Sprawling cyber-espionage campaign linked to Chinese military unit
Cybersecurity experts have uncovered evidence that interconnects several multi-year and sprawling cyber-espionage campaigns to a Chinese military unit operating out of the city of Ürümqi in China’s western province of Xinjiang.
According to a report released today by Recorded Future’s Insikt Group, the People’s Liberation Army (PLA) Unit 69010 is believed to have been behind a series of cyber-espionage campaigns dating back to 2014 that have focused on gathering military intelligence from neighboring countries.
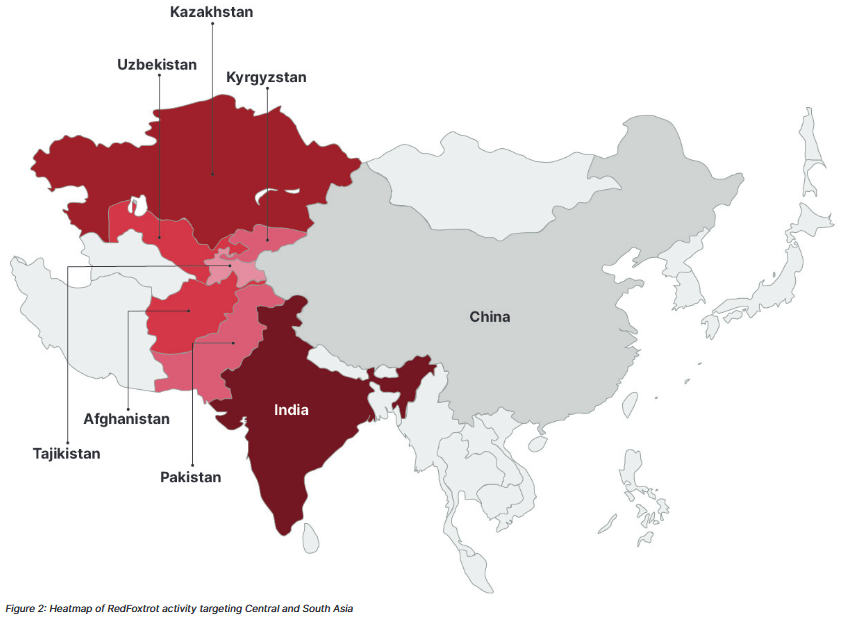
The attacks, which the Insikt Group has tracked under the RedFoxtrot threat actor codename, have targeted aerospace, defense, government, telecommunications, mining, and research organizations in Afghanistan, India, Kazakhstan, Kyrgyzstan, Pakistan, Tajikistan, and Uzbekistan.
“Notable RedFoxtrot victims over the past 6 months include multiple Indian aerospace and defense contractors; telecommunications companies in Afghanistan, India, Kazakhstan, and Pakistan; and several national and state institutions in the region,” analysts said today.
“Activity over this [past six-month] period showed a particular focus on Indian targets, which occurred at a time of heightened border tensions between India and the People’s Republic of China (PRC).”
Per the research team, for its attacks, the RedFoxtrot group used an assortment of malware families (IceFog, ShadowPad, Royal Road, PCShare, PlugX, and Poison Ivy) and web server infrastructure to host and deliver payloads and to collect stolen information.
Some of the group’s past campaigns have been previously documented by other security firms under different names in something that has become a common sight in modern-day threat hunting.
Over the past few years, the lines between Chinese state-sponsored hacking groups have blurred due to the reuse of malware strains among groups and the involvement of third-party contractors hired by the Chinese Ministry of State Security (MSS), which have conducted operations in parallel with China’s military hacking units.
OpSec mistakes leads investigators to PLA Unit 69010
Recorded Future researchers said they were able to make connections inside this nebula of Chinese state-sponsored hacking activity to RedFoxtrot (and subsequently to PLA Unit 69010) due to lax operational security (OpSec) measures of one of its members.
“Insikt Group is not publicly disclosing the identity of this individual; however, an extensive online presence provided corroborating evidence indicating that this individual is located in Ürümqi, has an interest in hacking, and also has a suspected historical affiliation with the PLA’s former Communications Command Academy (通信指挥学院) located in Wuhan,” the researchers said.

The team’s discovery comes two months after Japanese media reported—citing local law enforcement sources— that PLA Unit 61419 was behind a broad cyber-espionage campaign that breached more than 200 Japanese companies and organizations since at least 2016, which security researchers have linked to the Tick advanced persistent threat (APT) group.
These two recent attributions show that despite a recent wave of indictments that have linked Chinese cyber-espionage operations to the MSS and its local IT contractors, the Chinese PLA is still operating hacking units for its own campaigns and data collection goals.