StrRAT Masquerades as Ransomware – InfoRiskToday
Cybercrime
,
Fraud Management & Cybercrime
,
Social Engineering
Microsoft Says Spam Campaign Uses Updated Variant
Microsoft is warning about a spam campaign that uses an updated variant of Java-based StrRAT malware that steals confidential data while disguising itself as a ransomware infection even though it does not actually encrypt data.
“This remote access Trojan is infamous for its ransomware-like behavior of appending the file name extension .crimson to files without actually encrypting them,” Microsoft’s Security Intelligence Team said in a series of tweets on Thursday. The name extension prevents users from opening the file with a double click, enabling the attackers to go for a quick and easy extortion attempt, but Microsoft notes that users can remove the extension to recover their files.
Attack Technique
The spam campaign uses social engineering to lure victims into clicking on malicious links.
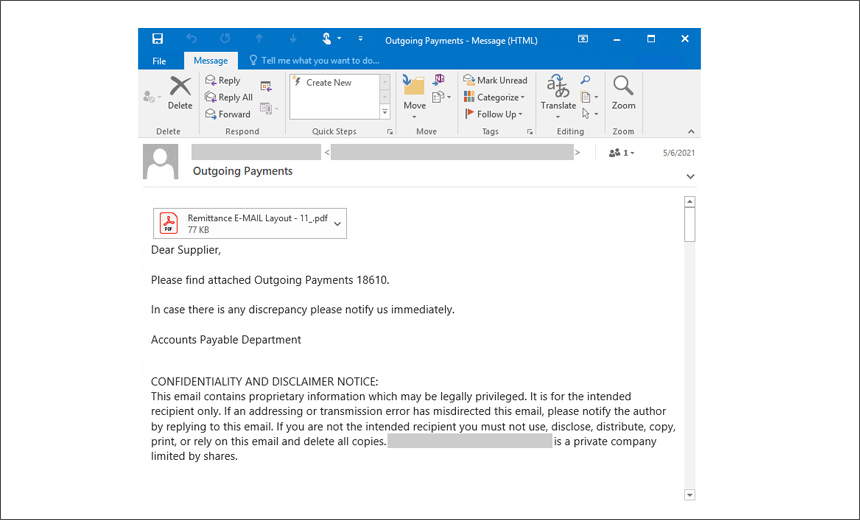
The emails sent from compromised accounts display a PDF attachment with “Outgoing Payments” as the subject line. If it is clicked, instead of opening a PDF, it downloads the StrRAT malware, which connects to the attackers’ command-and-control sever.
StrRAT can steal browser credentials, log keystrokes and take remote control of an infected system.
StrRAT Malware
The Java-based StrRAT malware was first spotted in June 2020 by researchers at German cybersecurity firm G Data CyberDefense AG. The malware, version 1.2, infected Windows devices via email campaigns pushing malicious JAR (or Java archives) attachments, which delivered the final RAT payload after going through two stages of VBScript scripts.
“Version 1.5 [of StrRAT] is notably more obfuscated and modular than previous versions, but the backdoor functions mostly remain the same: collect browser passwords, run remote commands and PowerShell, log keystrokes, among others,” Microsoft notes.
Karsten Hahn, malware analyst at G Data, says the remote access Trojan focuses on stealing credentials of browsers and email clients, including passwords via keylogging.
“It supports browsers and email clients like Firefox, Internet Explorer, Chrome, Foxmail, Outlook and Thunderbird. StrRAT malware also allows installation of RDPWrap,” Hahn notes.
RDPWrap is an open-source tool that enables Remote Desktop Host support on Windows.
Ransomware Feature
Hahn had previously documented the ransomware components as rw-encrypt for “encrypting” files, rw-decrypt for “decrypting” files and show-msg for displaying the ransom note.
The so called “encryption” only renames files by appending the .crimson extension and does not actually encrypt. “This might still work for extortion because such files cannot be opened by double-clicking. Windows associates the correct program to open files via their extension. If the extension is removed, the files can be opened as usual,” Hahn notes.
Remote Access Trojans
Unlike this campaign, many other RAT attacks actually involve encrypting data.
For example, Microsoft Security Intelligence reported a recent ransomware campaign that was targeting aviation companies, using malicious documents that deliver information-stealing RevengeRAT malware (see: Spear-Phishing Campaign Targets Aviation Sector).
RevengeRAT, also known as Revetrat, was linked to a sophisticated Crypter-as-a-Service campaign that delivered the malware as part of a phishing campaign, according to the security firm Morphisec.
In April, security firm Cisco Talos uncovered a phishing campaign that targeted users with Bloomberg BNA-based email messages starting in at least March 2020.
AsyncRAT is an open-source RAT that’s designed to remotely monitor and control other computers. The malware is equipped with a keylogger, screen viewer and command execution capabilities. In January, security firm ESET uncovered a hacking campaign using AsyncRAT that targeted private and government entities in Colombia for cyberespionage.
A December 2020 report by security firm Intel 471 revealed that Chinese underground markets were selling AsyncRAT and other RATs.