Most Frequently Exploited CVEs Listed
Governance & Risk Management
,
Patch Management
Experts Say Advisory Highlights Vulnerability Management Challenges
A joint cybersecurity advisory issued by several agencies this week highlighting the ongoing exploits of longstanding software vulnerabilities illustrates the woeful state of patch management, security experts say.
See Also: Live Webinar | Improve Cloud Threat Detection and Response using the MITRE ATT&CK Framework
The advisory lists the top 30 vulnerabilities – primarily Common Vulnerabilities and Exposures, or CVEs – routinely exploited in 2020 and those being widely exploited so far this year. Prepared by the U.S. Cybersecurity and Infrastructure Agency and the FBI, along with the Australian Cyber Security Center and the U.K.’s National Cyber Security Center, the report says four of the most critical flaws – which should be patched immediately – involved remote work, VPNs or cloud-based technologies.
‘Woeful’ Patch Management
“Announcements like these … primarily highlight the woeful state of patch management,” says Ross Rustici, a former security expert for the Department of Defense. “While the data is useful for understanding some of the trend lines in exploitation, it generally reinforces common wisdom rather than providing additional insight and only provides a tiny sliver of the information needed to assess risk.”
Rustici, who is now the managing director at global advisory firm StoneTurn, adds: “If companies prioritized patching over potential business interruptions, we would not have eight of the 12 most exploited vulnerabilities in 2020 be a year or more old.”
Lisa Plaggemier, interim executive director of the National Cyber Security Alliance, points out: “Developing patches can sometimes feel like a wild goose chase. Therefore, focusing on known and active vulnerabilities makes a lot of sense in terms of building strong defenses. However, this does not mean that organizations should rest on their laurels once all of these patches have been executed, as zero-day vulnerabilities still present a significant threat to cybersecurity health.”
Applying Best Practices
Many devices went unpatched in 2020, the agencies say, as COVID-19-related remote work setups challenged organizations’ abilities to conduct rigorous patch management. And many of the same patterns have persisted in 2021.
“In cybersecurity, getting the basics right is often most important. Organizations that apply the best practices of cybersecurity, such as patching, can reduce their risk to cyber actors exploiting known vulnerabilities in their networks,” says Eric Goldstein, executive assistant director of CISA. “We partnered with ACSC, NCSC and FBI to highlight cyber vulnerabilities that public and private organizations should prioritize for patching to minimize risk of being exploited by malicious actors.”
“The advisory puts the power in every organization’s hand to fix the most common vulnerabilities,” says Paul Chichester, director of operations for the U.K.’s NCSC.
The agencies say malicious cyber actors will likely continue to exploit longstanding vulnerabilities if systems remain unpatched. Exploiting these flaws, officials say, complicates attribution, reduces costs and minimizes risks.
“Focusing scarce cyber defense resources on patching those vulnerabilities that cyber actors most often use offers the potential of bolstering network security while impeding our adversaries’ operations,” the advisory says.
Vulnerability Management Is Challenging
But, as Rick Holland, a former intelligence analyst for the U.S. Army, notes: “Vulnerability management is one of the most challenging aspects of any security program.”
Holland, who is now CISO at security firm Digital Shadows, adds: “Taking a risk-based approach is the way forward, and teams should absolutely be prioritizing vulnerabilities that are actively being exploited. You can’t patch ‘all the things,’ and defenders are drowning in vulnerabilities.”
Rita Gurevich, a board member on the New Jersey Technology Council, says organizations shifting to a remote workforce “are likely simply shifting identities and data to the cloud without much concentrated efforts on pruning access beforehand or reviewing if and how data is being used. This results in unnecessary costs of moving ‘junk from one attic to another’ – but now it’s not living in your own four walls.”
Gurevich, founder and CEO of security firm Sphere Technology Solutions, says this week’s joint advisory highlights how critical it is to focus on risk mitigation strategies.
2021 Activity
The advisory issued this week says organizations should prioritize patching for the following CVEs:
- Microsoft Exchange: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065 can all lead to remote code execution.
- Pulse Secure: CVE-2021-22893, RCE on Pulse Connect Secure gateway; CVE-2021-22894, arbitrary code execution; CVE-2021-22899, RCE; and CVE-2021-22900, unrestricted uploads.
- Accellion: CVE-2021-27101, SQL injection; CVE-2021-27102, OS command execution; CVE-2021-27103, server-side request forgery; and CVE-2021-27104, OS command execution.
- VMware: CVE-2021-21985, RCE.
- Fortinet: CVE-2018-13379, path traversal; CVE-2020-12812, improper authentication; and CVE-2019-5591, default configuration.
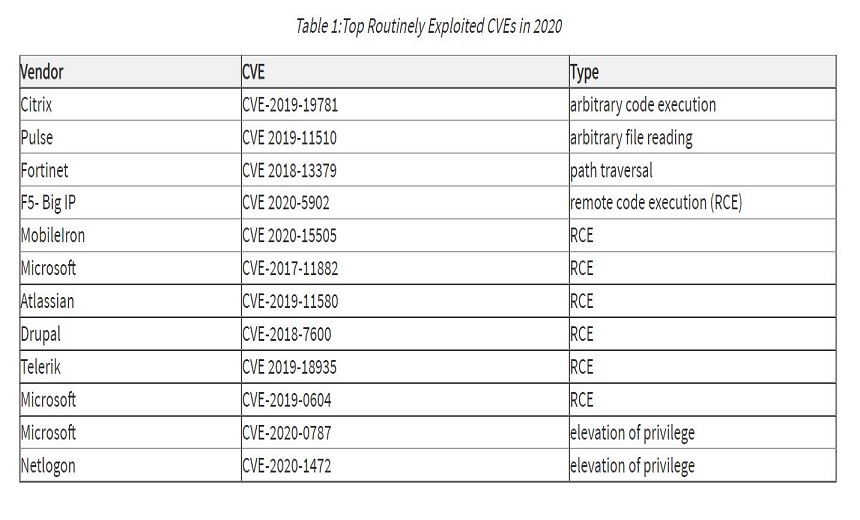
2020 CVEs
The most exploited vulnerabilities in 2020 were:
- CVE-2019-19781: A critical vulnerability in Citrix’s Application Delivery Controller widely used throughout the U.S;
- CVE-2019-11510: A flaw in Pulse Connect Secure VPN frequently targeted by nation-state APTs.
It’s ‘Pretty Significant’
Commenting on the significance of the advisory, Roger Grimes, defense expert at the security firm KnowBe4, says: “The leading cybersecurity organizations of multiple countries are telling us what the top exploits are, not a vendor-biased report – and that is pretty significant. There are a ton of network-level exploits here. It’s time for the network people to start making sure their patches are updated in a timely manner.”
For a full list of the most targeted CVEs, visit: us-cert.cisa.gov.






