR violations of personal data could have also occurred, and class-action lawsuits could also be on the horizon.”
‘I Have FBI Flash Alert’
Kottmann, who regularly hunts for exposed data or poorly secured systems, says those efforts have led to the FBI issuing an alert in October 2020 pertaining to the open-source continuous code inspection platform SonarQube, formerly known as Sonar. In that alert, the bureau warned that “vulnerable SonarQube instances” could be exploited “to access source code repositories,” and that “in August 2020, unknown threat actors leaked internal data from two organizations through a public lifecycle repository tool.”
In May 2020, Kottmann accessed and leaked nearly 9 gigabytes from Mercedes-Benz parent company Daimler AG’s software development documentation after Daimler misconfigured one of its GitLab repositories.
In August 2020, Kottmann posted 20GB of internal Intel corporate data – allegedly received from an anonymous hacker – to the Mega file-sharing service, saying that “most of the things here have not been published anywhere before and are classified as confidential, under NDA or ‘Intel Restricted Secret.'” Intel said the data appeared to have come from its Intel Resource & Design Center.
Managing Editor Scott Ferguson and Executive Editor Jeremy Kirk contributed to this report.