Travis CI Flaw Exposed Secrets From Public Repositories
Access Management
,
DevSecOps
,
Identity & Access Management
Critics Say Travis CI’s Security Bulletin is Insufficient

Travis CI, a Berlin-based continuous integration vendor, has patched a serious flaw that exposed signing keys, API keys and access credentials, putting thousands of organizations potentially at risk.
See Also: The 10 Essential Capabilities of a Best-of-Breed SOAR
The company is coming under criticism for not describing in more detail the security issue given the potential impacts.
“Anyone could exfiltrate these [secrets] and gain lateral movement into 1000s of orgs,” tweets Peter Szilagyi, who is the team lead for the Ethereum cryptocurrency project.
Travis CI has patched the flaw, which is tracked as CVE-2021-41077. It has advised that organizations should change their secrets immediately.
The vulnerability, which was discovered by Felix Lange, was reported to Travis CI on Sept. 7, Szilagyi tweeted. Travis CI says it began patching the issue on Sept. 3, which would indicate it had picked up on the problem before it was notified, but the timeline isn’t clear.
Continuous integration testing is the process by which developers ensure their software builds will work across different system environments. As of 2018, some 900,000 open-source projects were using Travis CI, according to this academic paper on continuous integration.
Travis CI officials couldn’t be immediately reached for comment.
Pulling Secrets
The effects of the vulnerability meant that if a public repository was forked, someone could file a pull request and then get access to the secrets attached to the original public repository, according to Travis CI’s explanation.
Travis CI’s documentation says that secrets shouldn’t be available to external pull requests, says Patrick Dwyer, an Australian software developer who works with the Open Web Application Security Project, known as OWASP.
“They [Travis CI] must have introduced a bug and made those secrets available,” Dwyer says.
Travis CI’s flaw representes a supply-chain risk for software developers and any organization using software from projects that use Travis CI, says Geoffrey Huntley, an Australian software and DevOps engineer.
“For a CI provider, leaking secrets is up there with leaking the source code as one of the worst things you never want to do,” Huntley says.
Security Bulletin Fail
Travis CI has issued a security bulletin, but some are criticizing the company that it’s insufficient given the gravity of the vulnerability. Szilagyi alleges in a tweet that Travis CI underplayed the issue and silently patched it.
After 3 days of pressure from multiple projects, @travisci silently patched the issue on the 10th.
No analysis, no security report, no post mortem, not warning any of their users that their secrets might have been stolen. 3/4
— Péter Szilágyi (karalabe.eth) (@peter_szilagyi) September 14, 2021
Travis CI mentions the vulnerability in two places on its websites. The first is on its blog under a headline Security Bulletin that has just two sentences: “As a reminder from the Support Team, cycling your secrets is something that all users should do on a regular basis per your company’s security process. If you are unsure how to do this please contact support and we would be happy to help you.”
There’s also another post in its Community Forums that gives a bit more detail.
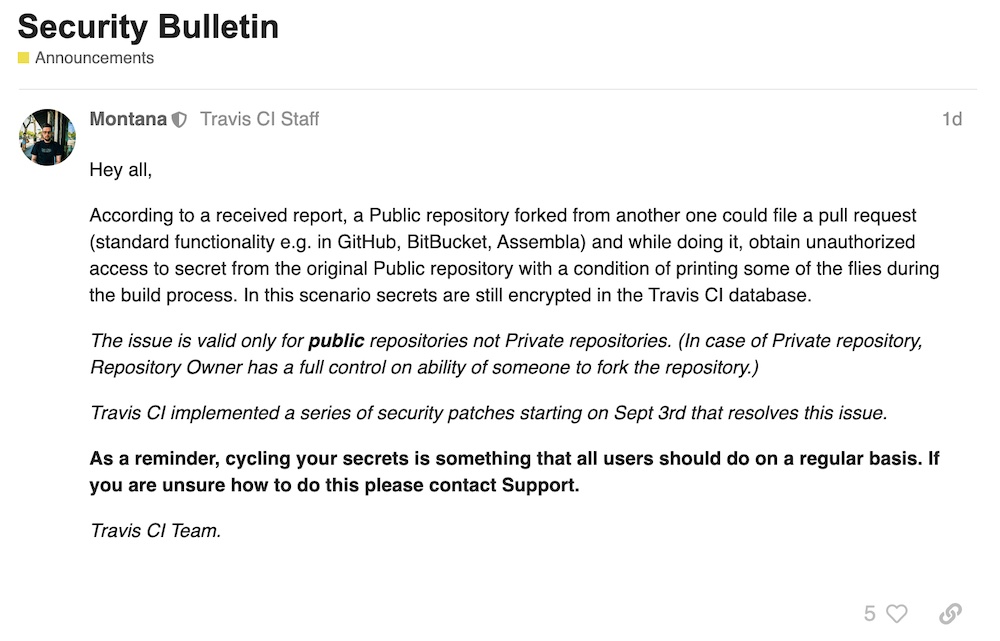
But Travis CI doesn’t appear to have warned organizations how they can detect if their secrets were stolen.
Dwyer says organizations could review their recent pull requests and see if there were ones that might look suspicious. But the sparse notification from Travis CI doesn’t give a lot of guidance to go on, Dwyer says.
“The problem with this sort of thing is you can probably tell after the event when you go to review the pull request, go, ‘What have they done here? Like this looks dodgy’.” Dwyer says. “But you find that out after they’ve already popped your creds.”
Sean Wright, lead application security SME at Immersive Labs, says Travis CI should perform an audit to identify who was affected by this vulnerability and inform those organizations.
“Unfortunately, many of those affected likely don’t have any idea,” Wright says. “Anyone who has a public repository on Travis CI should change their secrets immediately, and perform any additional actions such as certificate revocation for existing secrets.”
Travis CI was acquired by a company called Idera in January 2019. Shortly afterwards, it appears Travis CI began laying off some employees, and a crowdsourced effort on Twitter under the hashtag #TravisAlums sought to help those affected with other jobs.






