U.S. Declares Emergency in 17 States Over Fuel Pipeline Cyber Attack
The ransomware attack against Colonial Pipeline’s networks has prompted the U.S. Federal Motor Carrier Safety Administration (FMCSA) to issue a regional emergency declaration in 17 states and the District of Columbia (D.C.).
The declaration provides a temporary exemption to Parts 390 through 399 of the Federal Motor Carrier Safety Regulations (FMCSRs), allowing alternate transportation of gasoline, diesel, and refined petroleum products to address supply shortages stemming from the attack.
“Such [an] emergency is in response to the unanticipated shutdown of the Colonial pipeline system due to network issues that affect the supply of gasoline, diesel, jet fuel, and other refined petroleum products throughout the Affected States,” the directive said. “This Declaration addresses the emergency conditions creating a need for immediate transportation of gasoline, diesel, jet fuel, and other refined petroleum products and provides necessary relief.”
The states and jurisdictions affected by the pipeline shut down and included in the Emergency Declaration are Alabama, Arkansas, District of Columbia, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas, and Virginia.
The exemptions, which aim to alleviate any shortages or supply disruptions that may arise due to the shutdown, are expected to be in effect until the end of the emergency or June 8, 2021, 11:59 p.m., whichever is earlier.
FBI Confirms DarkSide Ransomware
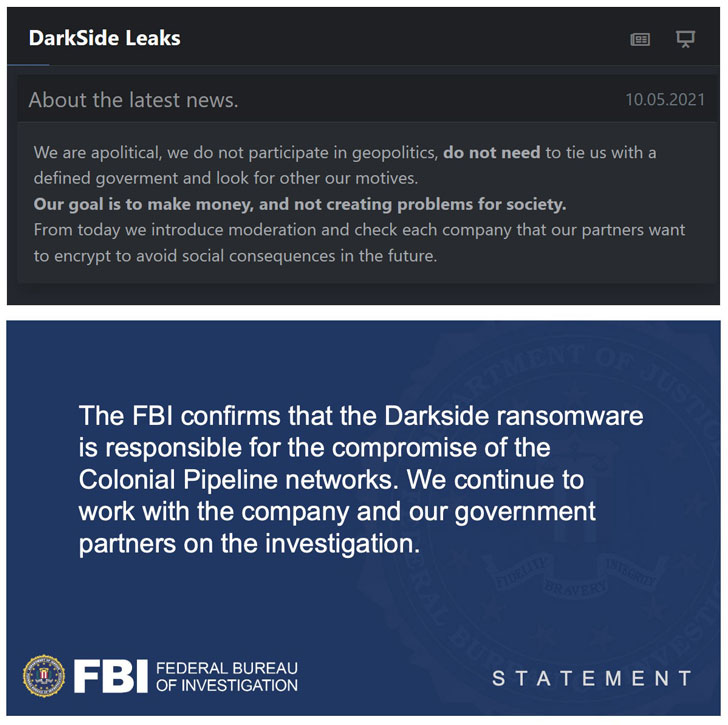
The development comes as the U.S. Federal Bureau of Investigation (FBI) confirmed the disruption of one of the country’s largest pipelines over the weekend was orchestrated by Darkside ransomware. The cyberattack forced the company to shut down 5,500 miles of fuel pipeline from the Texas city of Houston to New York harbor, raising concerns about the vulnerability of the U.S. energy infrastructure to cyberattacks.
“Colonial Pipeline is continuing to work in partnership with third-party cybersecurity experts, law enforcement, and other federal agencies to restore pipeline operations quickly and safely,” Colonial Pipeline said in a statement. “While this situation remains fluid and continues to evolve, the Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach.”
While the U.S. government on Monday said there was no evidence to imply that Russia was involved in the Colonial Pipeline ransomware attack, the operators of the DarkSide ransomware issued a statement on their dark web extortion site, pledging it intends to vet the companies its affiliates are targeting going forward to “avoid social consequences in the future.”
“We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives,” the cybercrime gang said, adding, “Our goal is to make money, and not creating problems for society.”
DarkSide as Carbon Spider’s Ransomware campaign
The adversary, which is alleged to have leaked data pertaining to at least 91 organizations since commencing operations in August 2020, functions as a ransomware-as-a-service (RaaS) scheme, in which partners are roped in to expand the criminal enterprise by breaching corporate networks and deploying the ransomware, while the core developers take charge of maintaining the malware and payment infrastructure. Affiliates typically receive 60% to 70% of the proceeds, and the developers earn the rest.
Among the victims whose internal data was published on the DarkSide’s data leak site are other oil and gas companies such as Forbes Energy Services and Gyrodata, both of which are based in Texas. According to Crowdstrike, DarkSide is believed to be the handiwork of Carbon Spider (aka Anunak, Carbanak, or FIN7), whose high-level manager and systems administrator was recently sentenced to 10 years in prison in the U.S.
“The DarkSide group is a relatively new player in the game of ransomware. Despite being a new group, though, the DarkSide team has already built itself quite a reputation for making their operations more professional and organized,” Cybereason researchers said last month. “The group has a phone number and even a help desk to facilitate negotiations with victims, and they are making a great effort at collecting information about their victims – not just technical information about their environment, but more general information about the company itself, like the organization’s size and estimated revenue.”
DarkSide’s pattern of issuing corporate-style press releases on their Tor domain to inject a veneer of professionalism into its criminal activities has led cybersecurity firm Digital Shadows to label its business model as a “ransomware-as-a-corporation” (RaaC).
The Colonial Pipeline incident is the latest cyberattack to confront the U.S. government in recent months, following the SolarWinds hacks by Russian intelligence operatives and the exploitation of Microsoft Exchange Server vulnerabilities by Chinese threat actors.
“To take down extensive operations like the Colonial pipeline reveals a sophisticated and well-designed cyberattack,” Check Point’s Head of Threat Intelligence, Lotem Finkelsteen, said. “This attack also requires a proper time frame to allow lateral movement and data exhilaration. The Darkside is known to be part of a trend of ransomware attacks that involve systems the cyber community rarely sees involved in the compromised network, like ESXi servers. This leads to suspicions that ICS network (critical infrastructure systems) were involved.”