Fake Telegram Desktop App Malware Campaign Persists
Application Security & Online Fraud
,
Cybercrime
,
Fraud Management & Cybercrime
Google Ad Leads to Malicious App Disguised as Telegram
Jannis Kirschner, an independent security researcher based in Basel, Switzerland, searched on Sunday for the desktop version of the popular messaging application Telegram.
See Also: Live Webinar | Mitigating the Risks Associated with Remote Work
The second Google result, an advertisement, led him straight to malware disguised as the desktop version of Telegram for Windows. It was convincing enough at first glance that Kirschner says he “almost fell for it myself.”
It’s a common ploy for malware distributors to use the same advertising tools that online merchants use to lure people. Google patrols its advertising ecosystem to stop abuse, but malvertising remains a persistent problem.
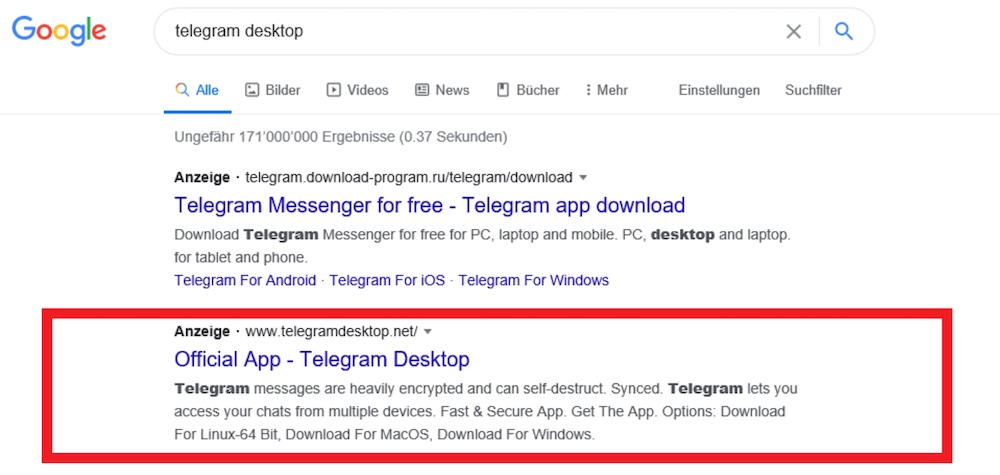
Kirschner, who did a technical write-up on his site, Suid Vulnerability Research, took an in-depth look at the campaign, which involved three domains spoofing Telegram.
Although visiting one of those sites, telegramdesktop[dot]com, now triggers a warning from Google’s Safe Browsing tool as being unsafe, two of the sites are still active and presumably duping others. Those are telegramdesktop[dot]net and telegramdesktop[dot]org. Kirschner has reported the sites to Google.
OpSec Errors
All three spoofed sites are clones of Telegram’s website. All of the links on the cloned sites redirect to Telegram’s legitimate domain, desktop.telegram.com. But one link is swapped out, which is purportedly the executable for the Windows version of Telegram desktop.
Kirschner says that whoever is running the sites made a few operational security mistakes that shed light on how successful the campaign has been. The .com and .net sites have seen 2,746 downloads of the malicious Windows executable, and a second-stage malware was then pushed down 129 times. The .org site snared 529 downloads in just two days, Kirschner says.
Whoever is behind the malware campaign used Bitbucket – a GitHub-like alternative from Atlassian – to host it. The software repository that held the malware was accessible, which allowed Kirschner to see the number of downloads.
“A repo probably was a bad choice for delivering malware since it’s very verbose (download numbers, time and other documents),” Kirschner says. “The biggest opsec mistake was that they didn’t clean one of the repo’s metadata, which led me to discover commit messages and their e-mail [address].”
