Chinese APT Groups Targeted Asian Telecoms
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Cybereason: Attacks Exploited Microsoft Exchange Servers

Chinese advanced persistent threat groups compromised networks of telecommunication providers across Southeast Asia in an effort to harvest customers’ sensitive communications, according to a new report from the security firm Cybereason. As in other Chinese cyberattacks, these APT campaigns exploited flaws in Microsoft Exchange servers.
See Also: Live Panel | How Organizations Should Think About Zero Trust
The researchers uncovered several previously unidentified cyberattack campaigns infiltrating major providers and evading detection since at least 2017, Cybereason says.
Researchers identified three clusters of attacks associated with the campaign that it attributed to the Chinese APTs Soft Cell, Naikon and Threat Group-3390. The firm says overlaps in the attackers’ tactics, techniques and procedures suggest a connection between the groups.
Government Connection?
“It is not surprising that the telcos targeted in these intrusions are located in ASEAN [Association of Southeast Asian Nations] countries, some of which have long-term, publicly known disputes with the People’s Republic of China,” Cybereason says in its report
The security firm says at one time, each cluster was observed in the same environment, operating on the same endpoints at around the same time.
“One thing is certain: All three threat actors are operating on behalf of Chinese state interests,” says Assaf Dahan, senior director, head of threat research at Cybereason.
Espionage Efforts
Telecoms were compromised to facilitate espionage against specific targets – likely corporations, political figures, government officials, law enforcement agencies, political activists and dissidents of interest to the Chinese government, Cybereason says.
“The attackers exfiltrated hundreds of gigabytes of data collected from the network,” Dahan says. “Knowing the threat actors targeted major servers … gives us an indication that PII was also likely compromised.”
The findings follow U.S. President Joe Biden’s recent rebuke of Chinese cyber activity, blaming the nation for another series of attacks, detected in January, that exploited vulnerabilities in unpatched Microsoft Exchange servers. The U.S. said last month the criminal group responsible for the attacks – which Microsoft called Hafnium – worked for China’s Ministry of State Security, which oversees foreign intelligence operations (see: US: Chinese Government Waged Microsoft Exchange Attacks).
A Persistent Campaign
The new Cybereason report finds that the Chinese APT groups conducted an “adaptive, persistent and evasive” campaign to obscure activity and maintain persistence on infected systems.
The telecom espionage campaign, like the earlier Hafnium attacks, exploited vulnerabilities in Microsoft Exchange servers to gain access to targeted networks and then proceeded to compromise critical assets – including domain controllers and billing systems with sensitive call detail record data, Cybereason says.
“These attacks compromised telcos primarily in ASEAN countries, but the attacks could be replicated against telcos in other regions,” the security firm says. “While the prevailing assessment is that the operations were intended for espionage purposes only, the fact remains that had the attackers decided to change their objectives from espionage to interference, they would have had the ability to disrupt communications for any of the affected telecoms’ customers.”
Lior Div, CEO and co-founder of Cybereason, notes: “The attacks are very concerning because they undermine the security of critical infrastructure providers and expose the confidential and proprietary information of both public and private organizations that depend on secure communications for conducting business.”
State-sponsored espionage operations “not only negatively impact customers and business partners; they also have the potential to threaten the national security of countries in the region and those who have a vested interest in the region’s stability,” Div adds.
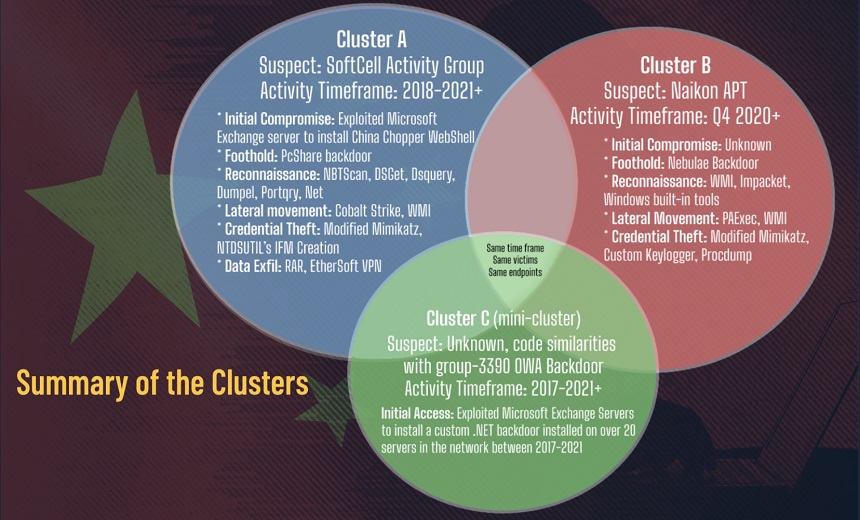
Soft Cell APT
Cybereason attributes one cluster of attacks to Soft Cell, an APT group in operation since 2012 that had previously targeted telecom providers in the same region of Southeast Asia. Telemetry and forensic evidence shows that the naming conventions, tools and TTPs in this cluster are similar to those attributed to Soft Cell in previous research.
Researchers say Soft Cell:
- Exploited Microsoft Exchange servers to install a “China Chopper WebShell”;
- Leveraged a backdoor called PcShare;
- Used various built-in Windows tools for internal and external connectivity checks;
- Harvested credentials using the open-source tool Mimikatz;
- Moved laterally using the adversary simulation software Cobalt Strike;
- Exfiltrated data and compressed/password-protected the data using the WinRAR tool and SoftEther VPN.
Naikon APT
Cybereason attributes another cluster of activity, first observed in late 2020, to the Naikon APT, based on the unique TTPs involved, including tools and command-and-control server infrastructure. Researchers say this APT:
- Used a backdoor called Nebulae, versions of which date back to 2016;
- Deployed a previously undocumented keylogger called “EnrollLogger” on high-profile assets – likely to obtain sensitive information and harvest credentials;
- Used the legitimate Google Chrome Frame to load the Nebulae backdoor payload;
- Used built-in Windows tools for internal and external connectivity checks;
- Used “PAExec” to connect remote servers and the command “net use” in order to access shared network resources;
- Used Windows’ Sysinternals’ ProcDump and Mimikatz to dump credentials from the domain controllers;
- Concealed its “EnrollLogger” with a South Korean multimedia player called “Potplayer,” which has a known hijacking vulnerability.
Threat Group-3390
A third cluster involved deployment of a custom Outlook Web Access backdoor used to harvest credentials, Cybereason reports. Activity dates back to 2017; backdoor deployment continued into this year, including a sharp uptick in March, perhaps in response to Microsoft’s patches for its Exchange Server vulnerabilities.
Code analysis shows similarities with the backdoors “Dllshellexc2007” and “Dllshellexc2010,” discovered by TrendMicro and attributed to Group-3390, or APT27, aka Emissary Panda. For example:
- Its custom “.NET” credential-stealing backdoor was installed on either Microsoft Exchange or Internet Information Services servers and could run arbitrary commands, exfiltrate data and deploy additional tools;
- The backdoor was obfuscated with “.NET Reactor,” a code protection that can hinder analysis.
Last month, the U.S. indicted four Chinese nationals connected to the nation’s Ministry of State Security over an alleged hacking campaign conducted from 2011 to 2018 that targeted universities and government entities to obtain trade secrets, medical research and other intellectual property (see: US Indicts 4 Chinese Nationals for Lengthy Hacking Campaign).





