New Study Warns of Security Threats Linked to Recycled Phone Numbers
A new academic study has highlighted a number of privacy and security pitfalls associated with recycling mobile phone numbers that could be abused to stage a variety of exploits, including account takeovers, conduct phishing and spam attacks, and even prevent victims from signing up for online services.
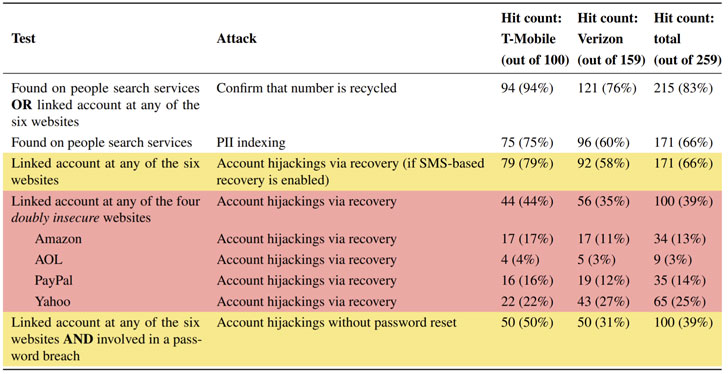
Nearly 66% of the recycled numbers that were sampled were found to be tied to previous owners’ online accounts at popular websites, potentially enabling account hijacks by simply recovering the accounts tied to those numbers.
“An attacker can cycle through the available numbers shown on online number change interfaces and check if any of them are associated with online accounts of previous owners,” the researchers said. If so, the attacker can then obtain these numbers and reset the password on the accounts, and receive and correctly enter the OTP sent via SMS upon login.”
The findings are part of an analysis of a sample of 259 phone numbers available to new subscribers of U.S. telecom majors T-Mobile and Verizon Wireless. The study was undertaken by Princeton University’s Kevin Lee and Prof. Arvind Narayanan, who is one of the executive committee members at the Center for Information Technology Policy.
Phone number recycling refers to the standard practice of reassigning disconnected phone numbers to other new subscribers of the carrier. According to the Federal Communications Commission (FCC), an estimated 35 million phone numbers are disconnected each year in the U.S.
But this can also pose serious dangers when an attacker does a reverse lookup by randomly entering such numbers in the online interfaces offered by the two carriers, and upon encountering a recycled number, buy them and successfully log in to the victim account to which the number is linked.
At the heart of the attack strategy is the lack of query limits for available numbers imposed by the carriers on their prepaid interfaces to change numbers, in addition to displaying “full numbers, which gives an attacker the ability to discover recycled numbers before confirming a number change.”
What’s more, 100 of the sampled phone numbers were identified as associated with email addresses that had been involved in a data breach in the past, thereby allowing account hijacks of a second kind that circumvent SMS-based multi-factor authentication. In a third attack, 171 of the 259 available numbers were listed on people search services like BeenVerified, and in the process, leaked sensitive personal information of prior owners.
“Once they obtain the previous owner’s number, they can perform impersonation attacks to commit fraud or amass even more PII on previous owners,” the researchers explained.
Beyond the aforementioned three reverse lookup attacks, five additional threats enabled by phone number recycling target both previous and future owners, permitting a malicious actor to impersonate past owners, hijack the victims’ online phone account and other linked online accounts, and worse, carry out denial-of-service attacks.
“Attacker obtains a number, signs up for an online service that requires a phone number, and releases the number,” the researchers said. “When a victim obtains the number and tries to sign up for the same service, they will be denied due to an existing account. The attacker can contact the victim through SMS and demand payment to free up the number on the platform.”
In response to the findings, T-Mobile said it has updated its “Change your phone number” support page with information about reminding users to “update your contact number on any accounts that may have your number saved, such as notifications for bank accounts, social media, etc.” and specify the FCC-mandated number aging period of 45 days to allow reassignment of old numbers.
Verizon, likewise, has made similar revisions to its “Manage Verizon mobile service” support page. But neither of the carriers appear to have made any concrete changes that make the attacks harder to pull off.
If anything, the study is another evidence of why SMS-based authentication is a risky method, as the attacks outlined above could allow an adversary to hijack an SMS 2FA-enabled account without having to know the password.
“If you need to give up your number, unlink it from online services first,” Narayanan said in a tweet. “Consider low-cost number ‘parking’ services. Use more secure alternatives to SMS-2FA such as authenticator apps.”