SolarWinds Attackers Return With Fresh Phishing Campaign
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Microsoft: Russians Used Malicious Messages Portrayed as Coming From USAID
A Russian group that was behind the massive SolarWinds supply chain attack has returned with a fresh phishing campaign, according to Microsoft. This new campaign compromised a marketing firm used by the U.S. Agency for International Development – USAID – to send malicious messages to thousands of potential victims.
See Also: Top 50 Security Threats
Microsoft attributes this latest phishing campaign to an attack group that the company calls Nobelium, which also conducted the SolarWinds supply chain attack, which affected 18,000 users of the Orion network monitoring platform and resulted in follow-on attacks on nine government agencies and 100 companies. The U.S. government has accused Russia’s Foreign Intelligence Service, or SVR, of conducting the SolarWinds supply chain compromise.
Phishing Campaign
In the new campaign that Microsoft uncovered, the attackers gained access to the Constant Contact email marketing account of USAID and sent out messages that contained a malicious link that would install a backdoor dubbed “NativeZone” on victim’s devices, according to Microsoft’s research report.
Constant Contact is a third-party email marketing firm based in Waltham, Massachusetts.
While it’s not clear how successful this new campaign has been, Microsoft security researchers note that it was still active as of Tuesday, and the attackers appear to have targeted about 3,000 email accounts at 150 organizations – most of which are involved in international development, humanitarian and human rights work.
While most of the targeted victims were located inside the U.S., Microsoft says the phishing campaign also targeted organizations in at least 20 other countries.
CISA, FBI Investigating
The U.S. Cybersecurity and Infrastructure Security Agency, along with the FBI, is investigating the phishing campaign, a CISA spokesman says.
“We are aware of the potential compromise at USAID through an email marketing platform and are working with the FBI and USAID to better understand the extent of the compromise and assist potential victims,” the CISA spokesman told Information Security Media Group on Friday.
A spokesperson for Constant Contact says: “We are aware that the account credentials of one of our customers were compromised and used by a malicious actor to access the customer’s Constant Contact accounts. This is an isolated incident, and we have temporarily disabled the impacted accounts while we work in cooperation with our customer, who is working with law enforcement.”
Microsoft believes that most of the phishing emails were stopped by security tools before they reached victims. But this latest attack shows that attackers with links to Russia continue to attempt new methods to compromise networks.
“When coupled with the attack on SolarWinds, it’s clear that part of Nobelium’s playbook is to gain access to trusted technology providers and infect their customers,” says Tom Burt, corporate vice president for customer security and trust at Microsoft. “By piggybacking on software updates and now mass email providers, Nobelium increases the chances of collateral damage in espionage operations and undermines trust in the technology ecosystem.”
U.S. and Russia
The revelation of the latest Russian attack comes just weeks after the Biden administration issued economic sanctions against Russia’s SVR, along with individuals and companies that the White House believes assisted in the SolarWinds campaign and interfered during the 2020 U.S. elections (see: US Sanctions Russia Over SolarWinds Attack, Election Meddling).
President Joe Biden is slated to meet with Russian President Vladimir Putin during a summit in Geneva, Switzerland on June 16, according to the White House.
On May 12, Biden issued a sweeping executive order designed, in part, to implement measures designed to help counter the type of supply chain attack that compromised SolarWinds (see: Biden’s Cybersecurity Executive Order: 4 Key Takeaways).
Wake-Up Call
Phishing campaigns with suspected ties to nation-state attackers should serve as a reminder for organizations to implement better security procedures, such as establishing least privilege access to networks and creating resilient systems that can respond and recover from these types of compromises, says Sam Curry, chief security officer at Cybereason.
“The asymmetry in cyber conflict favors attackers and, so far, the attackers are getting more effective at a faster rate than defenders are,” Curry says. “This is not a cause for despair, but it is a wake-up call for innovation and to find new methods of working together and of countering them. There is a call to arms to all of us to protect the connected world and to reverse this trend. There are ways to be safe and to boost our mutual protection, but simply doing more of the same is a recipe for disaster.”
Curry cautions against too rapidly attributing the phishing attack to any group.
“The Biden administration has come out strongly with rhetoric about foreign – and specifically Russian – aggression. But behind the scenes, I hope that they are judicious in taking offense or retributive measures and that they will proceed when they have a preponderance of the evidence,” Curry says.
How Phishing Campaign Evolved
Microsoft notes that the latest phishing campaign differs significantly from the campaign that targeted SolarWinds, which ran from early 2019 until December 2020, when security firm FireEye discovered the attack.
The latest phishing campaign started in January when the attackers began using Google Firebase – a smartphone and web app development platform – to start sending phishing emails to potential victims to see if users would open the messages, Microsoft says. These early emails did not contain any malicious links or files and appear to have been part of early reconnaissance by the group, according to the research.
