Electrical Grid’s Distribution Systems More Vulnerable
Business Continuity Management / Disaster Recovery
,
Endpoint Security
,
Governance & Risk Management
Audit Recommends Energy Department Implement Better Protections

The U.S. electrical grid’s distribution systems that deliver electricity directly to customers are increasingly vulnerable to cyberthreats, and the Department of Energy needs to do more to protect this critical infrastructure, according to a Government Accountability Office audit.
See Also: Live Webinar | Mitigating the Risks Associated with Remote Work
The GAO recommends that the Energy Department incorporate the grid’s distribution systems into its cybersecurity strategy that already includes the generation and transmission systems.
The Energy Department agreed with the recommendation, the audit notes.
Although the GAO says it’s not clear how threats against distribution systems might affect the grid, it points out that a “coordinated attack on distribution systems could cause outages in multiple areas even if it did not disrupt the bulk power system, according to officials from one national laboratory.”
Growing Cyber Concerns
The electrical grid’s distribution systems are increasingly connected to the internet through business networks and remote access tools, making them more susceptible to hacking and cyberthreats, the GAO found.
“As a result, threat actors can use multiple techniques to access those systems and potentially disrupt operations,” the watchdog report notes. “However, the scale of potential impacts from such attacks is not well understood.”
The GAO notes that these distribution systems – and the utilities that oversee them – are not subject to mandatory federal security standards. Some states and privately owned utilities, however, have started to incorporate more cybersecurity standards into the oversight of these distribution systems and are hiring more security staff, the audit report notes.
Although the Energy Department is planning to implement a national cybersecurity strategy for the entire U.S. electrical grid, the agency has so far paid too little attention to emerging threats that could target distribution systems and the supply chains that support them, the report notes.
“DOE has not fully addressed such risks in its plans because it has prioritized addressing risks to the grid’s generation and transmission systems,” the audit states. “Without doing so, however, DOE’s plans will likely be of limited use in prioritizing federal support to states and industry to improve grid distribution systems’ cybersecurity.”
In previous audits, the GAO found that other parts of the U.S. electrical grid, including generation and transmission systems, are also vulnerable to cyberthreats. Industrial control systems, which help power plants and utilities properly function, are also vulnerable to attack because of their remote access features, the GAO reports (see: GAO Raises Concerns About Power Grid Vulnerabilities).
Types of Attacks
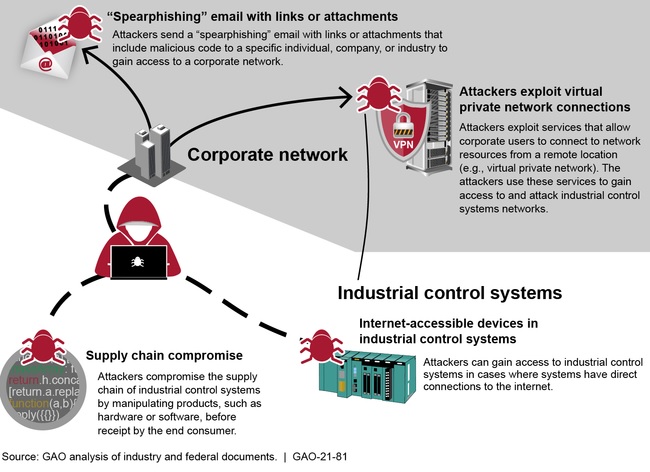
The GAO audit describes cyberthreats to which the grid’s distribution systems could be susceptible over the coming years, especially as more networks are connected to the internet through remote access tools. These include:
- Spear-phishing emails that contain malicious links or attachments and can serve as a way to gain initial access to a network and allow a hacker to maintain persistence.
- Attackers taking advantage of vulnerabilities in VPNs and other remote access tools to gain initial access to networks. Government agencies, such as the U.S. Cybersecurity and Infrastructure Security Agency, have warned about flaws in VPNs and other remote access tools (see: VPN Vulnerabilities Put Industrial Control Systems at Risk).
- Supply chain attacks in which a third-party vendor is compromised and attackers use this as a jumping-off point to target other infrastructure;
- Attacks targeting industrial control systems that are not “air-gapped” and are connected to the internet through networks on the business side of the utility.
“Connected industrial control systems now have given adversaries access to our distribution systems,” says Setu Kulkarni, vice president for strategy at WhiteHat Security in San Jose, California. “What is worse is that with such remote access, the relative anonymity and the potential safe harbor, adversaries do not have any deterrent to launching such malicious and potentially profound attacks.”
Remote Access Concerns
The recently thwarted attack against a water treatment facility in Florida illustrates that, indeed, hackers can use remote access tools to access industrial control systems (see: Hacker Breached Florida City’s Water Treatment System).
It’s difficult for organizations supporting critical infrastructure – whether it’s the electrical grid or water treatment – to take systems offline to conduct maintenance and ensure that remote access tools are properly configured, says Kevin Dunne, president of the security firm Pathlock.
“Many of these systems were built decades ago and are still secured through traditional methods, such as network design and role-based access control,” Dunne says. “Many aren’t adapted to today’s remote access environment, making them prime targets for hackers who can easily gain access to the network with compromised credentials and exploit these legacy systems.”






