Heimdal Security Blog | Accellion Data Breach Show Ties to Clop Ransomware and FIN11
On Monday, cybersecurity researchers connected a series of attacks targeting Accellion File Transfer Appliance (FTA) servers over the past two months to a data breach and extortion campaign orchestrated by the UNC2546 cybercrime group. Threat actors targeted up to 100 companies using Accellion’s FTA and stole sensitive files by combining multiple zero-day vulnerabilities and a new web shell.
The attacks first began in mid-December 2020, when UNC2546 started exploiting a SQL injection vulnerability in Accellion’s FTA. Now, the hackers opted for an extortion campaign exploiting zero-day vulnerabilities in the legacy FTA software to install DEWMODE web shell on victim networks and withdrawing sensitive data. Subsequently, the victims were blackmailed over email with making stolen information publicly available on a leak site operated by the CLOP ransomware gang unless a ransom was paid.
The emails were customized to each victim and sent from a no-cost account to a compact quantity of addresses.
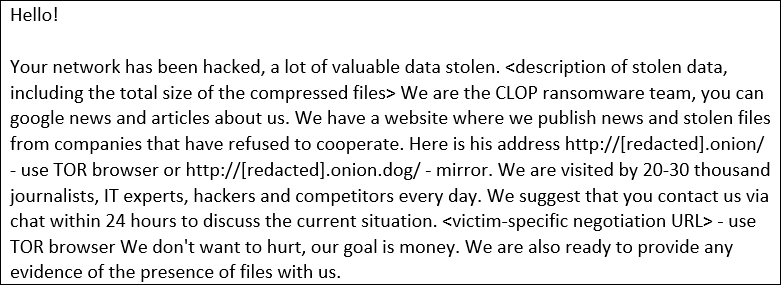
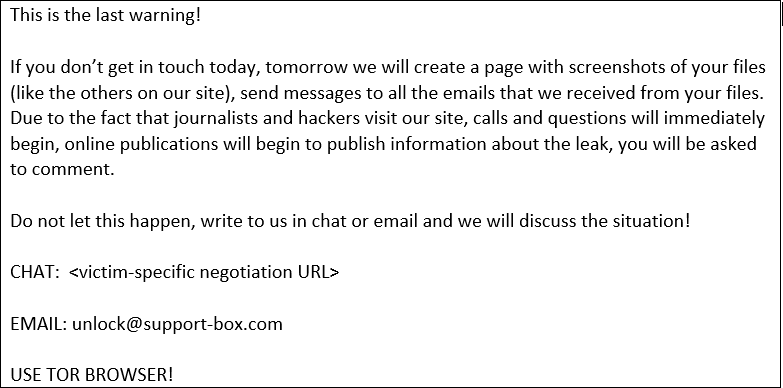
If the victim ignored the initial threats, other emails followed with the clear intention to force payment.
Following the slew of attacks, Accellion issued an official statement announcing that they have patched four FTA vulnerabilities that were known to be exploited by the threat actors, and incorporated new monitoring and alerting capabilities to flag any suspicious behavior. According to the investigation, the flaws were as follows:
Additionally, FireEye’s Mandiant forensics unit, which has been retained by Accellion, says it has done penetration tests and code reviews of the FTA, and no other critical vulnerabilities have been found.
UNC2546’s infrastructure overlaps with FIN11, a fiscally inspired group that has been active for a long time, conducting common phishing strategies. Despite the fact that FIN11 operators are now publishing data from Accellion FTA clients on the Clop ransomware leak site, these companies haven’t had any part of their internal network encrypted but are rather victims of a classic extortion scheme.
Among the companies that had their data listed on the Clop site so far are Fugro, Danaher, Singapore’s largest telco, Singtel, and Law firm Jones Day.
Other companies that have reported security breaches due to attacks on their FTA servers without having their data leaked on the CLOP site include The Reserve Bank of New Zealand, The Australian Securities and Investments Commission (ASIC), Law firm Allens, The University of Colorado, The Washington State Auditor Office, QIMR Berghofer Medical Research Institute, US retail store chain Kroger.
In light of this unfortunate event, Accellion announced plans to retire FTA effective April 30, according to a company notice. Although these measures should have been done sooner, it’s understandable, given that Accellion likely didn’t want to overly aggravate its customers, particularly given the plethora of secure file-sharing alternatives. However, if an organization continues to use FTA, it should at the very least mitigate risk with a layered approach by patching and implementing additional log and access review.
Email communications are the first entry point into an
organization’s systems.
Heimdal™ Email Fraud Prevention
Is the next-level mail protection system which secures
all your incoming and outgoing comunications.
- Deep content scanning for attachments and links;
- Phishing, spear phishing and man-in-the-email attacks;
- Advanced spam filters to protect against sophisticated attacks;
- Fraud prevention system against Business Email Compromise;
Be aware that cyber attackers are one step ahead of the defenders. That means that you cannot always be 100% protected against them, not even with all the email filtering systems or anti-virus software. Obviously, this doesn’t mean that you want to make their jobs easier, so taking some simple steps like keeping your software updated or installing a reliable antivirus will go a long way in preventing phishing.