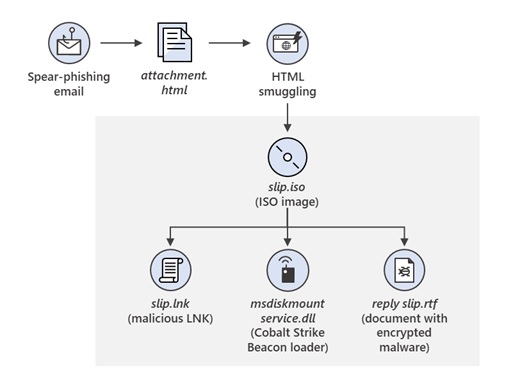
After the reconnaissance phase, the attackers began sending other spear-phishing emails with an HTML file attached to the message. If this email was opened by a user, JavaScript within the HTML would write an ISO file to the device’s disc and a message would then encourage the victim to open the file, Microsoft reports. If opened, a shortcut file would then execute a Dynamic Link Library file that would launch a Cobalt Strike Beacon within the compromised device.
Starting in March, Microsoft’s researchers found the attackers were experimenting with other techniques to deliver malicious files and links to potential victims. For instance, the group removed the ISO files from the Firebase host and began encoding them within the HTML file directly. In another case, an ISO file containing a Rich Text Format document would hide the Cobalt Strike Beacon. Another phishing email showed that the HTML file was replaced with a URL that led to a spoofed website that hosted the malicious ISO file.
USAID Phishing Emails
In April, the attackers settled on an HTML and ISO combination embedded within the phishing emails, but malicious code also contained a custom .NET first-stage implant that could conduct reconnaissance of a device and fetch other files from a Dropbox account, according to Microsoft.
These phishing messages began appearing in May, but it wasn’t until May 25 that the attackers attempted a large-scale email campaign that used the compromised Constant Contact accounts to target the 3,000 inboxes. Due to the large number of emails, most of the messages were blocked by security tools, Microsoft notes.
The report does not indicate how the attackers initially compromised Constant Contact to then take over the USAID account.
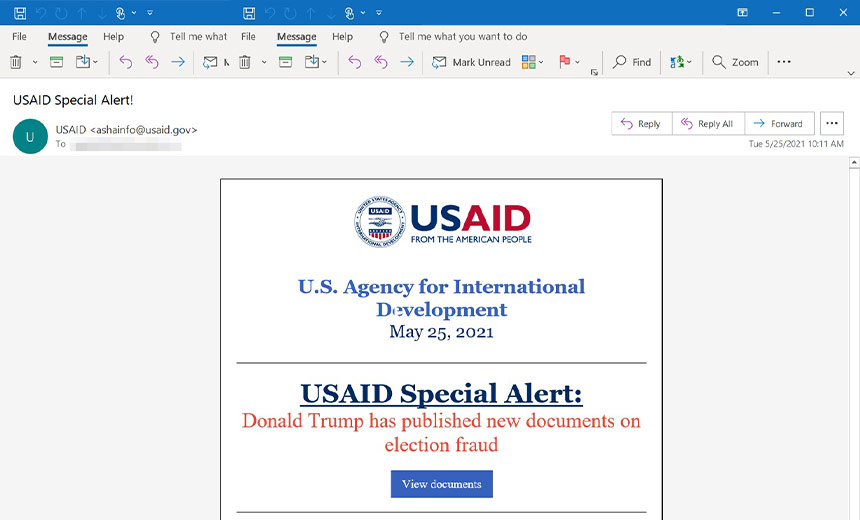
These USAID-themed phishing emails, however, had authentic sender email addresses that matched the standard Constant Contact service and appeared legitimate. In one example, the malicious email contained a message called “Donald Trump has published new documents on election fraud” in an attempt to get a user to click, Microsoft notes.
If the file was open or the link clicked, the user would be first sent to a legitimate Constant Contact service but then redirected to a landing page controlled by the Nobelium attackers. From there, the attackers attempted to install the NativeZone backdoor, which is a customized Cobalt Strike Beacon loader, according to the report.
“The successful deployment of these payloads enables Nobelium [the attackers] to achieve persistent access to compromised systems. Then, the successful execution of these malicious payloads could enable Nobelium to conduct action-on objectives, such as lateral movement, data exfiltration and delivery of additional malware,” Microsoft says.
SVR ‘Calling Card’
In a research note published Friday, John Hultquist, vice president of analysis at Mandiant Threat Intelligence, notes that his research team also began seeing these types of phishing emails in March, including some that spoofed diplomatic notes and invitations from embassies. He also notes that these types of phishing campaigns were once the hallmark of Russian SVR cyber operations.
“Though the SolarWinds activity was remarkable for its stealth and discipline, loud, broad spear-phishing operations were once the calling card of SVR operators who often carried out noisy phishing campaigns,” Hultquist notes. “Those operations were often effective, gaining access to major government offices among other targets. And while the spear-phishing emails were quickly identified, we expect that any post-compromise actions by these actors would be highly skilled and stealthy.”