Innovative REvil Ransomware Operation Is Back
Critical Infrastructure Security
,
Cybercrime
,
Cyberwarfare / Nation-State Attacks
Group Specializing in Big Game Hunting Has Amassed Millions in Ransom Payments
Has the notorious REvil ransomware group resumed full-scale attack operations?
See Also: Isolated Castles: Incident Response in the New Work From Home Economy
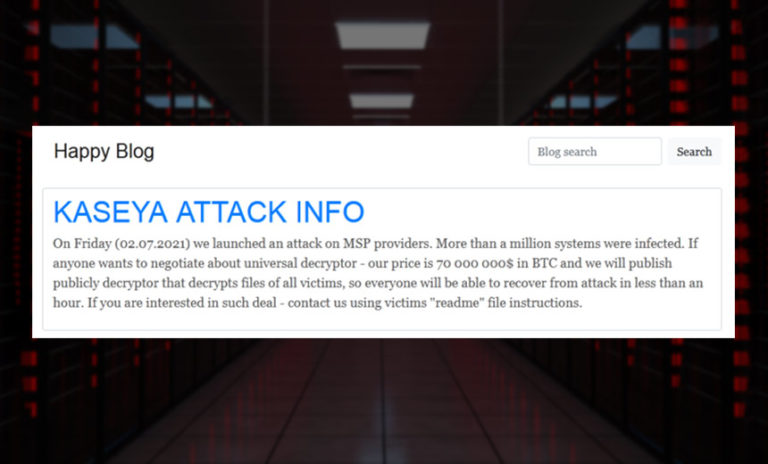
On Tuesday, multiple security experts – including Brett Callow, a threat analyst at Emsisoft – reported that the group’s Tor-based sites had come back online, including its “Happy Blog” data leak site and its payments portal.
Unfortunately, the Happy Blog is back online #REvil pic.twitter.com/vMr9qTOht2— Brett Callow (@BrettCallow) September 7, 2021
That’s notable because the ransomware-as-a-service operation, also known as Sodinokibi, went dark in July, not long after two big hits. On May 30, it forcibly encrypted systems at the U.S. operations of Brazil-based meat processing giant JBS, which paid the attackers a ransom worth $11 million in exchange for a decryption key and a promise to not leak stolen data. Over the July Fourth holiday weekend, it unleashed an attack via IT remote management software built by Kaseya, used by managed service providers, leading to about 1,500 organizations seeing their systems get crypto-locked by its ransomware.
In response, the White House pledged to mobilize more law enforcement resources to track and disrupt ransomware operations. President Biden also called on Russian President Vladimir Putin to crack down on domestic cybercriminals – or else.
Coincidentally or not, multiple groups at that time began going dark: DarkSide, which had attacked U.S.-based Colonial Pipeline, leading Americans to panic-buy gasoline; Babuk, which hit the Metropolitan Police Department of Washington, D.C., and leaked stolen data; and Avaddon, which seemed to exit because it was feeling the heat.
Another disappearing act was REvil’s Tor-based data leak site and payment portal, which became unreachable on July 13, capping off more than two years’ worth of attacks since the group apparently spun off in April 2019 from the GandCrab operation, which itself disappeared shortly thereafter, boasting that its affiliates had earned more than $2 billion.
Who’s Under Pressure Now?
Unfortunately, with its infrastructure coming back online, REvil appears to be back. Notably, all victims listed on its data leak site have had their countdown timers reset, Bleeping Computer reports. Such timers give victims a specified period of time to begin negotiating a ransom payment, before REvil says it reserves the right to dump their stolen data online.
REvil is one of a number of ransomware operations that regularly tells victims that it’s stolen sensitive data, before it forcibly encrypts systems and threatens to leak the data if they don’t pay. But REvil’s representatives have been caught lying before, by claiming to have stolen data as they extort victims into paying, only to admit later that they never stole anything.
Big Profits
Why might the infrastructure have come back online, including the payments portal, which accepts bitcoin and monero? Numerous experts have suggested REvil was just laying low in the wake of the Biden administration pledging to get tough. Perhaps the main operators and developers opted to relocate to a country from which it might be safer to run their business. Or maybe they were just taking a vacation.
