What’s Next Step for REvil Ransomware Victims?
Business Continuity Management / Disaster Recovery
,
Fraud Management & Cybercrime
,
Governance & Risk Management
If Backups Unavailable, Victims Should Retain Encrypted Files in Case Decryptor Released
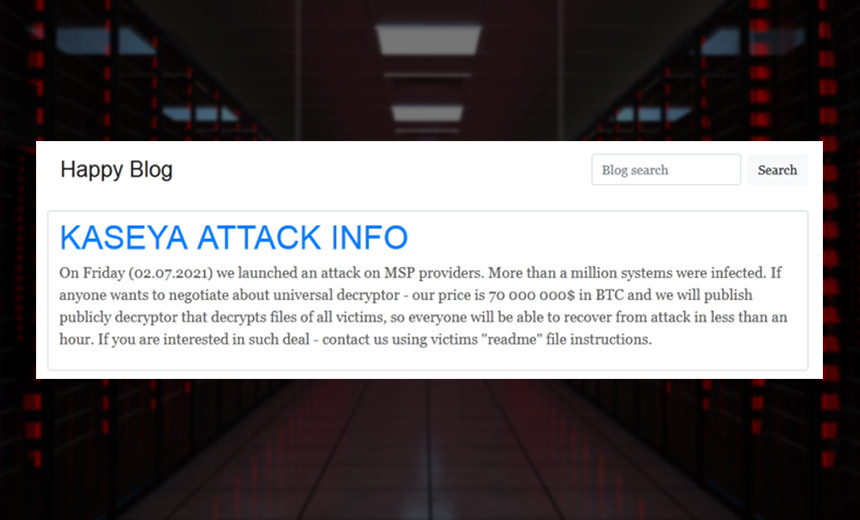
Some ransomware gangs that have shut down operations have offered decryption keys to their victims. But when the REvil, aka Sodinokibi, ransomware gang disappeared from online on Tuesday, no such offer was made. In fact, it’s not clear whether REvil shut down on its own or was forced down by government action.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
Now, victims that lack adequate data backups are in a precarious situation.
“Unless REvil chooses to release their master keys or the keys were seized by law enforcement, it’s quite likely that some victims will permanently lose access to their data,” says Brett Callow, a threat analyst with the security firm Emsisoft. “Unless they had working backups, the victims have no way of recovering.”
That’s why many experts are advising victims who cannot rely on backups to save encrypted data in case a decryptor becomes available at some point.
REvil went offline at about 1 a.m. EDT on Tuesday, leaving security experts wondering why. Possible causes are law enforcement action, an internal struggle within the gang or a technical issue.
Tom Robinson, CEO of the blockchain analysis firm Elliptic, notes there has been no activity on any of REvil’s known bitcoin wallets since Tuesday, indicating that victims likely cannot pay a ransom to receive a decryptor key.
REvil, which appears to be based in or near Russia, has been tied to several recent high-profile ransomware attacks, including the July 2 attack against software firm Kaseya, which targeted its on-premises Virtual System Administrator, leading to ransomware attacks on about 60 of its managed service provider customers and up to 1,500 of their clients. It was also tied to the June attack against the meat processing company JBS.
Waiting for a Key
“It can be very frustrating if you are a victim of a [REvil] attack and are now left with no options to recover encrypted data,” says ransomware incident response firm Coveware. “Hopefully, the REvil group releases a master key if they truly are retired, or a law enforcement agency is able to recover a master key in the future so that victims can recover their data.”
One security professional, Kevin Beaumont, head of the security operations center for Arcadia Group, asked on Twitter for REvil or one of its affiliates to forward encryption keys to him so he could pass them on to the victims.
If somebody pings me decryption keys for REvil wrt to Kaseya, to kevin.beaumont@gmail.com, I will get them out there (by giving them to somebody smart, I’m thick). https://t.co/qAg4n6QQnt
— Kevin Beaumont (@GossiTheDog) July 15, 2021
The exact number of victims of REvil’s supply chain attack on Kaseya remains unknown. But the MSP JustTech, which is a Kaseya customer, says it, and in turn, hundreds of its customers, were affected. Municipalities, companies and schools from around the world have also reported being attacked by REvil through Kaseya.
Recovery Options
For companies whose systems are infected by REvil ransomware, containing the malware is the first step, says Mark Lance, senior director of cyber defense at the incident response and cybersecurity firm GuidePoint Security.
“You have to get it to a state where you can start getting your systems back up operationally – whether that’s recovering from backups, restoring from an older version or snapshot of the system or rebuilding a system. You have to make sure that it’s being done in a manner that’s segmented and that has an EDR solution on it,” Lance says.
Victims without backups should still save their encrypted data just in case a decryption key is eventually released, says Devon Ackerman, managing director and head of incident response for North America for the incident response firm Kroll.
“We’d recommend companies make backups of critical systems in total, even full VMs, in their encrypted format, following adequate forensics process to avoid further corruption,” Ackerman says. “Keep the backups safe until such time that a public decryptor may be developed or the threat actor resurfaces. Without a decryptor, the organization is forced to essentially start rebuilding their systems from their last safe backup or from scratch, if no backups are available.”
Backups Save the Day
For Kaseya customer JustTech, backups proved to be extremely valuable after a July 2 REvil ransomware attack.
Joshua Justice, founder, owner and president of JustTech, tells Information Security Media Group that several hundred of its 3,000-plus clients were affected by the attack, but almost all of them are now operating normally.
“We have encrypted backups of our clients’ data and have almost finished restoring this data,” Justice says. “We wiped the workstations, deleted the encrypted files and restored the backups.”
Justice offered a timeline on the REvil attack and JustTech’s response.
The company believes the attack began at 12:31 p.m. EDT on July 2. Once the breach was discovered, the company disabled and shut down the affected servers within eight minutes and then told its customers to shut down all servers, laptops and desktops.
On July 4 and July 5, JustTech sent affected clients a list of all computers and laptops that it believed were infected. Then, the full recovery effort began, and that effort is now nearly complete.
Closing Shop
Those involved in the REvil gang have a track record of abandoning their victims.
REvil’s previous incarnation as the ransomware gang GandCrab announced in May 2019 that it would be shutting down in 20 days, the security firm CrowdStrike notes.
The gang made it known that any victim who did not pay up would lose their data forever, although some decryptors for earlier versions of GandCrab ransomware had been released by police, Europol says.
Another ransomware gang, DarkSide, recently announced it was shutting down its ransomware-as-a-service operation after having part of its infrastructure apparently taken down by law enforcement officials following its attack on Colonial Pipeline Co. DarkSide said it was making decryptor keys available to its affiliates to share with victims.
And in June, the ransomware gang Avaddon called it quits, citing pressure from law enforcement agencies; it also released its decryptor keys.
The ransomware groups Maze, Ziggy and Fonix also announced that they had abandoned their activity over the last year.