Leaker Dismisses MobiKwik’s Not-So-Nimble Breach Denial
Breach Notification
,
Incident & Breach Response
,
Security Operations
Seller of 99 Million Customers’ Stolen Data Calls Firm ‘Incompetent,’ but Stops Sale
Customers of Indian payments platform MobiKwik appear to have gotten a lucky break: A listing for 8.2TB of stolen data pertaining to 99 million customers was withdrawn by a cybercrime forum seller.
See Also: Live Webinar | Attacks on Cloud Infrastructure
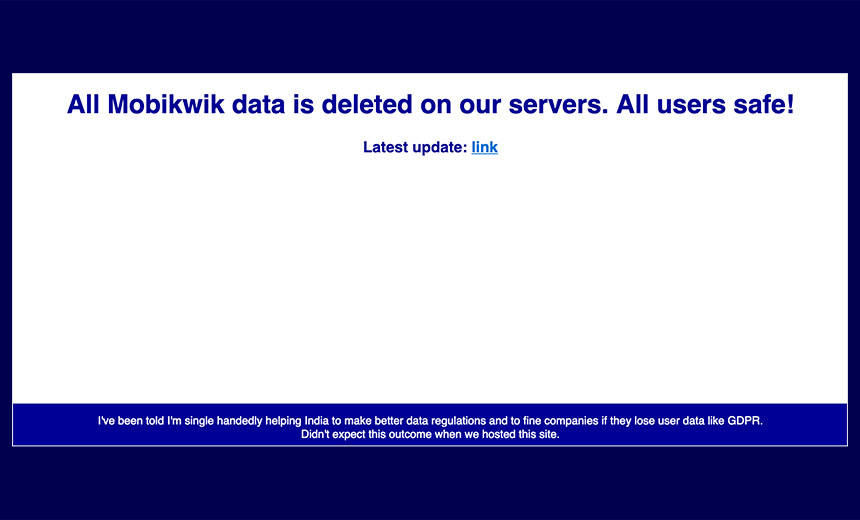
While branding MobiKwik “incompetent” for its handling of the alleged breach – the company continues to deny that anyone has ever stolen any of its data – the seller claims to have deleted the stolen data because of the risk to the public it poses.
“We just don’t want to see a company dig themselves deeper.”
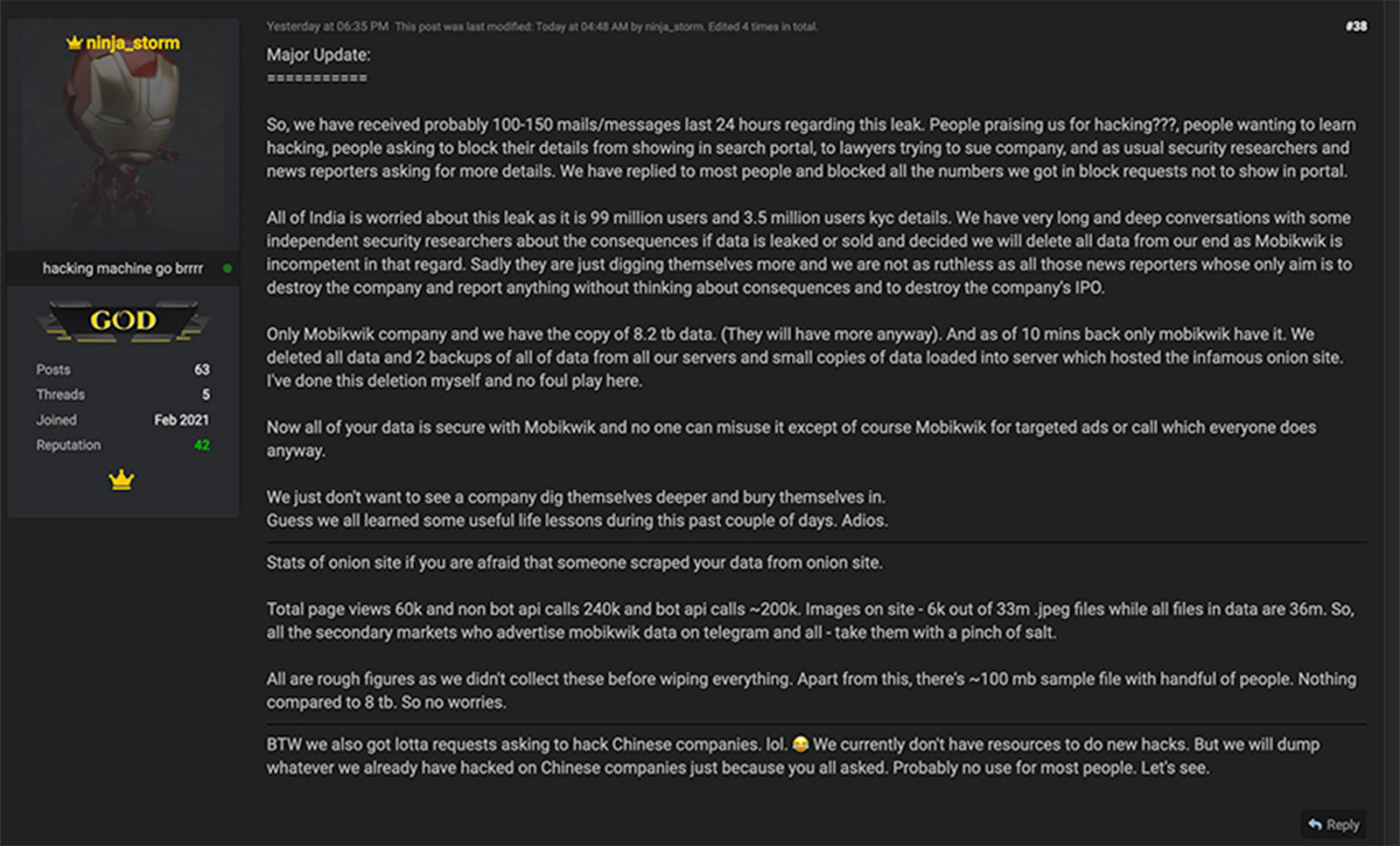
“All of India is worried about this leak as it is 99 million users and 3.5 million users’ KYC details,” the seller, who goes by “ninja_storm,” said in a Tuesday post to the RaidForums cybercrime forum, referring to the mandatory “know your customer” checks that financial services firms must use to confirm customers’ identity and watch for signs of fraud.
