REvil Decryption Key Posted on Cybercrime Forum
Endpoint Security
,
Fraud Management & Cybercrime
,
Ransomware
But the Key Appears to Only Unlock Files Encrypted in the Kaseya Attack
There’s yet another twist in the saga around REvil, the prolific but now-defunct ransomware group.
See Also: Live Panel | How Organizations Should Think About Zero Trust
Security analysts are testing a decryption key linked to by a user on the Russian-language cybercrime forum XSS on Friday. Experts say the key decrypts REvil’s ransomware used in the attack on July 2 against Miami-based software developer Kaseya.
Kaseya develops remote monitoring and management software that’s used by managed service providers. In late July, Kaseya acquired a decryptor from a source that would unlock files encrypted by the REvil attack.
Kaseya did not disclose the source for the key and said it did not pay a ransom. It initially expressed in a now-edited blog post that the acquisition came “unexpectedly” (see Kaseya Obtains Decryption Tool After REvil Ransomware Hit).
It’s unclear if what was released on Friday is what Kaseya has been distributing to victims under a nondisclosure agreement. A Kaseya spokesperson said late Tuesday that the company has no comment.
It’s possible that one of the recipients of that key who was under a NDA posted it on XSS in order to try to avoid legal repercussions.
The REvil ransomware ended up infecting up to 60 of Kaseya’s managed service provider customers and up to 1,500 of those businesses’ customers. The point of entry was a zero-day authentication vulnerability in the on-premises version of Virtual Service Administrator, or VSA, which is Kaseya’s remote IT management software.
Not Terribly Useful
Others claim that the key may be the elusive “operator” key – a decryption key that unlocks files from all REvil ransomware variants. But it is looking increasingly unlikely that is accurate.
In either case, the key may not be terribly useful to anyone at this point, says Allan Liska, an intelligence analyst with Recorded Future’s computer security incident response team.
“At this point, most REvil victims have already gone down the path of recovery,” Liska says.
One reason: Downstream victims of the attack against Kaseya have been able to get access to a decryptor after it was passed to the company. Kaseya worked with Emsisoft, a security vendor, to verify the decryptor and ensure that it worked without exposing victims to further risk.
After the attack against Kaseya, REvil’s infrastructure went offline although it is unclear why. REvil’s disappearance coincided with increasingly aggressive calls by the U.S. that Russia needed to do more about cybercriminals that may be within its borders (see REvil’s Infrastructure Goes Offline).
‘Good Luck’
The key was posted on the XSS forum by someone going by the nickname Ekranoplan. The person’s account was only created on Aug. 4.
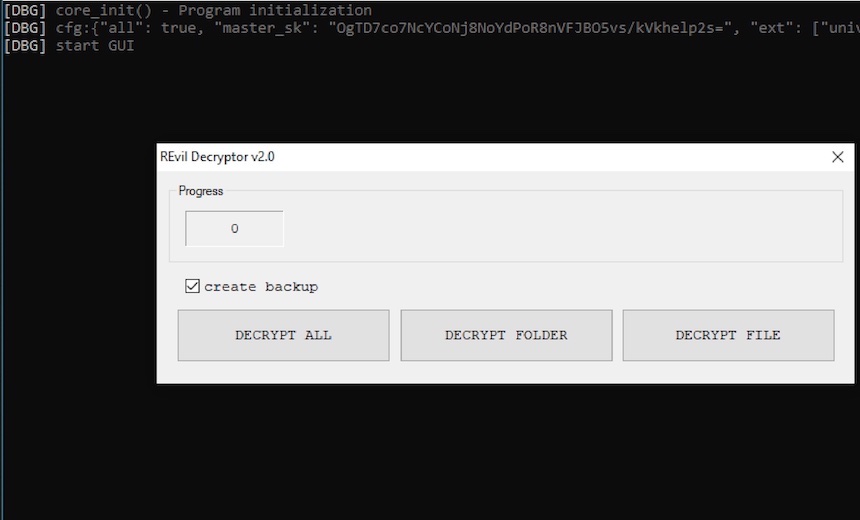
The person wrote in Russian: “If someone needs a REvil decryptor key, I put it here. Good luck” and then included this link to GitHub. The GitHub link contains screenshot that includes a string that is the decryption key. It is labelled “master_sk.”
REvil’s ransomware used four sets of cryptographic keys, as explained in a tweet thread in early July by Fabian Wosar, Emsisoft’s CTO.
In general, there are four types of public and private key pairs involved with REvil: There is an operator key pair, with the public part of it being hardcoded into every single REvil sample we have ever seen.
— Fabian Wosar (@fwosar) July 3, 2021
The master_sk key is also known as a “campaign” key, or a key that is used for a specific campaign against a specific entity. Or to put it another way, it’s different for every victim. So if the screenshot posted on GitHub has an accurate label, this would appear to be just the decryption key for Kaseya victims.
There’s also what Emsisoft calls an “operator” key. REvil samples have a public operator key coded into every sample. It is believed that the private operator key could decrypt all REvil variants. But Wosar tweets that those types of keys have been tightly held, and his company has never seen one. He later tweeted what was released is not the operator key.
The REvil hardcoded operator public key is 79CD20FCE73EE1B81A433812C156281A04C92255E0D708BB9F0B1F1CB9130635. The leaked key generates public key F7F020C8BBD612F8966EFB9AC91DA4D10D78D1EF4B649E61C2B9ADA3FCC2C853. Therefore, the leaked key is not the operator private key.
— Fabian Wosar (@fwosar) August 11, 2021
A couple of users on the XSS forum claim to have been able to use what was released to unlock files encrypted by other REvil variants. Also, in a second posting, Ekranoplan writes that the key “was provided to us by our parent company and is supposed to work for all REvil victims, not just us.”
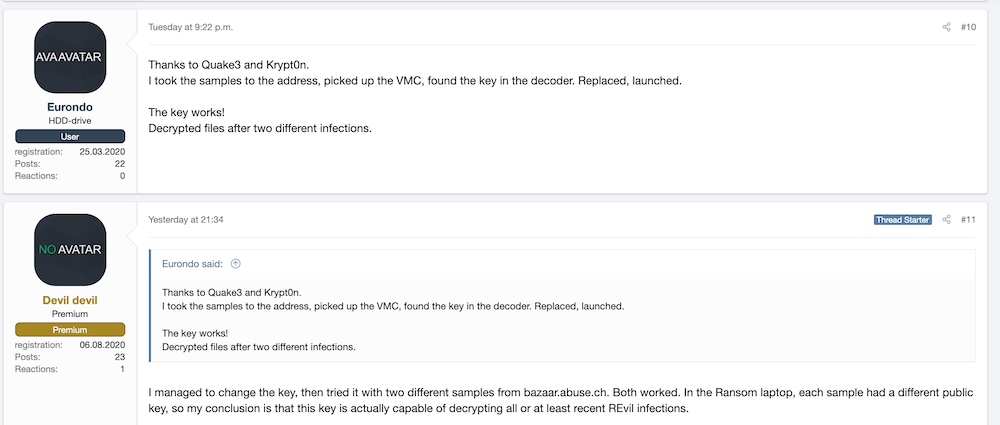
Also, the threat intelligence firm Flashpoint says in a blog post that the key may be a “master” but doesn’t mention Kaseya. But it did say it ran successful tests with recent REvil samples.
“Flashpoint patched the decryptor binary with the annotated key from the thread, and successfully decrypted a sandbox infected with the new REvil test sample, upon changing the file extensions to “universal_tool_xxx_yyy” as seen in the screenshot,” the company writes. “The files were properly decrypted once the file extensions were renamed.”






