Silver Sparrow Malware Infects 30,000 Macs
Cybercrime
,
Endpoint Security
,
Fraud Management & Cybercrime
Called Serious Threat, But Has Yet to Take Malicious Action

A previously undetected malware variant has infected almost 30,000 Apple Macs. But researchers so far have not seen it deliver any malicious payloads to compromised endpoints, according to a new report.
See Also: Top 50 Security Threats
The malware, dubbed Silver Sparrow, is being investigated by security teams from Red Canary, Malwarebytes and VMware Carbon Black. While the malicious code has not revealed its true colors yet, researchers do believe that Silver Sparrow is a serious threat.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate, and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice,” says Red Canary’s Tony Lambert.
Two versions of the malware have been spotted. Version one contains a Mach-O binary compiled to only target Intel x86-64 architecture. Version two adds a Mach-O binary compiled for Apple’s latest microprocessor architecture, the M1 ARM64, the report says.
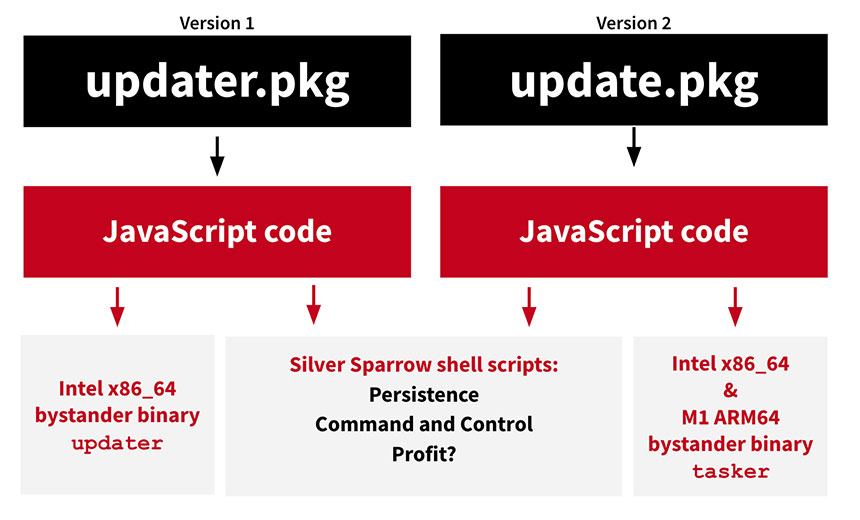
“The Mach-O compiled binaries don’t seem to do all that much – at least not as of this writing – and so we’ve been calling them ‘bystander binaries,'” Lambert says.
Several aspects of the malware remain a mystery, including its ultimate goal, its distribution method and even when it first appeared.
The researchers point to Aug. 18, 2020, as the first time version one’s callback domain api.mobiletraits[.]com appeared. The next indicator came on Aug. 31, 2020, when version one was submitted to VirusTotal. Version two was submitted the following month. Red Canary detected version one in the wild on Jan. 26 and version two on Feb. 9.
Silver Sparrow and JavaScript
The most unique aspect of Silver Sparrow, Lambert says, is that its installer packages use the macOS installer JavaScript API to execute its commands.
“While we’ve observed legitimate software doing this, this is the first instance we’ve observed it in malware,” Lambert says. “This is a deviation from behavior we usually observe in malicious macOS installers, which generally use preinstall or post-install scripts to execute commands.”
The next distinctive point, the researchers note, is that despite pinging the malware’s command-and-control server on an hourly basis, no response was ever received. Lambert and his fellow researchers observed the malware for a week, and at no time was a malicious payload sent to an infected device.
“We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution,” Lambert says.
The distribution method is also not well understood. It is suspected that the threat actors use malicious search engine results to direct victims to download the PKGs because they don’t have the visibility to determine exactly what caused the download.
Silver Sparrow’s infrastructure is hosted on Amazon Web Services S3 buckets and Akamai CDNs. Lambert says this allows the malware’s operators to have a highly available and resilient file distribution method. They can create a bucket and serve out files without any administrative worries or additional cost.
Tim Mackey, principal security strategist at the research firm Synopsys, notes the operator’s current use of Amazon and Akamai indicate other cloud services could also be used.
“The trick in this context is to understand what normal activity looks like for the applications powering your business. Knowing which APIs and cloud services endpoints represent legitimate accesses helps immensely when mitigating data leakage from within an organization,” Mackey says.
Bystander Binaries
As Lambert noted, the binaries that target the Intel and Apple ARM M1 processors do not play a major role in the malware operation. The operating theory is each is used as placeholder content to give the PKG something to distribute when the JavaScript is executed.
What each binary does do is deliver a message. Version one, the one targeting Intel, says, “Hello, World” on a dark background. The second version’s note says, “You did it” on a red background, according to the report.
The messages could indicate a threat is under development and are being presented as a proof of concept that the malware works, Lambert says.
Apple’s M1 chip is also the focus of another malware strain. Independent macOS security researcher Patrick Wardle notes the Mac application called GoSearch22 is malicious adware disguised as a Safari extension. He says the malware is capable of stealing browser data from its victims and acts as a persistent agent for further compromise (New Malicious Adware Exploits Apple M1 Chip).