Ransomware Gangs ‘Playing Games’ With Victims and Public
3rd Party Risk Management
,
Business Continuity Management / Disaster Recovery
,
Critical Infrastructure Security
‘Free’ Decryptors and Promises of Retirement Plans Are Empty Criminal Marketing Spin

Rule when analyzing cybercriminals: Don’t trust anything they say.
See Also: New Priorities for IT Operations: Be Ready for Whatever Comes Next
After disrupting Colonial Pipeline Co., which supplies fuel to 45% of the U.S. Eastern Seaboard, the DarkSide gang announced on May 13 that it would be ceasing operations. It’s also offering for sale a bridge in Brooklyn.
“They’re playing games.”
The most sophisticated ransomware-wielding gangs today are masters of PR and marketing spin (see: Charm Offensive: Ransomware Gangs ‘Tell All’ in Interviews).
When ransomware syndicates began racking up victims in the healthcare sector in the early days of the COVID-19 pandemic, some promised to revise their rules of engagement. They would avoid targeting healthcare entities and provide “free” decryptors to anyone they hit. (More on so-called free tools for addressing criminal damage in a moment.)
When it debuted last August, DarkSide said its operators already had extensive experience. “We are a new product on the market, but that does not mean that we have no experience and we came from nowhere,” the group said in a press release. By the time of DarkSide’s supposed exit, blockchain analysis firm Elliptic said the gang had amassed at least $90 million from 47 victims. (Before the gang’s Tor data leak site went dark, it had listed 99 victims.)
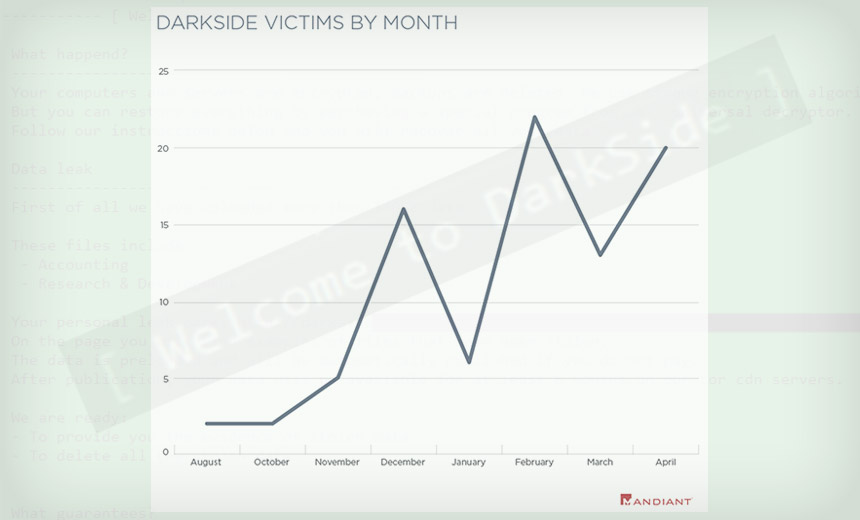
Even if the DarkSide brand disappears, its various members – whoever runs the operation, develops its malware, recruits affiliates to infect victims and share in profits – will be back. Their affiliates, in the meantime, will continue to work with whichever ransomware-as-a-service operations offer it the best malware or most generous terms.
US Federal Cybersecurity Improvements
DarkSide may have managed to do something unrivaled in history: It helped drive the release of an executive order signed by President Joe Biden mandating baseline cybersecurity standards for all federal agencies. (Extra special credit should also go to SolarWinds for failing to spot and disrupt one of the worst supply chain attacks in history, at the U.S. government’s expense.)
Former top U.S. cybersecurity official Chris Krebs told CBS’ “Face the Nation” that “the benefit here is that typically executive orders really only apply to the federal government, and what we’re going to see is through the power of the purse, through the purchasing apparatus of the United States government in the software from U.S. tech companies and others, we’re going to see improved security standards and improved security performance.”
That’s great news, if it helps – and hopefully it will. But in the meantime, the hits keep on coming, and much more must be done to stop them.
Irish Health Services Disrupted
Last week, attackers wielding Conti ransomware attacked Ireland’s state-run health services provider, the Health Service Executive. Patient care throughout the country continues to be disrupted.
