
Similar Posts

Colonial Cybercriminal Group’s DarkNet Website No Longer Accessible
The dark web page belonging to the DarkSide hacking group is down, as Bloomberg states. The Russian ransomware group is accused of attacking Colonial Pipeline. DarkSide was identified by the FBI and cybersecurity experts as the group responsible for the Colonial attack, that forced the company to shut down operations, causing fuel shortages in…

Facebook Disrupts Iranian APT Campaign
Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Media ‘Tortoiseshell’ Group Used the Social Network to Contact Targets Doug Olenick (DougOlenick) • July 15, 2021 Facebook’s threat intelligence team says it has disrupted an Iranian advanced persistent threat group that was using the social network as part of an effort…
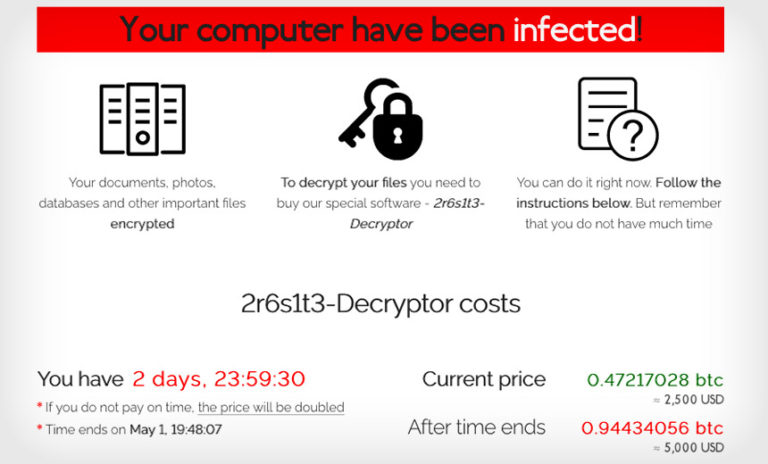
Ransomware Gangs ‘Tell All’ in Interviews
Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service REvil, MountLocker and LockBit Operators Describe Strategies and Target Selection Mathew J. Schwartz (euroinfosec) • March 22, 2021 Ransom note for a REvil – aka Sodinokibi – ransomware infection (Source: Cisco Talos) Ransomware-wielding attackers have been in the limelight lately – not just for…
Zynga’s Case Set for Arbitration
Governance & Risk Management , Incident & Breach Response , Legislation & Litigation Judge Says Users Agreed With Arbitration When Accepting Terms and Conditions Mathew J. Schwartz (euroinfosec) • August 3, 2021 Zynga develops mobile games such as Words With Friends 2 (Photo: Zynga) Yet another lawsuit filed in the wake of a…

Pearson Slammed for Breach – Wasn’t Just ‘Data Exposure’
Breach Notification , Governance & Risk Management , Incident & Breach Response Firm Pays $1 Million Settlement After Regulator Says It Misled Investors and Victims Mathew J. Schwartz (euroinfosec) • August 17, 2021 When is a data exposure not just a data exposure? See Also: Live Webinar | Password Management: Securing Hybrid Work…

India using our tech against Pakistan not acceptable: US firm
A recent Forbes article has alleged the Indian government for abusing private technology against China and Pakistan. Earlier this year, researchers at Russian cybersecurity firm Kaspersky witnessed a cyberespionage campaign targeting Microsoft Windows PCs at government and telecom entities in China and Pakistan, the Forbes article read. The software used by the digital spies was…