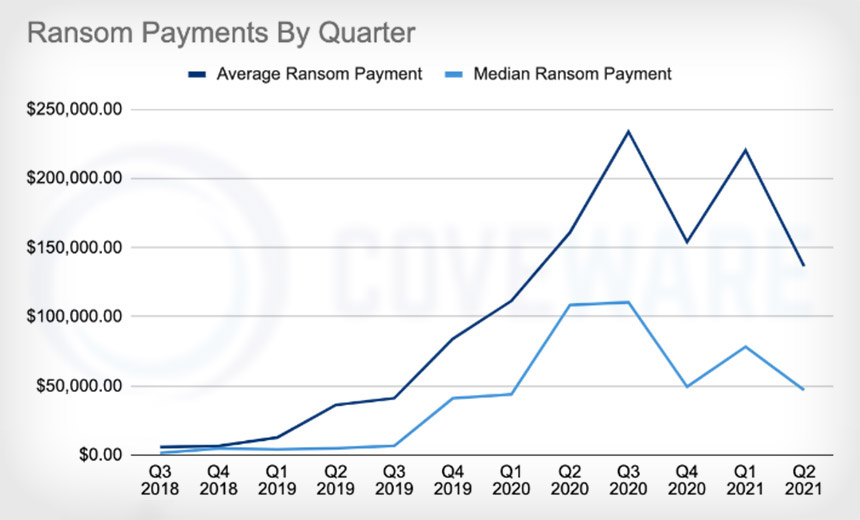
The reason for REvil’s return likely isn’t tough to guess. Namely, the illicit revenue being earned by top-tier ransomware gangs continues to be massive. The profit-sharing arrangement for REvil is reportedly 30% going to the operator and 70% going to the affiliate for every attack that results in a ransom payment. So the $11 million payoff from JBS likely made REvil’s administrators more than $3 million richer.
REvil’s data leak site, as of Monday, lists only one new victim: an Ohio-based firm that manufactures products made from aluminum, steel and stainless steel. The firm’s website currently resolves to a page that says the website remains “temporarily unavailable,” and lists a phone number for contacting the company, which reports that it otherwise remains “fully functional and operational.” But the business appears to have been hit on or before July 21, which is when it first said via Twitter that its website was temporarily unavailable.
On Sept. 4, however, a never-before-seen REvil executable was uploaded to virus-scanning service VirusTotal, suggesting that the group might have resumed hitting targets.
In addition, Emsisoft’s Callow tells me there are signs of fresh attacks. “REvil has opened a negotiation with a South African company within the last couple of days,” he says. “The negotiation could relate to an older attack, but it’s more likely that it’s recent.”
Many Ransomware Operations at Work
Of course, REvil is just one of many players. Indeed, Israeli threat intelligence firm Kela says that numerous ransomware operators continue to list new victims on their data leak sites. In just the past week, Kela says, it’s seen new victims listed by these 11 groups: BlackMatter, Clop, Conti, Cuba, Grief, Groove, LockBit, Marketo, Ragnar Locker, REvil and Vice Society.
All of those groups are ransomware-as-a-service operations, meaning operators maintain a portal where affiliates can download their crypto-locking malware and use it to infect victims. Whenever a victim pays a ransom, the operator and affiliate share in the profits. Experts say the vast majority of these Russian-language operations’ attacks are typically conducted by affiliates.
Clearly, organizations need effective procedures and defenses in place – including well-tested backups, stored offline – to defend against any type of ransomware attack.
REvil, however, remains notable because of its historical dominance as well as its ability to constantly innovate. Ransomware incident response firm Coveware says that of the thousands of cases it investigated from April through June, REvil was the most prevalent strain of crypto-locking malware tied to attacks it investigated, followed by Conti v2, Avaddon Mespinoza and Hello Kitty.
REvil, Conti and LockBit are among the more top-tier ransomware operations that have been practicing big game hunting, meaning they’ve focused their operations on taking down larger targets in pursuit of bigger ransomware payoffs.
So if one of the big players is back, it’s bad news.