Spyware Exposé Highlights Suspected Apple Zero-Day Flaws
Application Security
,
Cyberwarfare / Nation-State Attacks
,
Endpoint Security
‘Zero Click’ Exploits Suspected in NSO Group Pegasus Spyware Attacks, Amnesty Says

A new exposé tracking how spyware has been used to target journalists, human rights advocates and dissidents suggests attackers have been exploiting zero-day flaws in Apple applications and devices.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
The surveillance effort has been dubbed the Pegasus Project by Amnesty International, 17 media outlets as well as a Paris-based journalist collective called Forbidden Stories, who on Sunday collectively released their findings.
The Pegasus Project focuses on NSO Group, an Israeli company that develops spyware called Pegasus. NSO Group has long been accused of selling spyware to countries that use it to conduct surveillance on activists, journalists and dissidents.
In the latest campaign to be tied to the use of Pegasus software, Forbidden Stories says the long list of targets included “award-winning Azerbaijani journalist Khadija Ismayilova; reporter Szabolcs Panyi from Direkt36, an Hungarian investigative media outlet; freelance Moroccan journalist Hicham Mansouri; the director of the French investigative site Mediapart Edwy Plenel; and the founders of the Indian independent media The Wire, one of the few news organizations in the country that does not rely on money from private business entities.”
The Guardian reports that victims include a Mexican journalist and her family members as well as other prominent individuals and business executives that it plans to name in the coming days. It says the Apple flaws were identified after journalists and researchers obtained a leaked list of 50,000 phone numbers tied to individuals of interest to NSO Group’s customers and traced it back to the use of Pegasus.
Responding to the new report, NSO Group says it denies all of the accusations, The New York Times reports.
Publication of the Pegasus Project’s report follows Facebook In October 2019 taking the extraordinary step of suing NSO Group for allegedly developing and using an exploit for its WhatsApp messenger (see Facebook Sues Spyware Maker Over WhatsApp Exploit).
Based on a digital forensic investigation into Apple-using targets, Amnesty says it believes that Pegasus users have the ability to target the latest version of Apple’s mobile operating system – iOS 14.6 – using “zero click” exploits, which refers to attacks that can successfully infect a device with malware without requiring any interaction between a victim and their device.
Apple has confirmed that the attacks, discovered by technical experts working with Amnesty, are very sophisticated and a serious threat. But it also notes that the highly targeted attacks likely pose no risk to the overwhelming majority of its users.
Amnesty: At Least 37 Devices Hit
Amnesty says Pegasus spyware – or signs that it had previously been installed – has been found on at least 37 devices. Applications under attack may include iMessage – Apple’s messaging app – as well as Apple Music, it says. Some of the described attacks also affect the latest models and versions of Apple’s hardware and software.
“Most recently, a successful ‘zero click’ attack has been observed exploiting multiple zero-days to attack a fully patched iPhone 12 running iOS 14.6 in July,” Amnesty says in its report.
Amnesty’s results have been independently confirmed by Citizen Lab, a research lab at the University of Toronto’s Munk School of Global Affairs that regularly investigates state-sponsored surveillance campaigns against journalists, human rights advocates and other vulnerable groups.
“We at @citizenlab also saw a 14.6 device hacked with a zero-click iMessage exploit to install Pegasus,” tweets Bill Marczak, a senior research fellow with Citizen Lab. “All this indicates that NSO Group can break into the latest iPhones.”
This isn’t the first time that NSO Group has allegedly used zero-click attacks to exploit vulnerabilities in Apple products. In December 2020, Citizen Lab detailed a separate campaign, attributed to NSO Group’s software, which used zero-click attacks against iMessage.
Informed by Amnesty of the latest findings, Apple says in a statement that it “unequivocally condemns cyberattacks against journalists, human rights activists and others seeking to make the world a better place.” But it says the vulnerabilities identified by Amnesty, while serious, are unlikely to impact most users.
“Attacks like the ones described are highly sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals,” Apple says. “While that means they are not a threat to the overwhelming majority of our users, we continue to work tirelessly to defend all our customers, and we are constantly adding new protections for their devices and data.”
Unusual iMessages
Amnesty cited numerous examples of attacks it studied and how it believed such attacks were being executed.
