Chinese Hacking Group ‘Cloned’ NSA Exploit Tool
Researchers: ‘Jian’ Hacking Tool Targeted Zero-Day Flaw in Windows

A Chinese hacking group reportedly “cloned” and deployed a zero-day exploit developed by the U.S. National Security Agency’s Equation Group before Microsoft patched the Windows vulnerability that was being exploited in 2017, according to an analysis published Monday by Check Point Research.
See Also: Top 50 Security Threats
For several years, researchers had suspected the Chinese hacking group known as APT31 or Zirconium had developed an exploit tool to take advantage of a vulnerability tracked as CVE-2017-0005 and found in older versions of Windows, such as Windows 7 and Windows 8, according to the report.
The new Check Point research, however, demonstrates how the Chinese hacking group reportedly stole, cloned and then exploited a zero-day vulnerability created by the Equation Group, which is widely believed to be tied to the NSA’s elite Tailored Access Operations team.
The report also raises additional questions about how some of the NSA’s most prized cyber weapons have been discovered or stolen by nation-state hacking groups and then turned on their developers over the years. In May 2019, Symantec published a similar report that found another group of hackers had stolen and exploited cyber tools developed by the NSA (see: Report: Chinese Hackers First to Use NSA Cyberattack Tools).
Both the Symantec and Check Point research show that the theft of NSA Equation Group tools by these groups appears to have happened before the hacking group known as the Shadow Brokers first began publishing the agency’s exploits in 2016 (see: Shadow Brokers Says ‘Trick or Treat’ Over Attack Tool Leak).
“The Shadow Brokers leak, however, just gave us a taste of some of the possible implications such a cyber theft can cause. Many important questions still remain – could this have also happened before? And if so, who is behind it and what did they use it for?” Check Point researchers Eyal Itkin and Itay Cohen write in the report.
“Our recent research aims to shed more light on this topic, and reveal conclusive evidence that such a leak did actually take place years before the Shadow Brokers leak, resulting in U.S. developed cyber tools reaching the hands of a Chinese group which repurposed them in order to attack U.S. targets,” the two researchers note.
An NSA spokesperson declined to comment on the report Monday.
Questioning NSA’s Role
The latest report by Check Point not only shows the dangers of what happens when the NSA’s tools are stolen by nation-state hacking groups, but also the flaws with the Vulnerabilities Equities Process, a U.S. government program that discloses software vulnerabilities to vendors so they can be patched, says Scott Shackelford, chair of Indiana University’s cybersecurity program.
“The Biden administration would be well advised to take a fresh look at the U.S. Vulnerabilities Equities Process created by the Obama administration, particularly the role played by the NSA in weighing how and when to disclose discovered vulnerabilities back to vendors,” Shackelford says. “The Trump administration’s decision to give the NSA a larger role in Vulnerabilities Equities Process, in particular, seems to have been ill-advised.”
Jian
Security research previously noted that the APT31 hacking group first developed a zero-day exploit for CVE-2017-0005, called “Jian,” in 2014 and initially deployed it in 2015. The exploit was used for two years before Microsoft finally issued a patch for it in 2017. If exploited, this bug could allow an attacker to escalate privileges within a compromised device and then gain full control, the researchers note.
Microsoft published its patch for CVE-2017-0005 in March 2017, when the company was forced to issues multiple fixes for the exploits related to the Shadow Brokers’ “Lost in Translation” leak, Check Point notes.
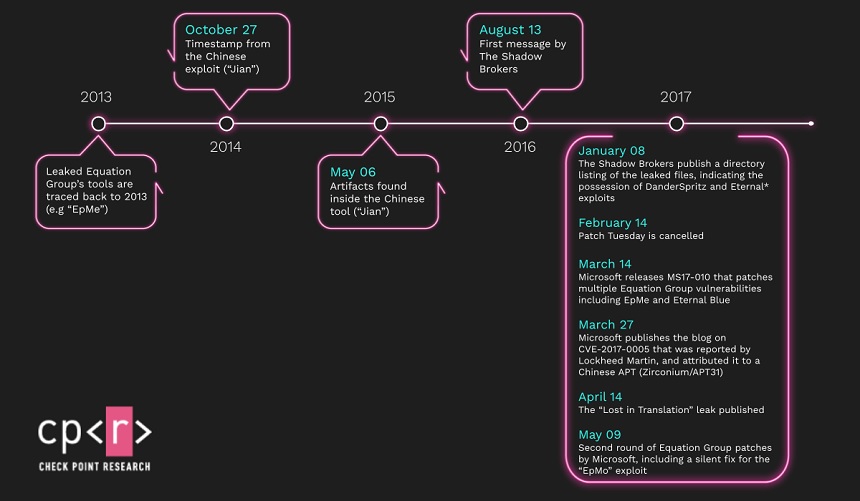
A further investigation by Check Point found that Jian was not an original creation, but a clone of a zero-day exploit for older versions of Windows developed by the NSA Equation Group in 2013 and originally called “EpMe” by the agency, according to the new report.
The Check Point research shows that the APT31 hackers gained access to both the 32-bit and 64-bit versions of the EpMe exploit more than two years before the Shadow Brokers leak become public in 2016.
A further investigation of Jian found a module within the exploit that had similarities to DanderSpritz, a modular post-exploitation framework created by the NSA Equation Group that contains dozens of interdependent modules, according to the Check Point report.
This framework also contained several zero-day exploits that targeted Windows and other Microsoft products. They include EpMe, which is similar to Jian, as well as another zero-day exploit called “EpMo,” which Microsoft patched in May 2017, although the company didn’t assign a CVE number to the vulnerability, the report notes.
A Check Point researcher notes that when APT31 copied that EpMe code, the hackers didn’t realize that the exploit had certain limitations.
“Jian contains several code snippets that show that its developer wasn’t fully aware of the nature and limitations of the exploited vulnerability, such as trying to support Windows 2000 which isn’t even vulnerable,” the Check Point researcher tells Information Security Media Group. “This Windows 2000 support makes sense in Equation Group’s exploit as it is a shared module with another Equation Group exploit – EpMo – which indeed supports this Windows version. The futile attempt of Jian to support Windows 2000 looks like a classic case of copying code without fully understanding how it works and if it is even necessary.”
How Did It Happen?
What is not clear is how APT31 first obtained the source code for EpMe that it eventually refashioned into Jian, according to the report.
There are several possibilities, including that APT31 captured the exploit code during an Equation Group network operation on a Chinese target, or the hackers found an Equation Group operation on a third-party network, which was also being monitored by Chinese intelligence, according to the researchers.
A third possibility, although more remote, is that the Chinese hackers found the zero-day exploit during an attack on Equation Group infrastructure, Check Point says.
David Brumley, a professor of electrical and computer engineering at Carnegie Mellon University, notes that when it comes to cyberespionage, these types of incidents are likely to keep happening since any exploit can be captured and studied by those it targets.
“In reality, the Chinese group did the cyber equivalent of copying a movie or music file. Attacks and exploits are different from physical weapons. They’re just bits on a wire, and anyone can copy them and reuse them,” Brumley says. “Every time the U.S. uses an exploit, they are potentially showing others a new – unknown to them – capability. Similarly, every time Russia hacks the U.S., we may learn a new exploit.”
American Targets
It’s also not clear which organizations APT31 may have targeted using the Jian exploit. The Check Point report notes that Lockheed Martin’s Computer Incident Response Team was the first to report the vulnerability to Microsoft.
The fact that the vulnerability was discovered by a defense contractor could indicate that the hacking group was planning “a possible attack against an American target,” the Check Point researchers note.




