Buer Dropper Malware Updated Using Rust
Fraud Management & Cybercrime
,
Fraud Risk Management
,
Governance & Risk Management
Proofpoint: New Code Makes ‘RustyBuer’ Version Harder to Detect
Attackers are using a freshly updated variant of the Buer first-stage malware loader rewritten in the Rust programming language to help evade detection, the security firm Proofpoint reports.
See Also: Live Webinar | Empowering Financial Services with a Secure Data Path From Endpoint to Cloud
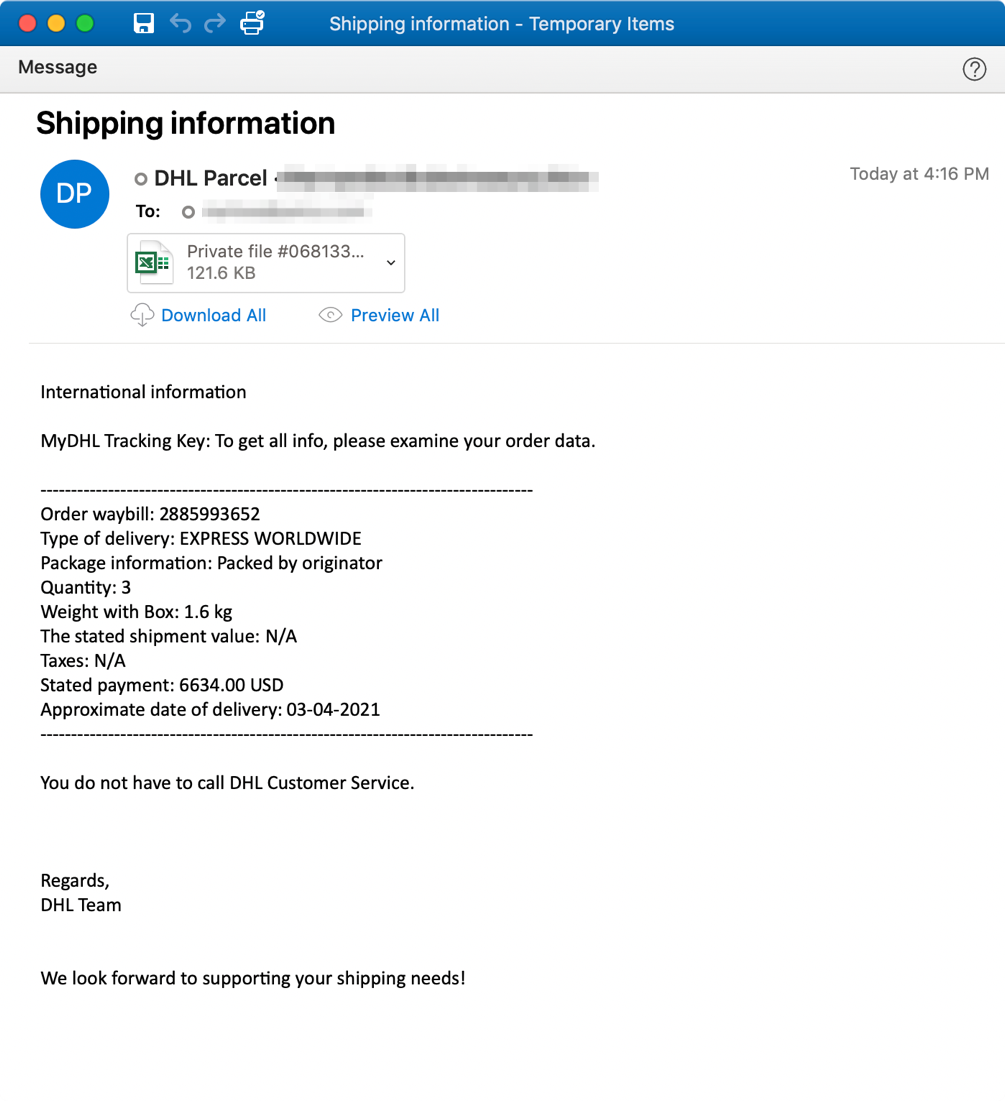
In April, researchers observed the loader, dubbed RustyBuer, being distributed via emails purporting to be DHL shipping support notices. Proofpoint says a gang likely developed the malware to sell to others on darknet marketplaces. RustyBuer is capable of exfiltrating information from a targeted system.
