Hunting phishing websites with favicon hashes, (Mon, Apr 19th)
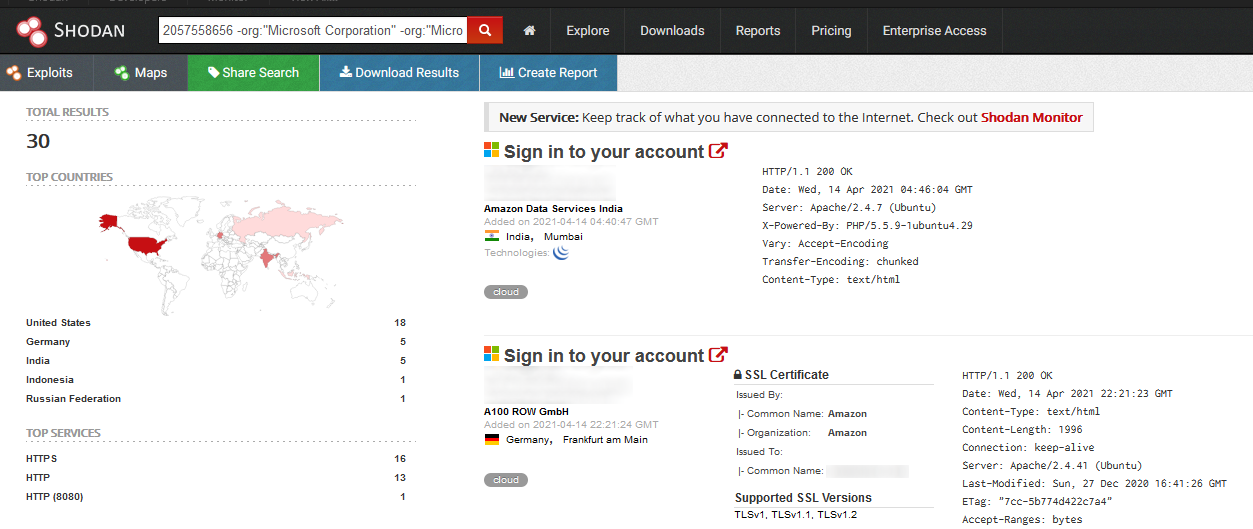
HTTP favicons are often used by bug bounty hunters and red teamers to discover vulnerable services in a target AS or IP range. It makes sense since different tools (and sometimes even different versions of the same tool) use different favicons[ 1 ] and services such as Shodan calculate MurmurHash….