In the wrong hands, KYC information could arguably be used to commit fraud, especially when paired with customer details.
Founded in 2009, MobiKwik facilitates payments via mobile phones. It has attracted numerous investors, including Sequoia Capital and Bajaj Finance, and counts 120 million users.
MobiKwik continues to deny its systems were breached, although it says it has launched its second investigation into the matter. “For our users, we reiterate that all your MobiKwik accounts and balances are completely safe,” according to a message from the company posted on Tuesday. “All financially sensitive data is stored in encrypted form in our databases. No misuse of your wallet balance, credit card or debit card is possible without the one-time-password that only comes to your mobile number.”
On Tuesday, a post from ninja_storm claimed that the stolen information included:
- Databases: 350GB of MySQL dumps, comprising 500 databases;
- Personal details: 99 million customers’ details, including email, phone number, password, physical address, plus “lots more data,” including apps installed on devices, smartphone manufacturer, IP address and GPS location;
- 40 million payment cards: The 10-digit SHA256 hash of the card number and expiration date;
- Databases: “Lots of databases with all company data”;
- KYC: 7.5 TB of KYC data – details of passports, Aadhaar cards and PAN cards that were “used to get loans on the site.”
The listing set a price of 1.5 bitcoins – worth $88,000 – for the data to be deleted. “Exclusive. All data deleted on our end after transfer,” it claimed. The listing included a zip file with samples of stolen data.
Claim: Stolen Data Deleted
Now, however, the stolen information is no longer for sale, and all copies of the information – aside from what MobiKwik itself holds – have supposedly been deleted.
“We have very long and deep conversations with some independent security researchers about the consequences if data is leaked or sold and decided we will delete all data from our end as MobiKwik is incompetent in that regard,” ninja_storm says. “Sadly, they are just digging themselves more and we are not as ruthless as all those news reporters whose only aim is to destroy the company and report anything without thinking about consequences and to destroy the company’s IPO.”
Are the attacker’s claims – to have obtained stolen MobiKwik data and then to have deleted it – to be believed?
“We just don’t want to see a company dig themselves deeper and bury themselves in,” the seller says by way of explanation for why the allegedly breached data has been deleted. “Guess we all learned some useful life lessons during this past couple of days. Adios.”
MobiKwik: Maybe Other Breaches Are to Blame
MobiKwik hasn’t done itself any favors in its handling of this episode, noting that when the allegedly stolen data came to light in February, it “undertook a thorough investigation with the help of external security experts and did not find any evidence of a breach.”
Subsequently, after they reviewed the leaker’s sample of stolen data, “some users have reported that their data is visible on the dark web,” it adds, but then it says other breaches must be to blame.
“While we are investigating this, it is entirely possible that any user could have uploaded her/ his information on multiple platforms. Hence, it is incorrect to suggest that the data available on the dark web has been accessed from MobiKwik or any identified source,” MobiKwik claims.
But the company says that despite having already brought in “external security experts” to investigate, it’s now bringing in more, “to conduct a forensic data security audit.” Hence, it’s unclear what the first group of investigators might have done.
Not everyone appears to be convinced. Reuters on Thursday, citing an anonymous source with knowledge of the discussions, reported that the Reserve Bank of India was “not happy” with MobiKwik’s statements, and ordered it to immediately launch a full digital forensic investigation. Indian law grants RBI the power to fine payment system operators who violate its policies up to $7,000, “or double the amount of contravention, whichever is higher, where such amount is quantifiable.”
Misconfigured Cloud Buckets?
Despite MobiKwik’s claims, mounting evidence suggests it did, indeed, suffer a massive data breach, which led to the offering of authentic data for sale.
Multiple security researchers report that they had spotted publicly exposed MobiKwik data. One researcher, Rajshekhar Rajaharia, tells TechCrunch that he warned MobiKwik in February that its systems were publicly exposing sensitive data. Now, MobiKwik’s legal team plans to take “strict action against the so-called security researcher,” it tells TechCrunch.
But the publication reports that it obtained a screenshot showing a MobiKwik official asking customer support staff for Amazon Simple Cloud Storage, aka S3, to share logs, noting that MobiKwik “came to know that our S3 data is downloaded by some other person outside the organization.”
In other words, the alleged breach may trace to an all-too-common problem: Organizations misconfiguring their cloud storage and leaving cloud buckets and databases publicly accessible (see: Cloud Security: ‘Big Data’ Leak Prevention Essentials).
In the bigger picture, this incident is unusual in that it has pitted the trust and reliability of a criminal data leak broker against that of a business entrusted with securely handling both people’s personal details and money.
One appears to have been offering clear facts and transparency, albeit in the pursuit of criminal gains. The other tells its customers: “We are committed to a safe and secure Digital India.”






