Microsoft Exchange Cyber Attack — What Do We Know So Far?
Microsoft on Friday warned of active attacks exploiting unpatched Exchange Servers carried out by multiple threat actors, as the hacking campaign is believed to have infected tens of thousands of businesses, government entities in the U.S., Asia, and Europe.
The company said “it continues to see increased use of these vulnerabilities in attacks targeting unpatched systems by multiple malicious actors beyond HAFNIUM,” signaling an escalation that the breaches are no longer “limited and targeted” as was previously deemed.
According to independent cybersecurity journalist Brian Krebs, at least 30,000 entities across the U.S. — mainly small businesses, towns, cities, and local governments — have been compromised by an “unusually aggressive” Chinese group that has set its sights on stealing emails from victim organizations by exploiting previously undisclosed flaws in Exchange Server.
Victims are also being reported from outside the U.S., with email systems belonging to businesses in Norway and the Czech Republic impacted in a series of hacking incidents abusing the vulnerabilities. The Norwegian National Security Authority said it has implemented a vulnerability scan of IP addresses in the country to identify vulnerable Exchange servers and “continuously notify these companies.”
The colossal scale of the ongoing offensive against Microsoft’s email servers also eclipses the SolarWinds hacking spree that came to light last December, which is said to have targeted as many as 18,000 customers of the IT management tools provider. But as it was with the SolarWinds hack, the attackers are likely to have only gone after high-value targets based on an initial reconnaissance of the victim machines.
Unpatched Exchange Servers at Risk of Exploitation
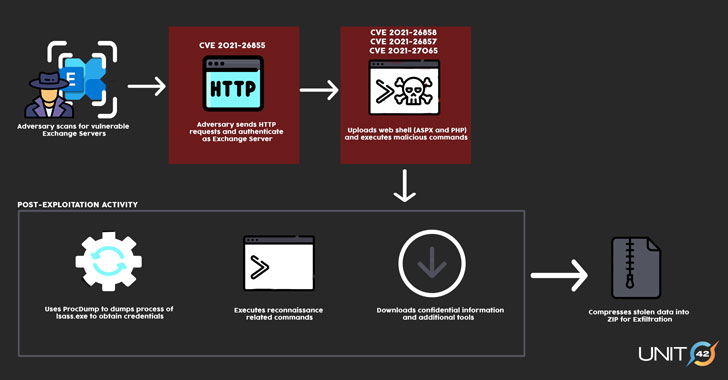
A successful exploitation of the flaws allows the adversaries to break into Microsoft Exchange Servers in target environments and subsequently allow the installation of unauthorized web-based backdoors to facilitate long-term access. With multiple threat actors leveraging these zero-day vulnerabilities, the post-exploitation activities are expected to differ from one group to the other based on their motives.
The four security issues in question were patched by Microsoft as part of an emergency out-of-band security update last Tuesday, while warning that “many nation-state actors and criminal groups will move quickly to take advantage of any unpatched systems.”
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), which released an emergency directive warning of “active exploitation” of the vulnerabilities, urged government agencies running vulnerable versions of Exchange Server to either update the software or disconnect the products from their networks.
“CISA is aware of widespread domestic and international exploitation of Microsoft Exchange Server vulnerabilities and urges scanning Exchange Server logs with Microsoft’s IoC detection tool to help determine compromise,” the agency tweeted on March 6.
It’s worth noting that merely installing the patches issued by Microsoft would have no effect on servers that have already been backdoored. Organizations that have been breached to deploy the web shell and other post-exploitation tools continue to remain at risk of future compromise until the artifacts are completely rooted out from their networks.
Multiple Clusters Spotted
FireEye’s Mandiant threat intelligence team said it “observed multiple instances of abuse of Microsoft Exchange Server within at least one client environment” since the start of the year. Cybersecurity firm Volexity, one of the firms credited with discovering the flaws, said the intrusion campaigns appeared to have started around January 6, 2021.
Not much is known about the identities of the attackers, except that Microsoft has primarily attributed the exploits with high confidence to a group it calls Hafnium, a skilled government-backed group operating out of China. Mandiant is tracking the intrusion activity in three clusters, UNC2639, UNC2640, and UNC2643, adding it expects the number to increase as more attacks are detected.
In a statement to Reuters, a Chinese government spokesman denied the country was behind the intrusions.
“There are at least five different clusters of activity that appear to be exploiting the vulnerabilities,” said Katie Nickels, director of threat intelligence at Red Canary, while noting the differences in the techniques and infrastructure from that of the Hafnium actor.
In one particular instance, the cybersecurity firm observed that some of the customers compromised Exchange servers had been deployed with a crypto-mining software called DLTminer, a malware documented by Carbon Black in 2019.
“One possibility is that Hafnium adversaries shared or sold exploit code, resulting in other groups being able to exploit these vulnerabilities,” Nickels said. “Another is that adversaries could have reverse engineered the patches released by Microsoft to independently figure out how to exploit the vulnerabilities.”
Microsoft Issues Mitigation Guidance
Aside from rolling out fixes, Microsoft has published new alternative mitigation guidance to help Exchange customers who need more time to patch their deployments, in addition to pushing out a new update for the Microsoft Safety Scanner (MSERT) tool to detect web shells and releasing a script for checking HAFNIUM indicators of compromise. They can be found here.
“These vulnerabilities are significant and need to be taken seriously,” Mat Gangwer, senior director of managed threat response at Sophos said. “They allow attackers to remotely execute commands on these servers without the need for credentials, and any threat actor could potentially abuse them.”
“The broad installation of Exchange and its exposure to the internet mean that many organizations running an on-premises Exchange server could be at risk,” Gangwer added.