REvil’s Ransomware Success Formula: Constant Innovation
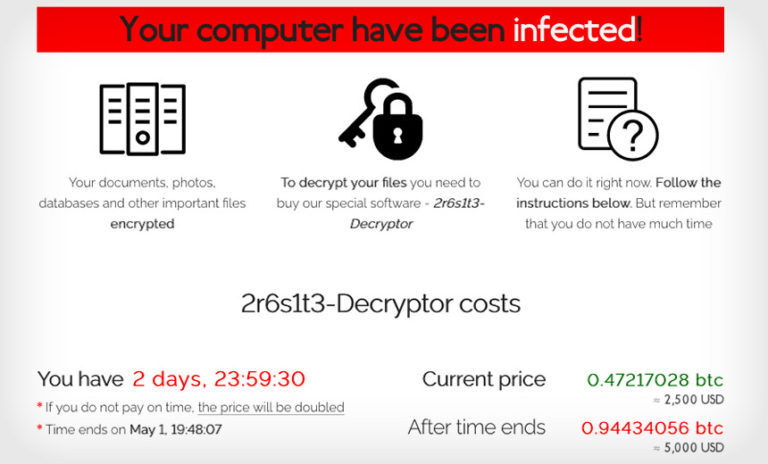
Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime Affiliate-Driven Approach and Regular Malware Refinements Are Key, Experts Say Mathew J. Schwartz (euroinfosec) • July 2, 2021 Sodinokibi/REvil ransom note (Source: Malwarebytes) Just as cloud services have taken the business world by storm, the same can be said for ransomware, including one of…