Attackers Rely on ‘Exotic’ Languages for Malware Creation
Cybercrime
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Blackberry: Newer Programming Languages Help Cybercriminals Evade Detection
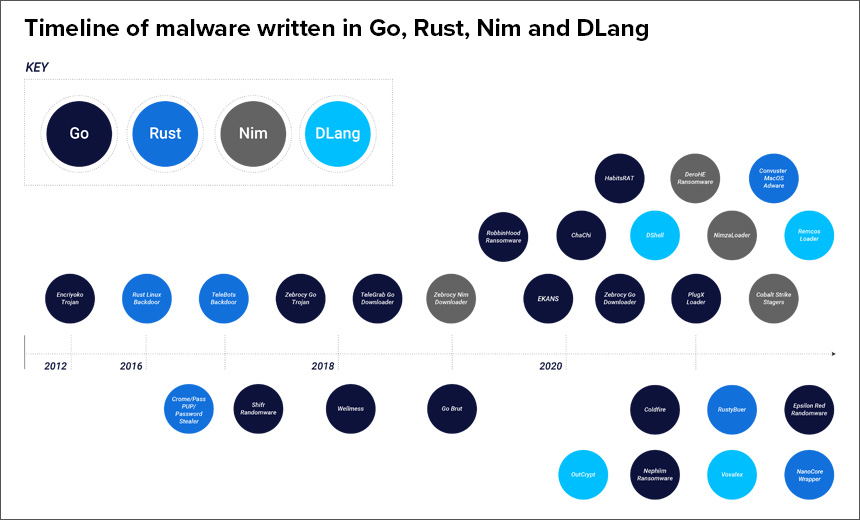
Malware developers increasingly are relying on “exotic” programming languages – such as Go, Rust, DLang and Nim – to create malicious code that can avoid security detection by tools and add a layer of obfuscation to an attack, according to a report released Monday by BlackBerry.
The BlackBerry researchers found malware developers are creating a new array of loaders and droppers using these four languages to deliver or disguise remote access Trojans, or RATs, as well as malicious versions of legitimate tools, such as Cobalt Strike, to potential victims, the report notes.
See Also: Live Webinar | Improve Cloud Threat Detection and Response using the MITRE ATT&CK Framework
In many cases, threat actors are turning to these languages to avoid detection and obscure an attack, according to the report.
“Each of these languages is relatively new and has little in the way of fully supported analysis tooling,” the BlackBerry researchers note. “As such, they can appear quite alien under the hood. It is because of their relative youth and obscurity that the languages themselves can have a similar effect to traditional obfuscation and be used to attempt to bypass conventional security measures and hinder analysis efforts.”
The report also notes: “Older malware written in traditional languages like C++ and C# is actively being given new life with droppers and loaders written in exotic languages. Typically, the older malware will be stored in encrypted form within the first stage, using XOR, RC4, AES or other methods of encryption and encoding.”
Instead of rewriting or recompiling older but still effective malware, attackers are now “wrapping” this malicious code in a dropper or loader written in one of the newer languages, which can then deliver the malware to vulnerable devices or networks while avoiding detection by various security tools, the BlackBerry researchers note.
Four Languages
The report notes that while attacks are increasingly adopting languages such as Rust and DLang, most of the malicious tools that researchers examined were written in Go – an open-source language originally developed by Google and officially released to developers in 2012.
Developers, as well as cybercriminals, have been turning to Go, aka Golang, because of its ease of use, reliability and efficiency, according to the report.
“Go can be cross-compiled to all major operating systems as well as Android, JavaScript and WebAssembly,” the researchers note. “Software engineers and malware authors alike flocked to this language, not only for stylistic reasons. Google backing the project has also increased its popularity as well as the number of libraries that have been made available.”
Malware developed using Go includes ElectroRAT, a RAT designed to steal cryptocurrency from digital wallets, and Ekans, or Snake, a type of ransomware that can attack IT networks as well as industrial control systems, according to researchers.
A ransomware group called Mespinoza has used Go to create a RAT called ChaChi that it uses to deliver other malware. This RAT has targeted government agencies, healthcare organizations and educational institutions over the last year (see: How Mespinoza Ransomware Group Hits Targets).
Other Uses
Other groups have also used the newer programming languages as part of an effort to better hide their attacks.
For instance, a threat group known as TA800 has used the Nim language to create a loader called NimzaLoader, which is typically delivered to victims in a phishing email that contains a malicious attachment, the report notes.
Once installed, NimzaLoader connects to a command-and-control server and then attempts to deliver secondary malware such as Cobalt Strike.
“Nim can be cross-compiled for all major operating systems such as Windows, Linux, BSD and macOS,” the researchers report. “These binaries can be statically or dynamically linked, depending on customization at the time of compilation. Nim also can produce JavaScript code, allowing for coalesced client and server development.”
Why New Languages?
Over the years, attackers have moved away from older programming languages such as VB6 and Delphi, and shifted to newer ones, the report notes.
Cybercriminals and other attackers tend to migrate toward languages that are easy to use and fit in with the type of systems that they are targeting, says Simon Moffatt, founder and analyst at research and advisory firm The Cyber Hut.
“If the intended attack target is a microservices ecosystem with plenty of extensions written in Go language, it makes sense to leverage the same language as the vehicle for an attack,” Moffatt says. “Many newer languages are also able to generate self-contained executables that are small, lightweight and often easy to distribute.”
Older languages are also difficult to use and require add-ins and modifications to work with modern systems, which can make creating malware in these languages difficult, says Chase Cunningham, a retired U.S. Navy chief cryptologist who is now the chief strategy officer at software firm Ericom.
Attackers can more speedily develop and apply malware with newer programming languages, Cunningham notes.