APT Group Using Backdoor for Espionage
Cybercrime
,
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
Kaspersky Describes ‘Operation TunnelSnake’ That Appears to Have China Connection
An ongoing advanced persistent threat campaign dubbed “Operation TunnelSnake” has been using a Windows rootkit named Moriya to deploy a passive backdoor to spy on victims, the security firm Kaspersky reports.
See Also: Live Webinar | Software Security: Prescriptive vs. Descriptive
Researchers observed the campaign being conducted on public-facing servers within the victim organizations to spy on network traffic and send commands to compromised hosts. The attackers are using privileged implants that are usually deployed as drivers, Kaspersky reports.
The Moriya rootkit was first identified on networks of regional diplomatic organizations in Asia and Africa in October 2019 and May 2020, Kaspersky says. Those infections persisted in the targeted networks for several months, the researchers say.
Kaspersky recently investigated another attack on a victim in South Asia in which the APT group, which is believed to be Chinese-speaking, deployed a tool set for lateral movement along with the rootkit. The researchers say the attackers apparently had a foothold in the victim’s network as early as 2018.
Using a Backdoor
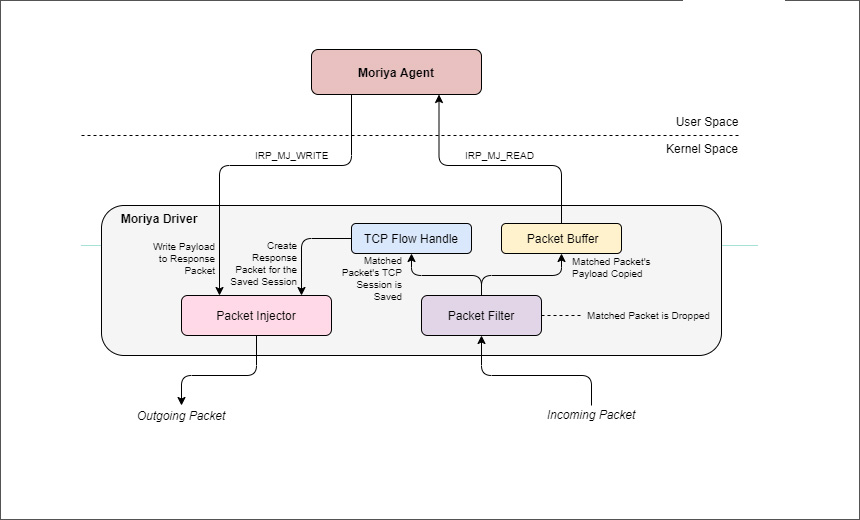
The APT group uses the Moriya rootkit to deploy a passive backdoor that allows attackers to analyze all incoming traffic to the infected machine, researchers say. It further filters out packets that are marked as designated for the malware and responds to them, which ultimately forms a covert channel that allows attackers to issue shell commands and receive back their outputs.
“Moriya is used by an unknown actor to deploy passive backdoors on public-facing servers, facilitating the creation of a covert C2 communication channel through which they can be silently controlled,” says Mark Lechtik, a senior security researcher at Kaspersky’s global research and analysis team.
Natalie Page, threat intelligence analyst at the security firm Talion, says the success of this long-running campaign can likely be attributed to the evasive elements of Moriya, which uses packet inspection taking place in the kernel mode leveraging a Windows driver.
“This allows the attacker to drop packets of interest before they are processed by the network stack, evading detection from security solutions,” Page says. “Furthermore, the way in which the tool waits for incoming traffic rather than initiating a connection to a server itself hinders analysis and makes it hard to trace an attacker’s footprints.”
Security firm Cyware found that the TunnelSnake APT campaign is using some additional tools to attack potential victims. “Cybercriminals evolve and tailor their tool set to maintain a considerable stealth level and infiltrate high-profile target networks,” the firm notes.
Additional Exploits
In addition to Moriya, the TunnelSnake operators have used a user-mode version of the malware – IISSpy – and network discovery tools, including HTTP scanner and DCOM scanner.
“IISSpy is used to target vulnerable IIS servers for establishing a backdoor in organizations’ underlying websites,” Cyware notes. “IISSpy exploits vulnerability CVE-2017-7269 to let the attackers gain an initial foothold on a server before running the malware.”
Kaspersky also found that the developers of Moriya are using malware known as ProcessKiller to eliminate execution of processes with the use of a kernel mode driver. ProcessKiller shuts down and blocks initiation of AV processes from kernel space, thus allowing other attack tools to run without being detected.
Kaspersky’s investigation of an attack in South Asia led to the discovery of the attackers’ methods and tools.
“The toolset includes programs used to scan hosts in the local network, find new targets, perform lateral movement to spread to them and exfiltrate files,” Kaspersky’s Lechtik notes. “While most of the tools seem custom-made and tailored for the attackers’ activities, we could also observe some open-source malware frequently leveraged by Chinese-speaking actors.”
China Link?
The Kaspersky researchers did not attribute the attack to any group, but based on the tactics, techniques and procedures used, they suspect a China connection.
The campaign’s use of tools such as China Chopper, Bouncer, Termite and Earthworm are indicators that the attackers are Chinese-speaking because these have previously been used in campaigns attributed to Chinese-speaking groups, Kaspersky says.
“While some cross-overs have been found in the coding of this tool with APT1, currently no threat group has officially been attributed to Moriya,” says Page of Talion. “A continuous presence of Chinese language throughout the campaign suggests this to be the country of origin, which falls in line with the likelihood that this is also a high-profile group.”