The White House Is Deciding Whether to Support a Bureau of Cyber Statistics
The White House Is Deciding Whether to Support a Bureau of Cyber Statistics


Top U.S. and Chinese officials offered sharply different views of each other and the world as the two sides met face-to-face for the first time since President Joe Biden took office. In unusually pointed public remarks for a staid diplomatic meeting, Secretary of State Antony Blinken and Chinese Communist Party foreign affairs chief Yang Jiechi…

Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Experts Warn of Continued Scrutiny in Cryptocurrency Markets Dan Gunderman (dangun127) • September 3, 2021 The U.S. Securities and Exchange Commission this week announced civil action against defunct cryptocurrency lending platform BitConnect; its founder, Satish Kumbhani; and its top U.S. promoter, Glenn…

A grand jury has indicted a California resident accused of stealing Shopify customer data on over a hundred merchants, TechCrunch has learned. The indictment charges Tassilo Heinrich with aggravated identity theft and conspiracy to commit wire fraud by allegedly working with two Shopify customer support agents to steal merchant and customer data from Shopify customers…
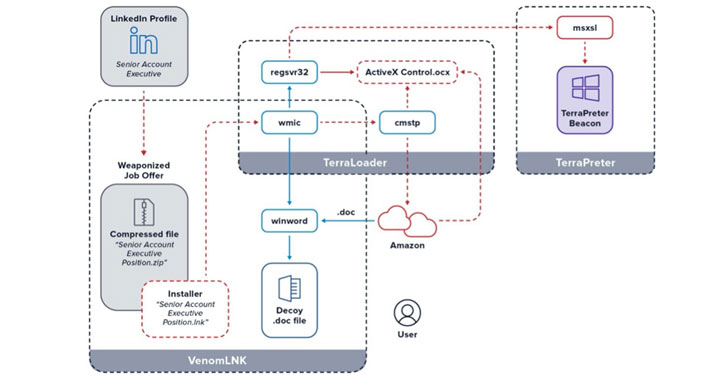
A new spear-phishing campaign is targeting professionals on LinkedIn with weaponized job offers in an attempt to infect targets with a sophisticated backdoor trojan called “more_eggs.” To increase the odds of success, the phishing lures take advantage of malicious ZIP archive files that have the same name as that of the victims’ job titles taken…

After examining 23 Android applications, mobile app developers potentially exposed personal data of over 100 million users through a variety of misconfigurations of third-party cloud services, a report said on Thursday. According to Check Point Research (CPR), it recently discovered that in the last few months, many application developers have left their data and millions…

Critical Infrastructure Security , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks Cybereason’s Sam Curry on DarkSide and New Breed of Ransomware Attack Tom Field (SecurityEditor) • May 12, 2021 Sam Curry, CSO, Cybereason In April, Cybereason published a blog describing its research into the DarkSide ransomware strain that infected…