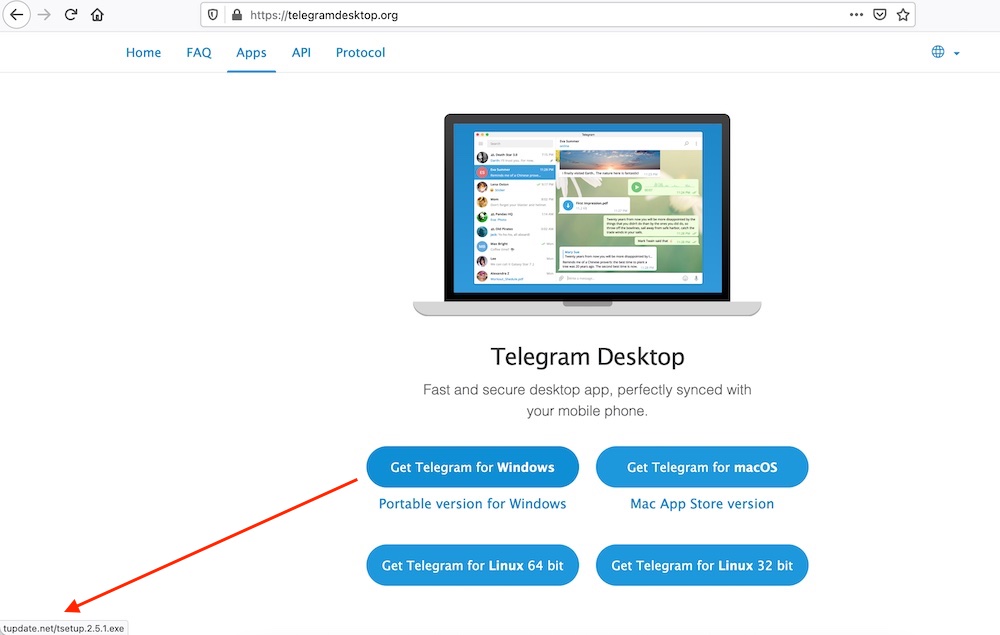
The commits repository lists a user nickname, “TrustVarios,” and an email: “beertmp+dtemn@gmail.com. The same group or person likely set up all of the sites, Kirschner says.
“I believe that it is the same threat actor or group since the TTPs [tactics, techniques and procedures] are the same, and all sites have been established in a very close timeframe using the same hoster and certificate authority,” he says.
Hosting malware on services such as Bitbucket offers at least a temporary advantage: Bitbucket links on the surface are often considered legitimate, and attackers have a window of abuse until someone reports a malicious repository, which then must be removed. The methods help disguise a campaign from technical filtering and manual vetting but don’t necessarily scale well, Kirschner says.
A report from the security firm Cybereason in February 2020 described more than a half-dozen infostealers, cryptominers, ransomware and other malware that bad actors placed on Bitbucket.
“The attackers leverage Bitbucket to easily update payloads and distribute many different types of malware at once,” Cybereason wrote. “In order to evade detection, they have an array of user profiles and continuously update their repositories, at times as often as every hour.”
Information Security Media Group noticed that kind of swapping behavior this week. On telegramdesktop[dot]org, the link to the malicious Windows file switched within two hours on Wednesday morning from being hosted on Bitbucket to another domain, tupdate[dot]net. The latter domain has now been suspended by its hosting provider, and Bitbucket has removed the malicious binaries.
Second Stage: AZORult Infostealer
The telegramdesktop[dot]com site appears to be on a shared hosting service in Moldova. “The web service promotes itself that it takes bitcoin as payment option, so it seems like a great hosting for criminals,” Kirschner writes.
That domain was registered on Dec. 29, 2020, Kirschner says. But a search on the Internet Archive’s Wayback Machine shows that around April 2018 telegramdesktop[dot]com redirected to telegram.org, the legitimate domain. In October 2018, however, the domain expired, according to records from DomainTools.
“I assume that domain once belonged to Telegram themselves, expired and was taken over by the criminals now,” Kirschner says.
The malware hosted on the site, TGInstaller.exe, is a .NET executable. After that gets installed, the second-stage payload is AZORult, which is a common information stealer that appeared about five years ago and was first sold on underground Russian forums, according to the security firm Trend Micro.

“AZORult was being used in malvertising campaigns targeting a popular VPN service, as well as using COVID-19 themed campaigns,” Kirschner writes.
AZORult is designed to pilfer login credentials, cryptocurrency wallets, Telegram messages and many items in Google’s Chrome browser, including cookies, autofill information, passwords and location data.
In February 2020, IBM wrote that AZORult was delivered as part of another malvertising campaign that purported to offer ProtonVPN, the VPN service developed by Proton Technologies, which created ProtonMail.