On Thursday, the attackers gave a decryptor to HSE, which says it will test the code to ensure it isn’t malicious before handing it to government incident response teams.
“The decryption key to unlock the data has now been made available,” Stephen Donnelly, Ireland’s health minister, said Thursday. “No ransom was paid by the Irish state.”
Criminal Gifts are Never ‘Free’
Some reports note that the decryptor was provided by attackers for “free” to the victim.
It would be more accurate to say that a crime syndicate seeking illicit profits no matter the cost to society, after disrupting a victim’s network, gave them a tool that might – or might not – help them restore their network in an attempt to make what they’d done look a bit less egregious.
One analogy: A mugger who shoots a victim during a botched robbery attempt agrees to pay for their hospital care. But there’s no easy fix for how long it takes the victim to recover, and there are broader implications for those around them.
In the case of the attack against HSE, Irish doctors say they’re unable to obtain even some of the most basic services, such as blood tests. Chemotherapy has also had to be rescheduled. Such disruptions can easily cost lives.
Furthermore, crypto-locking malware and decryptors are not magical pieces of software. In many cases, security experts warn, the malware can shred the data it’s attempting to encrypt, meaning not all ransomware-locked files can be decrypted. Decryptors can also fail to restore files back into folder hierarchies, meaning that even if they do get restored, victims must still figure out where they all go, which can add weeks or months to cleanup efforts.
Cybercrime Thrives in the Dark
The Conti-wielding criminals are still demanding a $20 million ransom, or they’ve threatened to dump 700GB stolen data. “Giving the key is some attempt to obtain moral brownie points as they’ve been attacking a health service,” says Alan Woodward, a professor of computer science at the University of Surrey, via Twitter. “They’re playing games.”
Ciaran Martin, Britain’s former cybersecurity chief, says the simple fact is that attackers have been caught out. “Ransomware works best for the criminals when private companies pay in secret,” Martin says via Twitter. “Attacking a state healthcare system in the full glare of publicity is not good ‘business.'”
Suspect Conti are under pressure from someone – maybe the Russian government or other criminals. Ransomware works best for the criminals when private companies pay in secret. Attacking a state healthcare system in the full glare of publicity is not good ‘business’ https://t.co/emaY5qdpnT
— Ciaran Martin (@ciaranmartinoxf) May 21, 2021
The Irish government on Thursday obtained a court order to block the illegal use of the stolen data. How that might work in practice, however, remains to be seen.
What Can Be Done?
Colonial Pipeline’s CEO confirming that his company paid a $4.4 million ransom because “it was the right thing to do for the country,” and now the HSE attack, have only intensified questions about whether ransomware payments should be outlawed or curtailed, gangs targeted and the role of cyber insurance – which will sometimes reimburse ransom payments – rethought. Perhaps if ransomware payoffs are allowed, declaring ransom payments publicly should become mandatory.
These are not new questions. Unfortunately, there are no easy answers. But it’s good that they’re being asked now in much more public forums.
Market forces might also help. Insurers cannot stay in business if they continue to pay ransoms. But depriving businesses of a safety net could be calamitous (see: As Ransomware Booms, Are Cyber Insurers Getting Cold Feet?).
As a spokesman for the Association of British Insurers told me in January: “If this insurance was not available, then firms who do the right things to protect themselves and are still hit could face financial ruin or possibly go out of business.”
Governments cracking down on cryptocurrency could also blunt the flow of funds to ransomware-wielding gangs.
Martin, the former head of GCHQ’s National Cyber Security Center who is now an Oxford University professor of practice in the management of public organizations, recommends full government policy reviews that don’t immediately rule out any strategy. He’s also previously suggested that one answer might be to allow government intelligence agencies to hack cybercrime syndicates, akin to how the White House tasked Cyber Command with disrupting Russia’s Internet Research Agency troll farm ahead of the 2018 U.S. midterm elections (see: Ransomware: Should Governments Hack Cybercrime Cartels?).
Writing in Lawfare earlier this year, Martin noted that such tactics have “been used against transnational cybercriminals in the past and should, in my view, be deployed where possible against the scourge of ransomware.”
At this stage of discussions, governments need to put everything on the table, and they need to do it now. Otherwise, trust ransomware-wielding criminals to continue their pursuit of illicit profits unchecked.






