Ransomware Cleanup Costs Scottish Agency $1.1 Million
Breach Notification
,
Business Continuity Management / Disaster Recovery
,
COVID-19
Conti Ransomware Gang Hit Scottish Environment Protection Agency on Christmas Eve

How much does it cost to recover from a Conti ransomware gang’s attack?
See Also: Live Webinar | Attacks on Cloud Infrastructure
For the Scottish Environment Protection Agency, so far the cleanup from a December 2020 attack has cost nearly 790,000 pounds ($1.1 million), according to figures obtained by the BBC under freedom of information law. Of that amount, it reports that $635,000 was spent to stabilize the agency’s IT platform.
SEPA is the Scottish government’s principal environmental regulator. The nondepartmental public body – meaning it largely operates independently – has a staff of about 1,200.
The agency says attackers began crypto-locking its systems “at one minute past midnight on Christmas Eve” after having already infiltrated SEPA’s network, stolen data and prepositioned its malware on multiple systems. The Conti gang has publicly taken credit for the attack – first listing SEPA on its data leak site and later leaking stolen data – to pressure the organization into paying a ransom.
Conti’s “news site” now lists 4,150 stolen files that it has leaked online, which it says is everything it obtained from the agency. The BBC reports that the stolen data includes “contracts, strategy documents and databases.”
On a dedicated site created by SEPA to describe its response to the attack and current service levels, the agency notes that the attack “significantly impacted our contact center, internal systems, processes and communications
“Following the attack, we immediately enacted our business continuity arrangements and took immediate action to limit the impact of the cyberattack, notifying relevant authorities, including Scottish Government, Police Scotland, the National Cyber Security Center and the Information Commissioner’s Office, with whom we continue to work,” SEPA says.
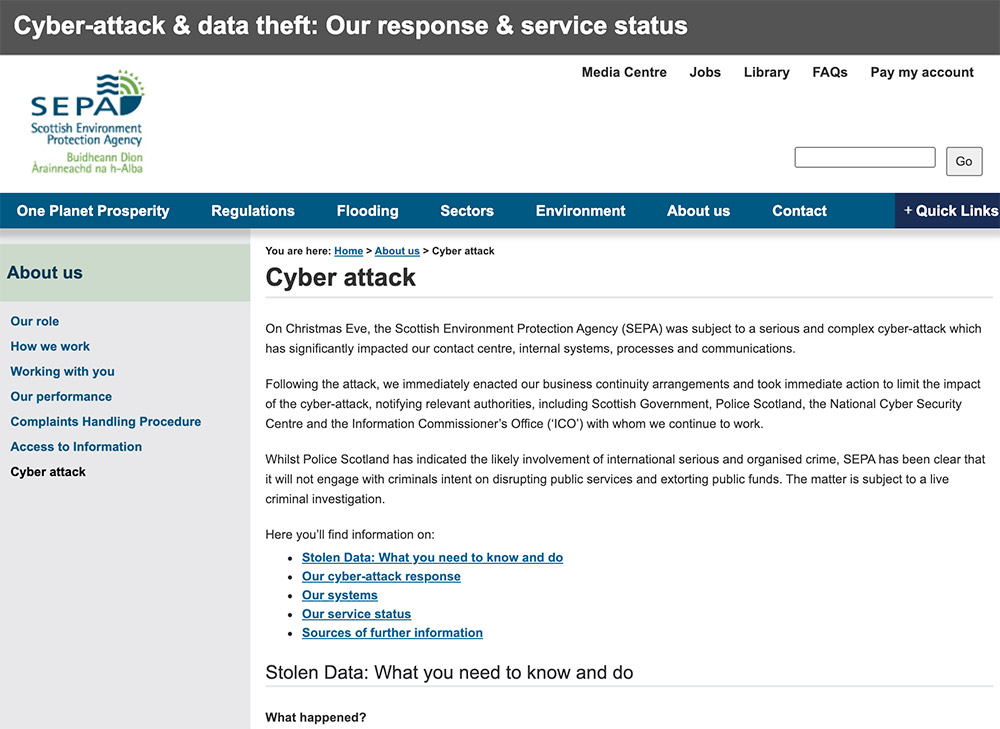
SEPA says is has not – and will not – pay a ransom to the attackers. “Whilst Police Scotland has indicated the likely involvement of international serious and organized crime, SEPA has been clear that it will not engage with criminals intent on disrupting public services and extorting public funds,” it says. “The matter is subject to a live criminal investigation.”
Detective Inspector Michael McCullagh tells the BBC: “Police Scotland is continuing to work closely with SEPA to investigate and provide support in response to this incident. The actions of the criminals behind this crime show a blatant disregard for public safety, evident in this sickening attack on an organization like SEPA.”
Attackers Struck on Christmas Eve
The timing of the attack – coming to light on Christmas Eve, ahead of a long holiday break in Scotland – is a reminder that ransomware-wielding criminals will often seek to hit organizations at a time designed to stoke maximum chaos and disruption to add further pressure on victims to pay (see: Hackers Love to Strike on Saturday).
The choice of target is also notable, in that SEPA provides flood forecasting and also warnings, which are essential alerts that help communities and emergency responders. At the same time, the agency also faces challenges in shifting to a post-EU regulatory system now that the U.K. has exited the EU.
SEPA says attackers stole 1.2GB of data and that it’s still analyzing the information. “Our priority is to identify the information that is personal data and/or commercially sensitive,” it says, and to work with anyone who’s affected to try to minimize any risk. “The information that was published online may include some personal data of our staff, of our customers and of the people with whom we work. We recognize that this news will cause concern, and we’re very sorry that this has happened.”
From a security standpoint, the agency warns anyone whose data might have been exposed to beware of unusual phone calls or emails, because criminals might use the leaked data to try to wage socially engineered schemes against individuals.
Restoration Work Continues
SEPA says it continues to restore systems. “Online pollution and inquiry reporting has been restored, but our email systems, staff schedules, some data products and reporting tools remain impacted and offline,” it says. While email access will be restored in a phased manner, the agency warns that due to the email backlog and ongoing coronavirus pandemic, the disruption could be felt for some time yet.
“We’ve said that whilst for the time being we’ve lost access to most of our systems, what we haven’t lost is the knowledge, skills and experience of our 1,200 expert staff,” the agency says.
“Whilst we initially lost access to our data and systems, what we didn’t lose was the expertise of our 1,200 staff,” says Terry A’Hearn, SEPA’s chief executive. “Since Christmas Eve, teams across the agency have been working flat out to support our people, partners and customers and to restore our systems services as quickly as possible. Our clear recovery strategy is gradually seeing systems being restored.”
SEPA says more than 70% of all staff should now be back online. “We’re engaging data recovery specialists and are confident that we will recover the most important data,” A’Hearn says.
Scotland: Incident Response Helpline
For any organizations in Scotland that suffer an online attack, the public-private Scottish Business Resilience Center, together with the Scottish government and Police Scotland, maintains a cyber incident response helpline to help organizations immediately triage and mitigate the incident, access appropriate resources and restore systems.
“If you feel that you are a victim of a cyberattack your first call should be to Police Scotland on 101 to report the crime – whilst respecting your IT systems as a crime scene,” followed by contacting the hotline, says Jude McCorry, CEO of the SBRC.
“We will assist you with immediate support and expert guidance, and ensure you are speaking to the correct agencies and organizations to help you feel supported and get you back in operation securely,” she says.