Pingback Malware Uses ICMP to Avoid C&C Detection
Cybersecurity analysts Lloyd Macrohon and Rodel Mendrez have recently inspected a new piece of malware that they’ve encountered during a breach investigation.
Dubbed “Pingback”, the malware uses ICMP (Internet Control Message Protocol) tunneling for its backdoor communications and operates with various modes to escalate the chances of a successful attack.
Pingback (“oci.dll“) achieves its purpose by loading through a legitimate service called MSDTC (Microsoft Distributed Transaction Coordinator) – a component that is responsible for coordinating transactions that span multiple resource managers, by exploiting a method called DLL search order hijacking. The latter involves using a genuine application to preload a malicious DLL file.
As my colleague Vladimir explained in his article on Malicious Apps, every time your computer boots, the OS will start looking for DLLs. If the path to a specific DLL is not hardcoded (i.e., set in stone), a malicious piece of code can be introduced in this search order, which would result in the executable loading it.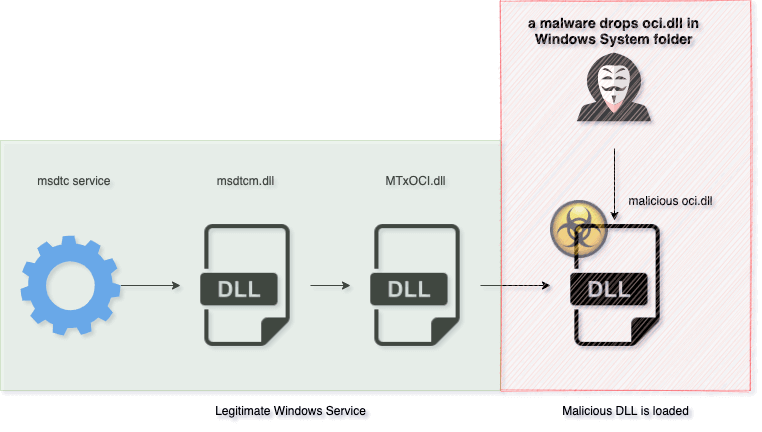
Malicious oci.dll is indirectly loaded by msdtc service
Image Source: Trustwave
After the execution is completed, Pingback uses the ICMP protocol for its main communication. ICMP is a network layer protocol mainly used to communicate with the source of a data packet about transmission issues. For example, if a datagram is not delivered, ICMP might report this back to the host with details to help discern where the transmission went wrong. It’s a protocol that believes in direct communication in the workplace.
Pingback specifically uses the echo (ping) request or type 8 ICMP message. It starts a sniffer for every IP address on the host, spawning a thread to sniff packets on each individual IP address. To distinguish between its own packets and other packets, the sniffer ignores anything else that’s not an ICMP echo packet and does not contain the ICMP sequence number 1234, 1235, or 1236. It also ignores packets not destined for the specified IP address.
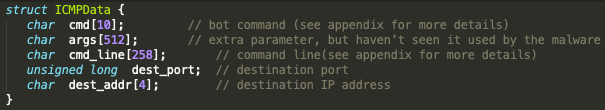
Malware’s ICMP data is represented by this C structure.
Image Source: Trustwave
Some commands that the malware supports include the ability to run arbitrary shell commands, download and upload files from and to the attacker’s host, and execute malicious commands on the compromised machine.
According to the researchers,
ICMP tunneling is not new, but this particular sample piqued our interest as a real-world example of malware using this technique to evade detection. ICMP is useful for diagnostics and performance of IP connections in the real world. It is very useful to have them enabled but must be balanced by real-world threats. While we are not suggesting that ICMP should be disabled, we do suggest putting in place monitoring to help detect such covert communications over ICMP.
Since the malware didn’t make its way into the network via ICMP but instead utilizes ICMP protocol for its main communications, an investigation into Pingback’s initial entry vector is still ongoing.