In one instance, Amnesty says an investigative journalist in Azerbaijan was targeted. The journalist is not identified by name but instead a code – AZJRN1 – and was “repeatedly targeted using zero-click attacks from 2019 until mid-2021.”
Amnesty says the journalist was hit with a fresh and successful infection of Pegasus on July 10. The exploit appears to start with iMessage before also invoking Apple’s Music app, although it unclear what the Music app’s role is in the exploit. But that app made an HTTP request to a domain that Amnesty has identified as being part of the infrastructure used to support Pegasus.
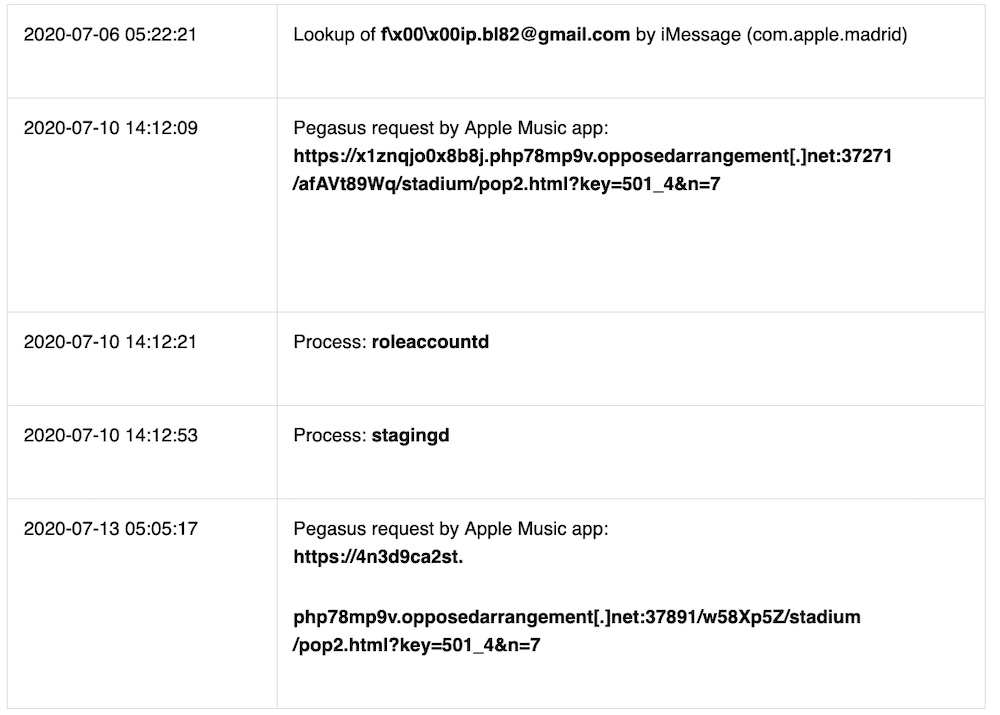
“Recent research has shown that built-in apps such as the iTunes Store app can be abused to run a browser exploit while escaping the restrictive Safari application sandbox,” Amnesty writes.
Other attacks indicated a likely vulnerability in iMessage. Some victims’ devices, notably, had received iMessage push notifications which appeared to represent the beginning of an attack.
In one example, the device of a Rwandan activist began looking up an unfamiliar iCloud account on May 17. Then in the ensuing minutes, “20 iMessage attachment chunks are created on disk,” according to Amnesty’s technical assessment. That attack didn’t appear to be successful, but two others that occurred on June 18 and June 23 did succeed, resulting in Pegasus payloads being installed on the device.
“These most recent discoveries indicate NSO Group’s customers are currently able to remotely compromise all recent iPhone models and versions of iOS,” Amnesty writes.
Messaging platforms are tempting targets for hackers since they can accept all kinds of untrusted input and have to parse it in a safe way.
Apple has repeatedly sought to strengthen iMessage’s defenses, not least following numerous run-ins with zero-click attacks. For example, researchers at Google’s Project Zero last year discovered one such attack in which an attacker only needed to know an Apple user’s email address or phone number to completely take over a device via iMessage.
Earlier this year, Apple introduced in iOS 14 a security defense dubbed BlastDoor, which is responsible for parsing untrusted data and also has new sandboxing protections, as Google’s Project Zero also detailed. But as Amnesty’s research shows, attackers may have found ways to circumvent even Apple’s latest defenses.