Joker Malware Targets More Android Devices
Application Security
,
Endpoint Security
,
Next-Generation Technologies & Secure Development
Trojan Spreads Through Malicious Apps in Huawei App Store
Joker malware has targeted more than 500,000 Android devices across the world through malicious apps in AppGallery, the official app store of Huawei, according to the security firm Doctor Web.
See Also: Live Webinar | Empowering Financial Services with a Secure Data Path From Endpoint to Cloud
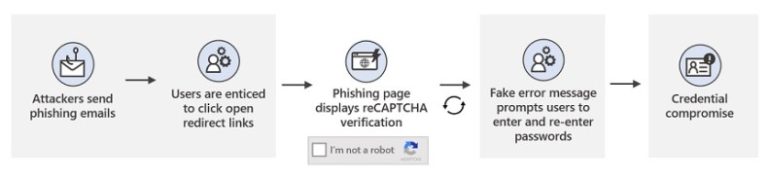
The Android Trojan, active since 2017, is capable of stealing SMS messages, contact lists and device information from infected smartphones, Doctor Web says. Attackers have used the malware in several campaigns (see: Updated Joker Android Malware Adds Evasion Techniques).
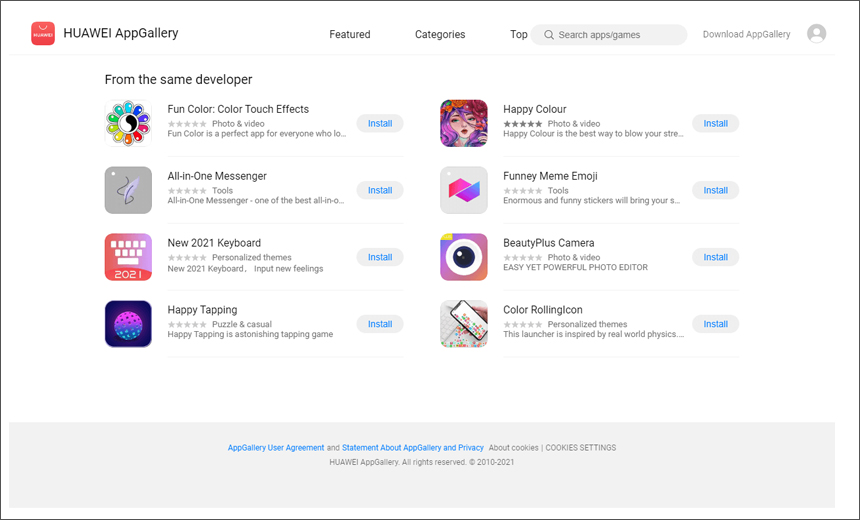
The malicious apps offered in Huawei’s AppGallery are a fully functioning virtual keyboard, a camera app, a launcher, an online messenger, a sticker collection, coloring programs and a game, Doctor Web notes. Victims who use them are unaware of background malicious activity.
The malicious Joker apps have been downloaded 538,000 times. Once installed on an Android device, the attackers use the malware to subscribe the device to up to 10 premium mobile services at a time. The attacker, who owns the overseas “premium service” to which the victim unknowingly subscribed, then receives mobile service fees paid for via the victim’s phone bill.
Attack Tactics
Once a malicious app has been installed, when a user interacts with it, the Trojan connects to the attackers’ command-and-control server and downloads additional components. The downloaded components then automatically subscribe the Android device user to premium mobile services.
“The downloaded Trojan module is detected by Dr. Web as Android.Joker.242.origin,” the security firm notes. “The same virus record successfully detects other similar modules downloaded by all 10 new malware modifications. Moreover, the same modules were used by some other versions of the Android.Joker, which were spread, among other places, on Google Play, for example, by apps such as Shape Your Body Magical Pro, PIX Photo Motion Maker, and others.”
The malicious Joker apps can intercept SMS messages notifications to subscribe to more mobile services. “By default, the limit is set to 5, but it can be increased or decreased upon receiving the configuration from the C&C server. For example, in the configurations our specialists intercepted, the number reached 10,” the report adds.
After being alerted to the malicious apps by Doctor Web, Huawei reported to the firm that it has hidden them to protect users.
Similar Campaigns
In September 2020, the Joker malware was found to be targeting Android users via malicious apps in Google Play as well as third-party app stores (see: Fresh Joker Malware Variant Targeting Android Users).
Other malware has also been targeting Android users. For example, over the past five years, a sophisticated spyware campaign dubbed PhantomLance has been targeting Android users through Trojan-laced apps in the Google Play Store that are disguised as various plug-ins, browser cleaners and application updaters, according to a report Kaspersky published in April (see: Spyware Campaign Leverages Apps in Google Play Store).
In July 2020, Malwarebytes reported fraudsters were able to insert a Trojan called Cerberus into the Google Play Store by hiding it within a money converter app to target Android devices (see: Cerberus Banking Trojan Targeted Spanish Android Users).