“The new strain is completely rewritten in a coding language called Rust, a departure from the previous C programming language. It is unusual to see common malware written in a completely different way,” the researchers say.
Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, says the language switch didn’t alter the malware’s functionality or capability.
“However, rewriting malware can enable a threat actor to evade existing detections,” she says. “For example, RustyBuer uses its own TLS library. While the malware executed as expected, we had to make a few adjustments so that we could see all of the command-and-control communications.”
Due to its efficiency and broad feature set, Rust is becoming a widely used programming language. By using this language, RustyBuer can better evade existing Buer detection capabilities, Proofpoint says.
Proofpoint recently detected emails with RustyBuer targeting over 200 organizations in 50 industries. The attackers are using the malware to establish a beachhead inside a system, and in some cases, these attackers then opt to sell this access to others who go on to implant additional malware, including Cobalt Strike and ransomware, Proofpoint says.
Sophos had tracked Buer being used to drop Ryuk in October 2020 (see: Ryuk Ransomware Updated With ‘Worm-Like Capabilities’). Researchers first observed Buer in 2019, Proofpoint notes.
RustyBuer Campaign
The Buer and RustyBuer campaigns use DHL-themed phishing emails containing a malicious Microsoft Word or Excel document. In the most recent campaign, attackers improved the social engineering behind the email lure by including more details aimed at enticing recipients to click on the malicious files, Proofpoint says. The malicious email is portrayed as a notification that a package is arriving and contains a tracking number and arrival date.
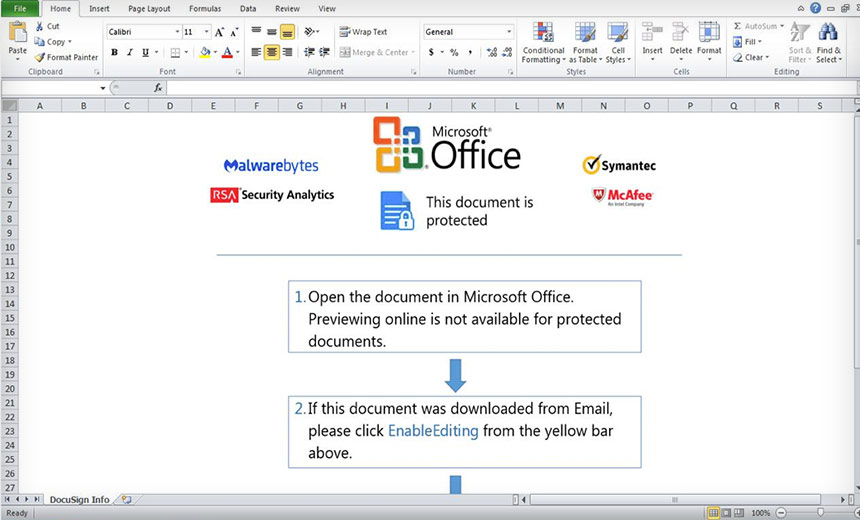
The malicious actors also added the logos of some cybersecurity companies, including McAfee and Symantec, to the attached document to make the victim believe that it was safe to open, according to the report.
When a victim takes the bait and enables the attached document’s macro, it then leverages an Application Bypass (Windows Shell DLL via LOLBAS) to evade detection from endpoint security mechanisms, Proofpoint says.
Payloads
Once installed, the malware establishes persistence by using a shortcut .LNK file, which runs at startup, the researchers say.
In some cases, the attacker opts to drop the legitimate pen tester software Cobalt Strike as a secondary payload. Cobalt Strike is able to deploy an agent named Beacon, which helps the user communicate with command-and-control servers and maintain persistence. Beacon has a variety of functionalities, including command execution, key logging, file transfer, SOCKS proxying, privilege escalation, Mimikatz, port scanning and lateral movement, according to Malpedia. Mimikatz is an open-source application that allows users to view and save authentication credentials.
Proofpoint notes that not all attacks include Cobalt Strike, which may mean that attackers who use it may be operating under a different business model.
“Researchers assess this may be due to threat actors in some specific instances operating as access-as-a-service providers. These threat actors may be attempting to establish initial access in victim environments to then sell their access to other threat actors in underground marketplaces,” Proofpoint says.
Once the malware establishes contact with the command-and-control server, it issues a POST request via HTTPS to start removing data from this system, Proofpoint says. Typically, the information taken includes user name, Windows version, architecture type, number of processors, user privileges, computer name and AD domain, the researchers say.





